Table of Contents
- Updated on 2022-12-30
- More highlights from the past 24 hours
- Updated on 2022-12-29
- More highlights from the past 24 hours
- Rubic crypto-heist
- 49ers CLA
- TikTok spied on journalists
- AT&T legal shenanigans
- Microsoft fined
- International Counter Ransomware Task Force
- DOD cyber skill exodus
- ShinyHunters extradition
- Robin Hood stuff
- New spyware vendor
- PureLogs campaigns
- Shlayer
- NK crypto-heists
- North Korean APT campaigns targeting NFT users
- Albanian government attacks
- APT-C-36 (Blind Eagle)
- APT-Q-27 (Miuuti Group)
- Mustang Panda APT
- ZyXEL backdoor credentials
- Elastic IP hijacking
- AI assistant coding tools are bad
- Cyber-attacks to become uninsurable
- New tool—PEACH
- New tool—Columbus Project
- Acquisition news
- New newsletter
- Updated on 2022-12-28
- More highlights from the past 24 hours
- Updated on 2022-12-26
- More highlights from the past 24 hours
- Updated on 2022-12-23
- More highlights from the past 24 hours
- Updated on 2022-12-22
- More highlights from the past 24 hours
- Raydium cyber-heist
- Nio extortion
- IE update
- Medical device security
- Chris Inglis resigns
- NCSC security advice
- JFK hack
- Smart home wall pad hacker
- Ring doorbell hackers
- T-Mobile hacker sentenced
- Pop-under campaign
- XLL campaigns
- MitM phishing
- SiestaGraph
- Trojanized WhatsApp app
- Coffee ransomware decrypter
- North Korean APTs
- CVE-2021-38003
- CVE-2022-41040 and CVE-2022-41082
- macOS Gatekeeper bypass
- MeshyJSON
- Rust training
- Trend Micro joins ADA
- Updated on 2022-12-21
- More highlights from the past 24 hours
- Updated on 2022-12-20
- More highlights from the past 24 hours
- Updated on 2022-12-19
- More highlights from the past 24 hours
- Apple rolls out iCloud encryption to everyone’s delight, except the FBI
- Hackers planted files to frame an Indian priest who died in custody
- Booters booted
- Updated on 2022-12-16
- More highlights from the past 24 hours
- GitHub to roll out mandatory 2FA
- Microsoft bans crypto-mining on Azure
- Z-Wave goes FOSS
- New web tracking technique
- SBOM left out of NDAA
- Cyber postures
- Russia to ban remote work from abroad
- 17k C&Cs
- Surveillance-for-hire industry
- SMS scam campaigns
- Masscan ransomware
- RedGoBot
- BrasDex
- FreePBX campaign
- UNC4166
- Meta bug bounty payouts
- Cookie expiration issues
- Cache poisoning attack
- CVE-2022-37998 and CVE-2022-37973
- Free service launch
- Updated on 2022-12-15
- More highlights from the past 24 hours
- When Extortion for Insider Trading is Good News
- SBOM Meets the Too Hard Basket, For Now
- New spyware vendor
- Updated on 2022-12-14
- More highlights from the past 24 hours
- Updated on 2022-12-13
- More highlights from the past 24 hours
- ITTF leak
- Manipulated academic imagery
- Jesuit priest framed in India
- Dutch government warnings
- NSA guidance
- Malicious IIS modules
- Kerberos attacks
- New npm malware
- Empire C2 Framework
- Influence operations targeting the US far-right
- Lenovo bugs still unpatched
- New tool—Alert on Public Repos
- Updated on 2022-12-12
- More highlights from the past 24 hours
- Lodestar Finance crypto-heist
- Edge support on Windows 7/8
- Mis/disinformation framework
- International SMS spam on the rise
- IAB market trends
- Python backdoor targeting ESXi
- New ransomware
- Cloud Atlas (Inception) APT
- DolphinCape
- Medical lab vulnerability
- Dirty Vanity technique
- Vulnerability does not compute
- Google One VPN security audit
- Updated on 2022-12-09
- More highlights from the past 24 hours
- Updated on 2022-12-08
- More highlights from the past 24 hours
- Updated on 2022-12-07
- More highlights from the past 24 hours
- Threema’s new Ibex protocol
- EU funds Cyber Lab in Ukraine
- ANSSI boss leaves post
- Dutch SIM swapper gets four years
- IRS fraudsters arrested
- Money launderers arrested
- New npm malware
- IoT malware evasion techniques
- DanaBot
- AndroxGh0st
- ChatGPT tools
- New tool—SandboxSecurityTools
- New tool—GCPGoat
- Updated on 2022-12-06
- More highlights from the past 24 hours
- Updated on 2022-12-05
- More highlights from the past 24 hours
- CoinTracker email leak
- ARSAT incident
- Beeline hack
- Chrome Enhanced Protection
- UK MSP regulation
- Fidesz abused government data for political spam
- Coordination between Russian kinetic and cyberattacks
- Black Panthers gang
- SIM swapper gets 18 months
- $140 million revenue
- $3.3 billion in crypto stolen
- Pass-the-Cookie attacks
- BlackProxies
- New npm malware
- Conti gang
- Titan Stealer
- Influence operations
- Artifact poisoning
- Visual Studio Code RCE
- Hell’s Keychain
- CertPotato attack
- Updated on 2022-12-04
- ICE in hot water
- Updated on 2022-12-02
- More highlights from the past 24 hours
- Updated on 2022-12-01
- More highlights from the past 24 hours
- Guatemala ransomware attack
- Nomad Bridge hack
- Google sues review scammer
- Amazon Security Lake
- US shoots down US-Cuba subsea cable
- South Dakota bans TikTok
- Albania charges five government workers
- Dutch emergency warning
- NSO sued by journalists
- Insivible npm packages
- WordPress backup scans
- Malspam trends
- Xiongmai exploitation
- TAG-56
- Operation ShadowTiger
- Metador’s Mafalda
- Linux vulnerability
- Huawei hypervisor vulnerability
- iOS updates
- Snyk vulnerabilities
- Hive Social vulnerabilities
- Vulnerabilities in remote keyboard apps
- Delta Electronics vulnerabilities
- OT vulnerabilities
- AllInfosecNews
- Black Hat USA 2022 videos
Updated on 2022-12-30
Threats from multiple cybercriminal groups create a whole new level of complexity for the recovery of data and systems affected. A similar situation was faced by a popular toy production giant after Hive and BlackCat ransomware groups posted the data stolen from the firm on their leak sites. Meanwhile, a newly identified CatB ransomware group was spotted with enhanced evasion tactics involving DLL hijacking. Another day another attack against cryptocurrency platforms, and this time it is 3Commas. Keep reading to know about the latest security incidents from cyberspace.
More highlights from the past 24 hours
Toy maker Jakks Pacific disclosed a cyberattack after two ransomware groups posted stolen information on their leak sites. Hive leaked the details on December 19, followed by BlackCat on December 28. Read more:
3Commas cryptocurrency platform admitted to a hack after a set of 10,000 API keys was published by a hacker on Twitter. The firm has urged Kucoin, Coinbase, and Binance to revoke all keys connected to 3Commas.
A newly identified CatB ransomware group is implementing several anti-VM and DLL hijacking techniques to evade detection. The ransomware is believed to have a connection with Pandora ransomware. Read more: New CatB Ransomware Employs 2-Year Old DLL Hijacking Technique To Evade Detection
Telekom Malaysia (TM) confirmed a data breach that affected the personal information of over 200,000 of its Unifi mobile users. This includes the names, phone numbers, and email addresses of users. Read more: Over 200,000 customers affected by Unifi Mobile data breach
A credential harvesting campaign targeting systems running public-facing Jupyter Notebooks was uncovered. So far, 50 systems have been compromised. Read more: Cloud Cred Harvesting Campaign – Grinch Edition
The Ukraine cyber police seized a call center for duping 18,000 victims by pretending to be IT security employees at banks. The scammers contacted the victims on the pretext of preventing fraud against their bank accounts and requested their financial information.
The CISA added two-year-old vulnerabilities in TIBCO Software’s JasperReports product to its list of Know Exploited Vulnerabilities (KEV) catalog. The flaws are related to an information disclosure vulnerability and a directory traversal vulnerability. Read more:
A security researcher identified wiretapping bugs in Google Home smart speakers that can be exploited to install backdoors on devices and eavesdrop on users. Read more: Turning Google smart speakers into wiretaps for $100k
The U.S. president approved the expenditure for the fiscal year 2023, out of which $2.9 billion has been allocated to the CISA. The amount will be spent to protect both civilians and government networks from cyberattacks.
Updated on 2022-12-29
Ransomware groups are hitting from left, right, and center, disrupting operations and sensitive data being stolen from organizations. In less than a week, the LockBit ransomware group targeted two new victims, one of them being a government county in Ohio. On the other hand, the data stolen from a telecommunications company is being held at ransom by the Royal ransomware group. What else? Increased abuse of the Google Ads platform has also been noticed to deliver a variety of malware to victims’ systems. Let’s glance through all the other incidents that shaped today’s cybersecurity landscape.
More highlights from the past 24 hours
Data security software vendor Netwrix Corp. acquired Privileged Access Management Startup Remediant Inc. for an undisclosed price. With this, Netwrix aims to empower organizations with even better resistance against advanced threats. Read more: Netwrix Acquires Remediant for PAM Technology
Rubic crypto-heist
Cross-chain cryptocurrency platform Rubic was also hacked and lost $1.41 million worth of crypto assets. The company confirmed the incident and promised to refund affected users.
49ers CLA
The San Francisco 49ers NFL team has been sued in a class-action lawsuit for not properly disclosing in a breach notification that they suffered a ransomware attack and that some of their employee and customer PII data might have been exposed and leaked online on the dark web. Read more: San Francisco 49ers confirm ransomware attack
TikTok spied on journalists
Chinese social media giant TikTok has confirmed that it spied on the real-time location of Forbes journalists who reported on the company in the hopes of identifying some of their sources. Read more: EXCLUSIVE: TikTok Spied On Forbes Journalists
AT&T legal shenanigans
AT&T has updated its terms of service to exonerate itself in the case of unauthorized access to customer accounts that took place because of “negligence by an AT&T employee, representative, agent, or any person or entity purporting to act on AT&T’s behalf.” If you don’t get what this is about, it’s AT&T shielding itself from any responsibility in the case of SIM-swapping attacks, many of which are being carried out with the help of AT&T insiders.
Microsoft fined
French privacy watchdog CNIL has fined Microsoft €60 million for not having a mechanism in place on the Bing search engine through which users could easily refuse tracking cookies as easily as accepting them. Read more: Cookies : sanction de 60 millions d’euros à l’encontre de MICROSOFT IRELAND OPERATIONS LIMITED
International Counter Ransomware Task Force
An international task force focused on going after ransomware gangs is set to become active in January 2023. The new task force was announced at the second edition of the International Counter Ransomware Summit that took place in November this year and will be led by Australia. Read more: Background Press Call by a Senior Administration Official Previewing the Second International Counter Ransomware Initiative Summit
DOD cyber skill exodus
A GAO report has found that “military personnel who complete advanced cyber training—which may take a year or more and costs DOD hundreds of thousands of dollars—may not remain in the military for a significant time after training.” Read more: Military Cyber Personnel: Opportunities Exist to Improve Service Obligation Guidance and Data Tracking
“We found that 2 of the 4 military services are not positioned to ensure adequate return on their investment in advanced cyber training. While the Navy and Air Force require 3 years of active duty, the Marine Corps has no guidance for this area and Army guidance does not clearly define active duty service obligations.”
ShinyHunters extradition
Moroccan authorities have approved the extradition to the US of Sebastien Raoult, a French national suspected of being “Sezyo,” a member of the ShinyHunters hacking group. Raoult was detained earlier this year at the airport in Rabat, Morocco, while trying to take a flight to Brussels, Belgium. Read more:
- Developing: Moroccan court orders extradition of alleged member of ShinyHunters to U.S.
- Un étudiant français accusé d’un vaste piratage par le FBI arrêté au Maroc
Robin Hood stuff
Ukrainian cybersecurity expert Alex Holden claims to have hacked Solaris, a dark web drugs market serving the Russian community, and stolen more than $25,000 worth of cryptocurrency from its users and administrators. Holden told Forbes he donated the stolen funds to charity organizations helping Ukrainians affected by Russia’s invasion. Read more: A Ukrainian Steals $25,000 In Bitcoin From Russian Dark Web Drug Market And Gives It To A Kyiv Charity
New spyware vendor
Reporters from Israeli news outlet Haaretz have a profile on a new surveillance vendor. Named Toka, the company was founded by former Israeli PM Ehud Barak and provides clients with the ability to hack cameras and change their video feeds. Read more: This ‘Dystopian’ Cyber Firm Could Have Saved Mossad Assassins From Exposure
PureLogs campaigns
A new Malware-as-a-Service called PureLogs launched in the cybercrime underworld, and campaigns distributing its payloads have already been seen in the wild, targeting Italian users, per Symantec.
Shlayer
Confiant’s Taha Karim has a report on a new variant of the Shlayer macOS malware. Read more: L’art de l’évasion: How Shlayer hides its configuration inside Apple proprietary DMG files
NK crypto-heists
NIS, South Korea’s main intelligence agency, estimated that North Korean hackers stole roughly $1.2 billion worth of cryptocurrency funds over the past five years, with $626 million stolen in 2022 alone. Read more: Seoul: North Korean hackers stole $1.2B in virtual assets
North Korean APT campaigns targeting NFT users
SlowMist researchers have published a summary of a large-scale phishing campaign targeting NFT owners that appears to have been carried out by a North Korean APT group. Read more: SlowMist: Investigation of North Korean APT’s Large-Scale Phishing Attack on NFT Users
Albanian government attacks
The Iranian APT groups who attacked the Albanian government networks with data wipers this year used stolen certificates from Nvidia and Kuwait Telecommunications Company to sign their malware. According to Kaspersky, while the Nvidia certificates were known to have leaked, it is currently unknown how the hackers got their hands on the KTC certs. Read more: Ransomware and wiper signed with stolen certificates
APT-C-36 (Blind Eagle)
Qihoo 360 researchers have published a report on APT-C-36 (Blind Eagle), a suspected Latin American APT, and its recent spear-phishing campaigns delivering versions of AsyncRAT or NjRAT. Targeting seems to have been aimed at Colombia. Read more: APT-C-36(盲眼鹰)近期攻击活动分析
APT-Q-27 (Miuuti Group)
QiAnXin researchers have a report out on Operation Dragon Dance [1, 2], a series of attacks that targeted the southeast Asian gaming industry. The report is a continuation of previous reporting on a campaign known as Operation Dragon Breath [1, 2].
Mustang Panda APT
Vietnamese security researcher Soulevil has published an analysis of a PlugX malware sample used in a recent Mustang Panda APT intrusion. Recorded Future has a report on the same thing as well. Read more:
- Diving into a PlugX sample of Mustang Panda group
- RedDelta Targets European Government Organizations and Continues to Iterate Custom PlugX Variant [PDF]
ZyXEL backdoor credentials
Italian security researcher RE-Solver has found several backdoor credentials in the firmware of some ZyXEL routers. This includes hardcoded superuser credentials that can bypass web UI authentication and hardcoded credentials to allow root access via Telnet. Read more: [ CVE-2022-40602 ] ZyXEL LTE3301-M209 – “Backdoor” credentials
Elastic IP hijacking
Mitiga researchers have found a new attack vector in AWS infrastructure, namely in a new feature named AWS Elastic IP Transfer that allows AWS customers to move IP addresses when migrating server infrastructure. Read more:
- Elastic IP Hijacking — A New Attack Vector in AWS
- Amazon Virtual Private Cloud (VPC) now supports the transfer of Elastic IP addresses between AWS accounts
AI assistant coding tools are bad
Academics from Stanford have found that code written by AI assistant coding tools like GitHub Copilot produce code that contains more vulnerabilities than code written by actual humans. Read more: Do Users Write More Insecure Code with AI Assistants?
Cyber-attacks to become uninsurable
Mario Greco, chief executive at insurer Zurich, told the Financial Times last week that cyber-attacks will soon become uninsurable as the number of incidents continue to grow and so do the losses from them. Read more: Cyber attacks set to become ‘uninsurable’, says Zurich chief
New tool—PEACH
Cloud security firm Wiz has open-sourced PEACH, a tenant isolation framework for cloud applications. Read more: Introducing PEACH, a tenant isolation framework for cloud applications
New tool—Columbus Project
Elmasy has open-sourced a new tool called the Columbus Project that can help identify and list known subdomains for a particular domain name. Read more: Introducing the Columbus Project
Acquisition news
Cybersecurity firm Netwrix has acquired Remediant, a startup specializing in continuous privilege discovery and remediation. Read more: Netwrix Acquires Remediant to Provide Customers with Enhanced Privileged Access Security
Datadog’s Zack Allen has started a new infosec newsletter. Named Detection Engineering, the newsletter focuses on defending techniques and news.
Updated on 2022-12-28
More million-dollar crypto heist incidents have come to light as threat actors exploited a couple of DeFi protocols of late. Multiple Japanese financial institutions also came under attack by a financially motivated BlueNoroff group that is using a new tactic to evade MotW security measures. Meanwhile, Android users must exercise caution as a new attack method capable of stealing personal information comes to light. Read on to learn more about the top happenings in the cybersecurity landscape.
More highlights from the past 24 hours
Personal data of approximately 30 million Indian Railway users have been put on sale on the dark web. The stolen data includes emails, phone numbers, and invoices of passengers. Read more: Indian Railway Data Leak: 30 million Railway customers’ data for sale on the dark web
The UAE Cybersecurity Council warned all public and private institutions against cyberattacks during the New Year celebrations and holiday season. It urged organizations to bolster their cyber defense. Read more: UAE panel on cybersecurity warns against cyberattacks during New Year celebrations
Imperva’s report on the DDoS threat landscape mentions that the largest DDoS attack in 2022 was 4.5x larger than the biggest attack observed in 2021. The large-volume DDoS attacks per month also saw an 81% jump from the last year. Read more: 81% Increase in Large-Volume DDoS Attacks
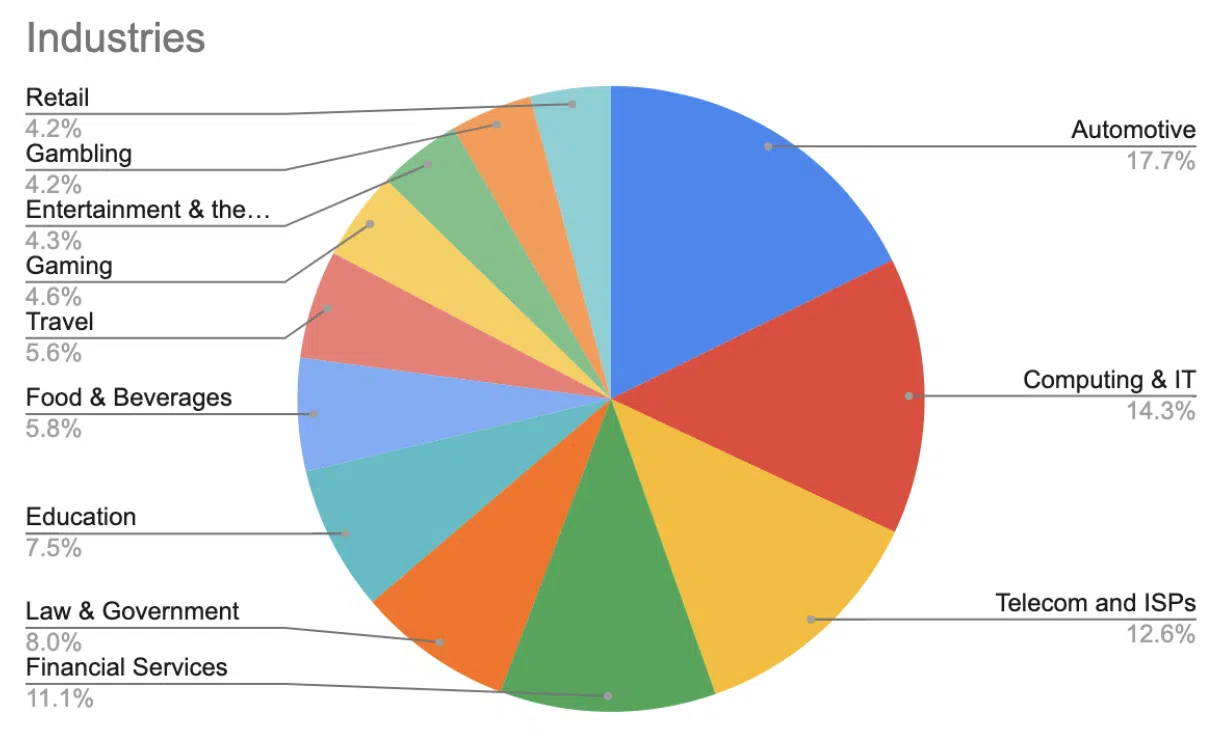
A report summarized by APWG states that the third quarter of 2022 witnessed a 488% increase in phishing attacks via emails when compared to the prior quarter. Read more: APWG PHISHING ACTIVITY TRENDS REPORT 3rd Quarter 2022 [PDF]
Updated on 2022-12-26
Cybercriminals spun another social engineering ruse aimed at NFT investors. In a new update, the North Korea-based Lazarus group has been linked to a massive phishing campaign that used around 500 phishing domains to target NFT investors. Meanwhile, a multichain cryptowallet platform has fallen victim to a DeFi exploit that resulted in the loss of around $8 million in assets. In another update, the notorious GuLoader malware has been upgraded with new capabilities to evade detection. Let’s dig in further to know all that happened in the cybersecurity space over the weekend.
More highlights from the past 24 hours
The Clifton-based Cincinnati State Technical Community College notified of a data breach that affected the personal information of students, including SSNs, health insurance, and financial account data. Read more: Notice of Data Security Incident on December 23, 2022 [PDF]
Washington-based Kaye Smith MultiCare hospital disclosed that more than 23,000 individuals are impacted by a third-party data breach that occurred in May. Read more: MultiCare Notifies 23K of Third-Party Breach
Amidst the holiday season, a spike in the number of Grinch bots impacting the online shopping experience has been observed. These bots are used to make fraudulent purchases and later resell the products for profit. Read more: Don’t let Grinch bots put coal in your stocking
According to a report compiled by the Ministry of Science and ICT, South Korea, the number of cyberthreats has increased by 60 percent in 2022. This is primarily due to increased ransomware attacks. Read more: Cyber threats shoot up over 60% through Nov: S.Korea
Updated on 2022-12-23
It is no secret that personal data is a potential gold mine for cybercriminals who can either use it for malicious activities or make profit by selling it on underground forums. Adding to this lately is the personal information of over a million customers associated with a popular sports betting company. Moreover, a widespread 2FA bypass attack against a telecommunications company has also put users at risk of data theft. In another vein, the Vice Society gang has adopted a new ransomware to maximize its attacks. Read on further to get an overview of what all new things have happened in the cyber world.
More highlights from the past 24 hours
Online sports betting company BetMGM confirmed suffering a data breach as threat actors offered to sell a database containing the personal information of 1.5 million customers. Read more: NOTICE REGARDING PATRON PERSONAL INFORMATION
A data breach at the Belgian bank, Degroof Petercam, led to the compromise of the data of hundreds of its clients, including multiple companies. Read more: Data leak at Degroof Petercam affects hundreds of Belgian companies
Indian government officials were targeted in a new phishing campaign, dubbed STEPPY#KAVACH, that was attributed to a threat actor whose tactics overlapped with the SideCopy hacker group. Read more: New STEPPY#KAVACH Attack Campaign Likely Targeting Indian Government: Technical Insights and Detection Using Securonix

A phishing campaign impersonating the Chinese Ministry of Finance and other state institutions was used to steal credit card credentials and other sensitive information. Threat actors used malicious QR codes to redirect victims to phishing sites. Read more: Phishing Campaign Abuses QR Codes to Steal Credit Card Details

Updated on 2022-12-22
Ransomware attacks have surged drastically across all sectors, not excluding the media sector. In one such instance, a famous British newspaper suffered a ransomware attack that disrupted its systems. Once again, we are back with server misconfiguration news. A global shoe manufacturer and retailer exposed millions of sensitive records since 2021. In other news, North Korean threat actors reportedly stole over a billion in cryptocurrency over the past few years. Read along for more.
More highlights from the past 24 hours
Shoemaker Ecco left 50 indices exposed to the public internet, with over 60GB of data accessible since June 2021. The server misconfiguration could have impacted millions of users. Read more: Shoemaker Ecco leaks over 60GB of sensitive data for 500+ days

South Korea’s spy agency estimated that North Korea-based threat actors stole approximately $1.2 billion in cryptocurrency and other virtual assets in the last five years. Read more: Seoul: North Korean hackers stole $1.2B in virtual assets
President Biden signed the Quantum Computing Cybersecurity Preparedness Act that would motivate federal agencies to adopt technology protected from decryption by quantum computing.
The French government introduced a “vast training program” to aid hospital staff in defending against threat actors, following a series of cyberattacks against healthcare facilities.
Raydium cyber-heist
Solana-based DeFi platform Raydium was hacked for $5.5 million. According to CertiK, “the attack appears to be the result of a trojan attack & private key compromise.”
Nio extortion
Chinese EV maker Nio said it was being blackmailed by hackers. According to Bloomberg, hackers are asking $2.25 million in Bitcoin from the company to not leak sensitive information they stole from the company in August 2021. Nio said this data contains “information of users and vehicle sales in China before August 2021.” Read more:
- NIO Inc. Promptly Responds to Data Leakage
- Nio Blackmailed for Millions in Bitcoin by Data-Stealing Hackers
IE update
Microsoft says that an Edge browser update that will be released on February 14, 2023, will permanently disable Internet Explorer 11 on Windows 10. Read more: Disable Internet Explorer 11
Medical device security
Furthermore, the Consolidated Appropriations Act, 2023 [PDF, page 3537] also codifies the PATCH Act and will require that medical devices be kept up to date with security updates and more.
Chris Inglis resigns
Chris Inglis will resign as National Cyber Director in the coming months, per CNN. Inglis has served as National Cyber Director in the White House since July 2021. Read more: Top Biden cybersecurity adviser to step down
NCSC security advice
The UK National Cyber Security Centre has a security advisory with a bunch of basic advice for beginners. Some of it includes recommending that users open PDF files in browsers rather than PDF readers, disabling the option to open/mount ISO files on a system, and the use of email server gateways in corporate environments. Read more: Telling users to ‘avoid clicking bad links’ still isn’t working
JFK hack
The US DOJ has charged two US nationals for working together with two Russian hackers to hack the taxi dispatch at the JFK airport in New York. US authorities said the group hacked the taxi queuing software and allegedly allowed drivers to cut the waiting line for a fee. Read more: Two Men Arrested For Conspiring With Russian Nationals To Hack The Taxi Dispatch System At JFK Airport
Smart home wall pad hacker
South Korean authorities have arrested a local IT professional who hacked a server that manages smart home wall pads for 638 buildings, recorded photos and videos of people in their homes, and then attempted to sell the footage online. Read more: New 국내 수백 개 아파트 단지 서버와 세대내 통합 주택 제어판(월패드)을 해킹한 보안전문가 검거
Ring doorbell hackers
California officials have charged two men for hacking Ring doorbell cameras across the US and then recording victims while they were getting swatted by police, swat calls they placed themselves. Read more: Grand Jury Indicts 2 in ‘Swatting’ Scheme that Took Over Ring Doorbells Across U.S. to Livestream Police Response to Fake Calls
T-Mobile hacker sentenced
Argishti Khudaverdyan, the owner of a T-Mobile retail who hacked into T-Mobile’s main network as part of a larger phone-unlocking scheme, was sentenced last week to 10 years in prison. Read more: Former Mobile Phone Store Owner Sentenced to 10 Years in Federal Prison for Multimillion-Dollar Scheme to Illegally Unlock Cellphones
Pop-under campaign
Malwarebytes has a report out on a malvertising campaign that uses pop-under ads on adult websites to redirect visitors to fake news sites as part of an ad fraud scheme. Read more: Adult popunder campaign used in mainstream ad fraud scheme
XLL campaigns
Cisco Talos researchers have a review of recent malspam campaigns that abuse Excel add-in (XLL) files to trick users into installing malware on their systems. This includes the whole gamut of groups, from financially-motivated boy bands like FIN7 and Dridex to cyber-espionage outfits like APT10, Donot, and TA410. Read more: Threat Spotlight: XLLing in Excel – threat actors using malicious add-ins
MitM phishing
PAN’s Unit42 team has a breakdown of meddler-in-the-middle (MitM) phishing campaigns that have taken place throughout 2022. This includes campaigns targeting users of platforms like GitHub, Dropbox, Microsoft, CircleCI, and others. Read more: Meddler-in-the-Middle Phishing Attacks Explained
SiestaGraph
Elastic’s security team has a report out on SiestaGraph, a PowerShell-based backdoor that leverages the Microsoft Graph API for command and control. The malware was found installed on an Exchange server belonging to the Foreign Affairs Office of an ASEAN country. Read more: SiestaGraph: New implant uncovered in ASEAN member foreign ministry
Trojanized WhatsApp app
Chinese security firm Zero Hour Technology says it linked several instances of trojanized WhatsApp clients available in China to thefts of personal funds from infected devices. Reported losses have been estimated at nearly $1.5 million. Read more: 零时科技 || 警惕恶意聊天软件!聊天记录被劫持损失数千万资产追踪分析
Coffee ransomware decrypter
Researchers from Chinese security firm Sangfor have released a free decryption utility to recover files encrypted by the Coffee ransomware. A technical analysis of the ransomware and its encryption flaw can be found here. The Coffee ransomware appeared in February this year and spread mainly via Chinese internet sites and social networks. Read more:
North Korean APTs
Sekoia has a year-in-review report on the North Korean cyber-espionage campaigns that have been documented this year. Read more: The DPRK delicate sound of cyber
CVE-2021-38003
StarLabs has a breakdown of an old Chrome vulnerability tracked as CVE-2021-38003, patched last year after being exploited in the wild. Read more: TheHole New World – how a small leak will sink a great browser (CVE-2021-38003)
CVE-2022-41040 and CVE-2022-41082
Kaspersky has a report out on two Microsoft Exchange zero-days known as ProxyNotShell. Read more: CVE-2022-41040 and CVE-2022-41082 – zero-days in MS Exchange
macOS Gatekeeper bypass
Microsoft has published a write-up on another macOS Gatekeeper bypass found by its MSTIC team. I don’t know how I feel about Microsoft’s security teams sifting through Apple’s products when their Exchange servers keep getting ransomed left and right. Read more: Gatekeeper’s Achilles heel: Unearthing a macOS vulnerability
MeshyJSON
NCC Group has a report on MeshyJSON, a stack overflow vulnerability in the tdpServer binary included with the firmware of TP-Link routers. Read more: MeshyJSON: A TP-Link tdpServer JSON Stack Overflow
Rust training
The Android Team has open-sourced its internal Rust training courses.
Trend Micro joins ADA
Trend Micro and McAfee will officially join the Google App Defense Alliance. Also known as ADA, this is a project through which Google gives security vendors access to the Play Store security systems so security firms can help it identify and remove Android malware faster. Previous members include the likes of ESET, Lookout, and Zimperium. Read more:
- Expanding the App Defense Alliance
- The App Defense Alliance: Bringing the security industry together to fight bad apps
Updated on 2022-12-21
Healthcare breaches have gotten more complex as third-party risks continue to escalate. In a new revelation, a healthcare IT service provider notified thousands of patients of a data breach that may have impacted their details. Lingering on breaches, an FBI database was, allegedly, infiltrated by a group of Russian hackers. In other news, major steel producer Thyssenkrupp suffered a cyberattack. Here are the top 10 highlights from the past 24 hours.
More highlights from the past 24 hours
Oklahoma-based Avem Health Partners, an IT service provider to healthcare facilities, started notifying around 271,000 individuals of a data breach at one of its vendors that compromised that personal information. Read more:
A large-scale ad fraud campaign using Google Ads and popunders on adult sites is estimated to have generated millions of ad impressions, raking in $275,000 per month.
Cyber risk analytics platform CyberCube raised $50 million in growth funding led by Morgan Stanley Tactical Value and featuring several other participants. Read more: CyberCube raises 50$ million
Updated on 2022-12-20
In yet another instance of cloud misconfiguration, a well-known publishing company came under fire for exposing the sensitive information of students. While this data leak was closed before it could cause further damage, the attack at an acclaimed German hotel chain could not be stopped in time. Play ransomware gang stole sensitive data and listed the company on its website as part of its extortion scheme. In another incident, the Ukrainian military found itself the target of a malware attack campaign. Let’s dive into the list to know what all new happened in cybersecurity.
More highlights from the past 24 hours
- A hacker managed to steal over $1 million (850 ETH) worth of 14 Bored Ape NFT collections in a carefully-planned month-long social engineering campaign that was executed against an unnamed victim. So far, the Bored Ape Yacht Club (BAYC) has lost more than 200 ETH to cybercriminals this year. Read more: Infamous hacker steals 14 BAYCs worth over 852 ETH ($1.07 million)
- The U.K Information Commissioner’s Office is planning to name breached firms by publishing details of personal data breaches and civil investigations on its websites. This will help track repeat offenders that fail to protect customer and employee data. Read more: UK Privacy Regulator Names and Shames Breached Firms
- Germany-based cybersecurity startup VMRay raised $34 million in Series B funding which was led by Tikehau Capital, with participation from High-Tech Gründerfonds, eCapital, NRW.BANK, and Gründerfonds Ruhr. Read more: Germany’s VMRay ties up $34 million series B to expand threat detection and analysis
Updated on 2022-12-19
Have you made a restaurant reservation recently? Then this news is for you. A platform used for managing restaurant customer relations confirmed suffering a data breach. In another incident, tens of thousands of Medicare beneficiaries were affected by unauthorized access to a subcontractor’s systems. Meanwhile, the U.S. food companies were warned of widespread BEC attacks that can steal the shipment details of their food products. Read on to know more on how the threat landscape shaped over the weekend.
More highlights from the past 24 hours
- Restaurant CRM platform SevenRooms confirmed suffering a data breach after a hacker claimed to have stolen 427 GB of customer records and leaked a sample on a cybercrime forum. Read more: Restaurant CRM platform ‘SevenRooms’ confirms breach after data for sale
- The HHS Centers for Medicare and Medicaid Services notified 254,000 beneficiaries of a ransomware attack on a third-party vendor, which may have compromised their personal details. Read more: Subcontractor Breach Affects 245K Medicare Beneficiaries
- Fire Rescue Victoria, Australia, was forced to shut down its network, emails, and dispatch after an external third-party launched a cyberattack against the service. Read more: Fire and rescue service in Victoria, Australia, confirms cyber attack
- A third-party after-hours call service supplier for New Zealand’s MAS Insurance suffered a data breach, potentially compromising the personal data of medical professionals. Read more: Cyber attack on NZ’s largest insurer of doctors MAS may have exposed members’ personal data
- Around 300 apps on the Google Play Store are found leaking the API keys of three popular email service providers. This puts mobile users at risk as threat actors can perform many unauthorized actions. Read more: Mobile App Users at Risk as API Keys of Email Marketing Services Exposed
- Cybersecurity solutions provider for AI and ML systems, Protect AI, raised $13.5 million in seed funding, co-led by Boldstart Ventures and Acrew Capital. Read more: Protect AI emerges from stealth and raises $13.5 million
Apple rolls out iCloud encryption to everyone’s delight, except the FBI
Remember a few years ago when the FBI tried to compel Apple to build a backdoor so it could hack into a shooter’s iPhone? The case collapsed when hackers found a way in, rather than relying on Apple’s compulsory assistance. Fast forward five years and now Apple is doubling down on its encryption, closing a loophole long used by feds to acquire iPhone data in the cloud, by finally end-to-end encrypting iCloud Backups with a new update starting with iOS 16.2, released last week. It’s a huge move for users who backup to Apple’s cloud. Clearly the FBI isn’t happy (even though it can still break into locked phones). In a statement, the FBI said it was “deeply concerned” by the “threat” end-to-end encryption poses. (My read: It’s like the FBI just locked its keys in the car and now it’s cross at the car maker? I digress.) Wired ($) broke the news last week, and that Apple dropped its controversial plan to scan users’ photos client-side for child abuse materials. Read more:
- Apple Angers FBI By Offering More Privacy And Security To Users
- Australian firm Azimuth unlocked the San Bernardino shooter’s iPhone for the FBI
- Exclusive: Apple dropped plan for encrypting backups after FBI complained – sources
- The FBI is mad because it keeps getting into locked iPhones without Apple’s help
- Apple Expands End-to-End Encryption to iCloud Backups
- Apple Kills Its Plan to Scan Your Photos for CSAM. Here’s What’s Next
- Apple advances user security with powerful new data protections
- Apple says it will allow iCloud backups to be fully encrypted
- Why You Should Enable Apple’s New Security Feature in iOS 16.2 Right Now
Hackers planted files to frame an Indian priest who died in custody
Wild reporting from @agreenberg on the case of 84-year-old Stan Swamy, who contracted COVID-19 in an Indian jail and died. A forensic examination of Swamy’s laptop shows Indian police compromised his laptop and planted evidence, then tried to delete files (to destroy evidence and cover their tracks) just one day before police seized his devices. This isn’t even the first time this has happened. Per Wired: “Swamy never touched the files himself. After his devices were seized by Pune City Police, those files were among the digital evidence used to charge him and the other Bhima Koregaon 16 defendants with terrorism as well as inciting a riot in 2018 that led to two deaths.” Read more:
- Police Linked to Hacking Campaign to Frame Indian Activists
- ModifiedElephant APT and a Decade of Fabricating Evidence
- Hackers planted evidence on computer of jailed Indian priest, report says
- Hackers Planted Files to Frame an Indian Priest Who Died in Custody
Booters booted
The U.S. seized 48 websites in a sting aimed at taking down DDoS-for-hire websites, which allow paying users to pummel websites with traffic to knock them offline. Six were charged under U.S. hacking laws. Though, it took a bit of time for the government to actually take down the offending sites… whoops. Read more:
- Federal Prosecutors in Los Angeles and Alaska Charge 6 Defendants with Operating Websites that Offered Computer Attack Services
- US claims major DDoS-for-hire takedown, but some ‘seized’ sites still load
- US Is Seizing 48 Websites in Sting of Cyberattack-for-Hire Services
Updated on 2022-12-16
If you are a subscriber of FuboTV, you may have faced some disruptions streaming the World Cup semi-final between France and Morocco. The streaming service finally confirmed that it was the result of a cyberattack. Millions of users of yet another crypto exchange were impacted by a data breach at a third party. In another vein, new research revealed that the number of unique C2 servers has surged quite a bit. Read along for more from cyberspace.
More highlights from the past 24 hours
- FuboTV confirmed that a cyberattack was responsible for a streaming outage preventing subscribers from watching the FIFA World Cup Qatar 2022 semi-final match. Read more:
- Crypto exchange Gemini was targeted in a phishing attack after hackers breached an unnamed third-party vendor and put up for sale the personal information of 5.7 million users. Read more: Protecting Our Customers From Phishing Campaigns
- Mandiant spotted a campaign against the Ukrainian government via trojanized ISO files pretending to be legitimate Windows 10 installers. These were spread via torrent sites in a supply chain attack. Read more: Trojanized Windows 10 Operating System Installers Targeted Ukrainian Government
- The number of unique C2 servers spiked by 30% this year, from 13,629 in 2021 to 17,000 in 2022 – noted Recorded Future. Read more: 2022 Adversary Infrastructure Report
- Trustwave identified a Meta-Phish campaign using Facebook posts as part of its attack chain to evade detection and trick users into giving away their PII and account credentials. Read more: Meta-Phish: Facebook Infrastructure Used in Phishing Attack Chain
GitHub to roll out mandatory 2FA
Microsoft GitHub code hosting service announced that all users who contribute code on the platform will be required to have one form of 2FA by the end of 2023. Throughout next year, users will be enrolled in batches, and once they receive a notification from Microsoft, they will have 45 days to enable 2FA, or they’ll lose access to their GitHub account. Read more: Raising the bar for software security: next steps for GitHub.com 2FA
Microsoft bans crypto-mining on Azure
Microsoft has updated its terms of service to ban cryptocurrency mining on its online infrastructure, such as its Azure cloud, without its specific approval. Read more: Microsoft Product Terms > Summary of Changes
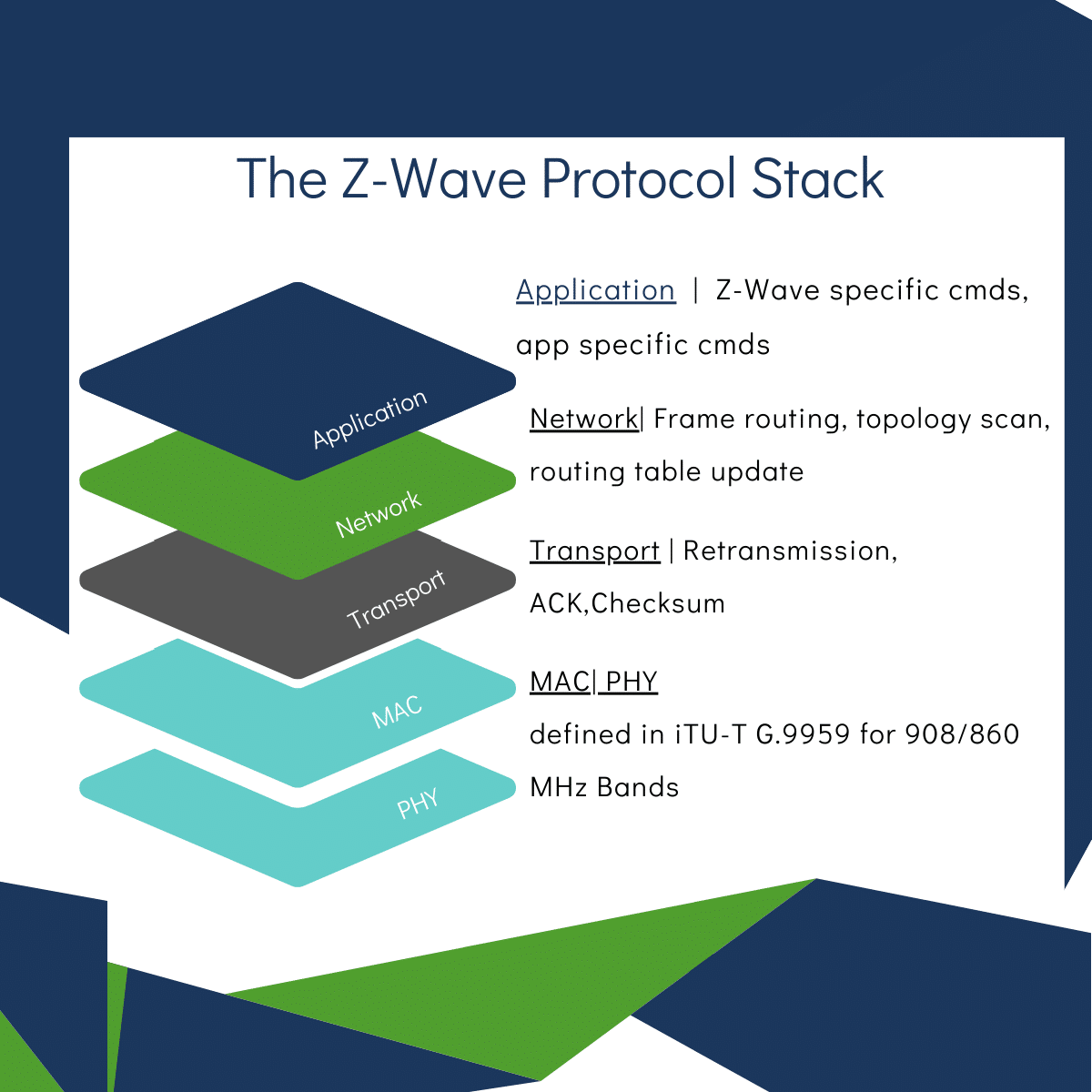
Z-Wave goes FOSS
The Z-Wave wireless protocol has gone open-source. Read more: Z-Wave Alliance Announces Z-Wave Source Code Project Is Complete, Now Open And Widely Available To Members
New web tracking technique
Academics from the University of California, San Diego, have developed a tool called CrumbCruncher which they used to measure the usage of UID smuggling in the wild. UID smuggling is a new type of web tracking that advertisers developed as an alternative after browser makers started blocking third-party cookies. The research team says that around 8% of the traffic they analyzed appears to use UID smuggling. Full paper here/PDF. Read more: New Web Tracking Technique is Bypassing Privacy Protections
SBOM left out of NDAA
After an alliance of tech vendors has complained [PDF] that the SBOM standard is not yet mature enough, US lawmakers have removed language from the National Defense Authorization Act bill that would have required vendors to provide bills of materials for all software provided to government agencies. Read more: Software supply chain amendment omitted from NDAA text
Cyber postures
The Stockholm International Peace Research Institute (SIPRI) has a report out on the evolution of cyber postures for today’s top powers, the US, EU, China, and Russia. It’s a good report to read, especially because it covers a little bit of the historical events that shaped national cybersecurity politics in recent years. Read more: Cyber Posture Trends in China, Russia, the United States and the European Union
Russia to ban remote work from abroad
Russian news outlets are reporting that the Russian government is working on a bill that would prohibit remote work for Russians who left the country. The bill appears to be aimed at Russian who fled the country in the aftermath of Russia’s invasion of Ukraine but continued to work for their Russian employers. Read more:
- Клишас допустил ограничения для уехавших после начала мобилизации россиян
- Клишас подтвердил разработку законопроекта об ограничении удаленки для уехавших из России
- В ГОСДУМУ ВНЕСУТ ЗАКОН О ЗАПРЕТЕ УДАЛЁННОЙ РАБОТЫ ИЗ-ЗА ГРАНИЦЫ
17k C&Cs
In a report reviewing the 2022 adversary landscape, Recorded Future says it observed 17,233 command and control servers that were set up during 2022, up 30% from last year (13,629 in 2021). Most of these were Cobalt Strike team servers, botnet families including IcedID and QakBot, and popular RATs such as PlugX, it said. Read more: 2022 Adversary Infrastructure Report
Surveillance-for-hire industry
Meta’s security team has published a report on the surveillance-for-hire industry [PDF]. The company said it took down this year several accounts on its social media sites that were being used by various hacker-for-hire companies. This includes:
- About 130 accounts on Facebook and Instagram linked to a known Israeli spyware developer Candiru, co-founded by a former employee of NSO Group.
- About 250 accounts on Facebook and Instagram linked to another known spyware vendor Quadream, an Israeli-based company founded by former NSO employees.
- About 230 accounts on Facebook and Instagram linked to CyberGlobes in Israel.
- More than 100 accounts on Facebook and Instagram linked to Avalanche in Russia, selling access to a platform that enables reconnaissance across the internet.
- About 3,700 Facebook and Instagram accounts linked to Social Links, a web firm originally based in Moscow, Russia, and now operating in New York in the United States.
- More than 40 accounts on Facebook and Instagram operated by an Indian firm called CyberRoot Risk Advisory Private.
SMS scam campaigns
Bitdefender has a report on some of today’s most aggressive SMS scam campaigns taking place in various countries across the globe. Read more: SMS Scams Exposed: A Look at Ongoing Campaigns Worldwide
Masscan ransomware
The Financial Security Institute of South Korea has published a report on the Masscan ransomware (aka MaRS), which recently hit multiple South Korean companies. Read more: Masscan Ransomware Threat Analysis – 2022 Cyber Intelligence Report
RedGoBot
Chinese security firm QiAnXin has spotted a new IoT malware strain named RedGoBot that appears to target Vacron NVRs. An analysis of the code shows the malware is intended for DDoS attacks. Read more: RedGoBot——新型Go语言编写的DDoS僵尸网络
BrasDex
ThreatFabric researchers have a report on BrasDex, a new Android banking trojan that originates from Brazil. ThreatFabric says the group behind BrasDex also appears to be involved in attacks using Casbaneiro, a banking trojan that targets Windows devices. Read more: BrasDex: A new Brazilian ATS Android Banker with ties to Desktop malware
FreePBX campaign
Sucuri researchers have analyzed a backdoor planted as part of an exploitation campaign that targets FreePBX, a web-based open-source GUI for managing Asterisk VoIP servers. Read more: Backdoor Targets FreePBX Asterisk Management Portal
UNC4166
Mandiant says that a threat actor it tracks as UNC4166 used trojanized versions of the Windows 10 OS installer distributed via Ukrainian torrent websites to infect locals with malware. Researchers say the group then handpicked government-related targets from their pool of compromised systems and deployed additional malware that could aid with reconnaissance and data theft.
“At this time, Mandiant does not have enough information to attribute UNC4166 to a sponsor or previously tracked group. However, UNC4166’s targets overlap with organizations targeted by GRU-related clusters with wipers at the outset of the war.”
Meta bug bounty payouts
Meta said it paid more than $2 million in bug bounty payouts to security researchers this year, bringing its payouts since the program’s inception in 2011 to more than $16 million. Read more: Looking Back at Our Bug Bounty Program in 2022
Cookie expiration issues
Atlassian products like Jira, Confluence, Trello, and BitBucket apparently have an issue with their cookie management, which they fail to invalidate once a user changes their password. This may lead to situations where attackers can retain access to hacked accounts using stolen cookies, even if an organization has reset passwords. See CloudSEK’s report. Read more: Security Flaw in Atlassian Products (Jira, Confluence,Trello, BitBucket) Affecting Multiple Companies
Cache poisoning attack
Tarunkant Gupta, a security engineer for Disney’s Hotstar, has found a novel cache poisoning attack that takes place between Akamai and AWS S3 infrastructure. Read more: Unusual Cache Poisoning between Akamai and S3 buckets
CVE-2022-37998 and CVE-2022-37973
On the same note, Akamai’s Ben Barnea also published details this week about two older vulnerabilities that Microsoft patched in October—namely, CVE-2022-37998 and CVE-2022-37973, bugs affecting the Windows Local Session Manager RPC interface. PoCs for both are available on GitHub. Read more: You’ve Crossed the Line — Disturbing a Host’s Rest
“The vulnerabilities lead to denial-of-service attacks that prevent container and session services (such as Microsoft Defender Application Guard, Sandbox, Docker, and Windows Terminal Server) from working.”
Free service launch
Wordfence launched this week a vulnerability database for WordPress security bugs. The service is free for community use and under a commercial license for hosting companies, security organizations, threat analysts, security researchers, and other commercial projects. Read more: Wordfence Launches Free Vulnerability Database For Commercial Use – And Launches Security Portal
Updated on 2022-12-15
Threat actors are increasingly abusing open-source repositories for phishing activities as proven by the hundreds of thousands of phishing-related packages revealed in a new discovery. In other news, Japanese political entities are under attack from a new credential stealer. We also have a new piece of research disclosing that millions of IP cameras are exposed to the internet. Here are the top 10 highlights from the past 24 hours.
More highlights from the past 24 hours
- New research revealed that 3.8 million IP cameras, belonging to the 28 most popular manufacturers, are exposed to the internet – an 8x increase since April 2021. Read more: 3.5m IP cameras exposed, with US in the lead
- ASEC researchers discovered the propagation of STOP ransomware in South Korea. The files downloaded by the ransomware include various kinds of malware, including banking malware. Read more: STOP Ransomware Being Distributed in Korea
- Australia and Vanuatu signed a bilateral security agreement that aims to establish cooperation over cybersecurity matters, including environmental, resource, maritime, and aviation security. Read more: Vanuatu and Australia sign Bilateral Security Agreement
When Extortion for Insider Trading is Good News
A Krebs on Security article explains that the latest innovation in ransomware is to frame executives by planting emails that implicate them in insider trading. We think it is good news that groups are being forced to try different extortion schemes. Alex Holden, founder of cyber security firm Hold Security, told Krebs that the group in question gets access to victim organisations “but nobody wants to pay them”. Read more: New Ransom Payment Schemes Target Executives, Telemedicine
SBOM Meets the Too Hard Basket, For Now
FedScoop reports that an amendment to force some contract holders to provide a software bills of materials (SBOM) has been omitted from the National Defense Authorization Act. While SBOMs would help when it comes to remediating problems such as Log4Shell it’s such a long-term project that we can’t help but think that current bandwidth might be better spent elsewhere anyway. Read more: Software supply chain amendment omitted from NDAA text
New spyware vendor
Politico Europe has a profile on Altrnativ, a French company that allegedly sells spyware and surveillance tools to at least six African countries. The most interesting part of the piece is that one of the Altrnativ founders is the former CEO of Qwant, a privacy-first search engine that at one time was the default search provider of the Brave browser. That’s quite the career turn. Read more:
- France’s Mr. Privacy turns cybersnooper
- Fast and Private Brave Browser Chooses Qwant as its Default Search Engine in France and Germany
Updated on 2022-12-14
A credit card processing firm exposed the PII of nine million users, owing to a misconfigured database. Let us take a moment to recognize the incident’s potential impact, such as identity theft and loss of reputation. Talking about databases, an English-language cybercrime forum was found selling a database belonging to an FBI-vetted info-sharing network. In other news, the HHS warned against rising LockBit 3.0 infections. Read along for the top 10 highlights from cyberspace.
More highlights from the past 24 hours
- Security researchers identified an unsecured database, belonging to Cornerstone Payment Systems, containing 9,098,506 credit card transaction records. Read more: Payment Giant Exposed 9 Million Credit Card Transaction Record
- The San Gorgonio Memorial Hospital, California, reported a data breach that impacted its patients’ sensitive data, including SSNs, financial information, and medical care information. Read more: California hospital breach exposed patients’ Social Security numbers, medical info
- The Queen Elizabeth Hospital notified the public of a cyberattack against its network, causing disruptions and delays in operations. Read more: QEH warns of delays following cyber security incident
- Much like last year, 90% of the 10 largest healthcare data breaches in 2022 were caused by third-party vendors – reported SC Media. Two of these vendors affected hundreds of providers. Read more: Most of the 10 largest healthcare data breaches in 2022 are tied to vendors
Updated on 2022-12-13
Russian RaaS group LockBit is on an attack spree and in its latest attack, it has provided California’s finance department a deadline of December 24 for the ransom payment. Right after threat actors attacked Antwerp, another European country fell victim to disruptive attacks. A group of hackers now claimed two Swedish municipalities as its victims, which led to a crisis situation. Do you know how many new Windows malware samples were detected this year? Millions. Read along for the exact number and more from the past 24 hours.
More highlights from the past 24 hours
- Swedish municipalities of Borgholm and Mörbylångan suffered a cyberattack on their joint IT system, leading them to declare a ‘crisis situation’. Read more: ‘Crisis situation’ declared as two Swedish municipalities hit by cyberattack
- Research by Atlas VPN revealed that 59.58 million new Windows malware samples were discovered in the first three quarters of the year, making up for 95.6% of all malware in that period. Read more: 95.6% of New Malware in 2022 Targeted Windows
- Cybersecurity startup Snyk raised $196.5 million in Series G round, led by Qatar Investment Authority, with participation from Tiger Global and Sands Capital. Read more: Cybersecurity startup Snyk valued at $7.4 bln after latest funding
- Massachusetts-based AppSec company Veracode announced the acquisition of cybersecurity company Crashtest Security for an undisclosed sum. Read more: Veracode acquires Crashtest Security to improve web application security
ITTF leak
The International Table Tennis Federation (ITTF) has leaked the passports and vaccination certificates of hundreds of professional table tennis players. The leak was caused by an improperly configured cloud hosting service and the data was exposed for more than three years. The Dutch reporters who found the leak said they notified the ITTF several times this year before the federation finally intervened to secure the leaky server. Read more:
- Tafeltennisbond lekt honderden paspoorten en vaccinatiebewijzen van wereldtop
- ITTF found to have data leak of confidential player information
Manipulated academic imagery
Dr. Neal Krawetz has an interesting write-up on the practice of forging and editing images in academic studies and how these can be spotted.
Jesuit priest framed in India
Digital forensics company Arsenal Consulting said they found evidence that a hacker broke into the computer of Father Stan Swamy, an 84-year-old Jesuit priest, and planted incriminating evidence. The Indian government detained and sentenced Father Swamy on terrorism-related charges. He spent eight months in prison before passing away in July 2021. The case is among of dozen similar incidents where activists and academics have been framed and sentenced to jail in India after criticizing the Indian government. Several of these incidents have been tied to Indian police forces. Read more:
- Hackers planted evidence on computer of jailed Indian priest, report says
- Police Linked to Hacking Campaign to Frame Indian Activists
Dutch government warnings
The Dutch government said it sent out more than 5,200 warnings to Dutch companies since the summer of 2021 about security vulnerabilities in their IT networks. Officials said that around 76% of these warnings were for sensitive systems being accessible via the internet. The other warnings covered malware infections, leaked credentials, or unpatched systems. Read more: Bedrijfsleven 5.200 keer gewaarschuwd voor digitale kwetsbaarheden
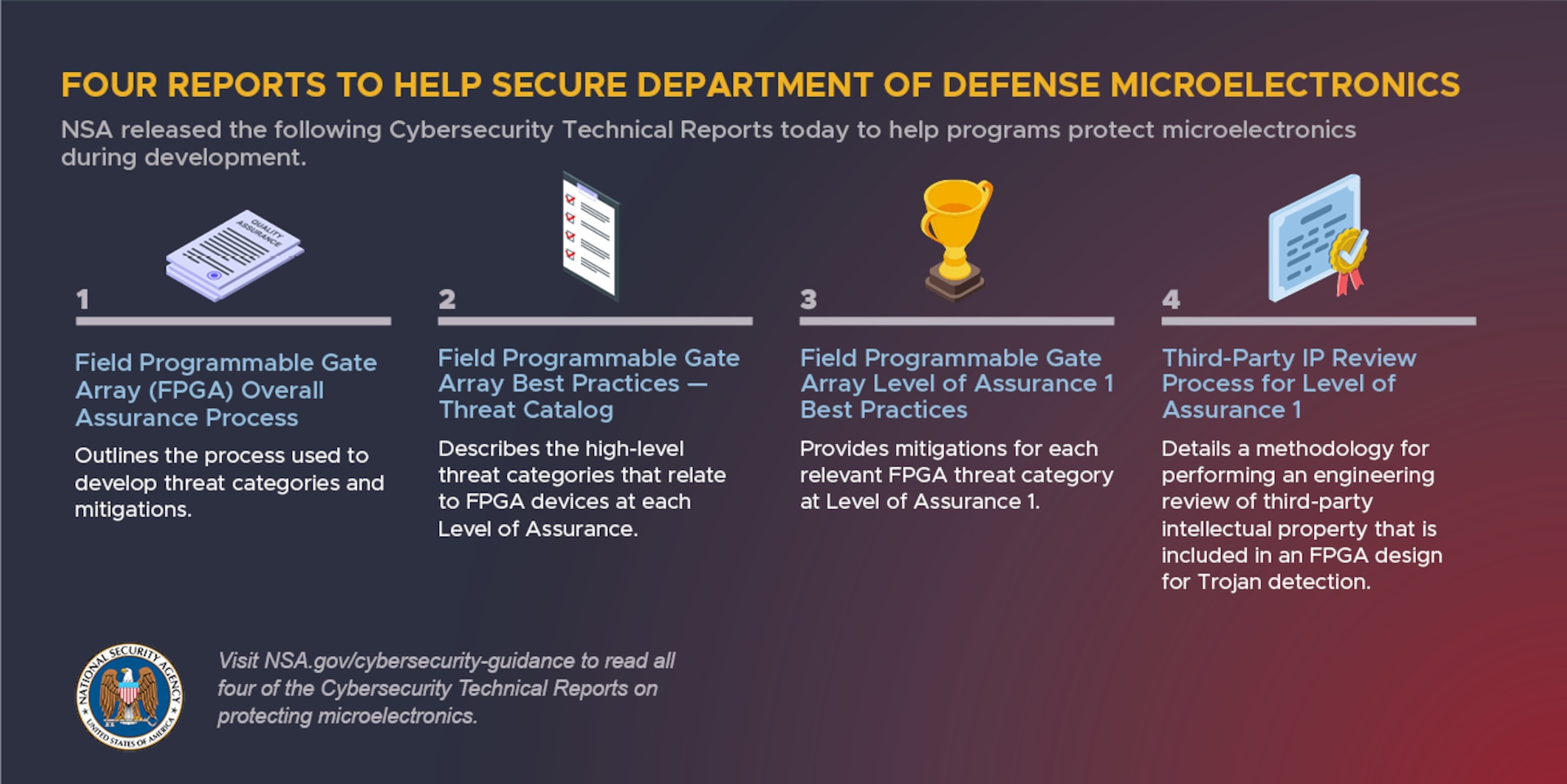
NSA guidance
The US National Security Agency published four documents last week that contain guidance meant to help vendors and government agencies protect microelectronic components from malicious influence. Read more: NSA Releases Series on Protecting DoD Microelectronics From Adversary Influence
Malicious IIS modules
Microsoft has a good report for defenders on how they can detect and protect against malicious IIS modules, which are often planted by threat actors on hacked IIS servers to hide backdoors and web shells. Read more: IIS modules: The evolution of web shells and how to detect them
Kerberos attacks
On the same note, PAN’s Unit42 has a guide on all the new variations of Kerberos attacks that have been discovered in recent months. Read more: Precious Gemstones: The New Generation of Kerberos Attacks
New npm malware
Ten new malicious npm packages spotted. Check out GitHub’s security advisory portal for details.
Empire C2 Framework
Qualys researchers have published a deep dive into Empire, an open-source post-exploitation framework that has been seeing adoption by malware operators in recent years. Threat actors seen using Empire include Turla, Leviathan, Wizard Spider (Conti/TrickBot), and many more. According to Qualys, although Empire has support for Linux, the vast majority of malware samples they found that used it had targeted Windows systems. Read more: Dissecting the Empire C2 Framework
Influence operations targeting the US far-right
A joint report by Graphika and the Stanford Internet Observatory has found a network of Russian troll farm accounts on right-wing social networks Gab, Gettr, Parler, and Truth Social. The accounts pushed divisive topics related to allegations of voter fraud in the 2020 US presidential election, voter fraud in the 2022 midterms, and attempts to undermine public support for Ukraine following Russia’s invasion. Read more: Suspected Russian Actors Leverage Alternative Tech Platforms in Continued Effort to Covertly Influence Right-Wing U.S. Audiences
“Based on the technical, behavioral, and content indicators detailed in this report, we assess with high confidence that this activity is linked to the actors behind the Newsroom for American and European Based Citizens (NAEBC), a fake right-wing news outlet that targeted US audiences ahead of the 2020 presidential election. NAEBC has been attributed by Meta to individuals associated with past activity of Russia’s Internet Research Agency (IRA), an assessment reportedly shared by US law enforcement.”
Lenovo bugs still unpatched
Binarly researchers say that even if Lenovo released patches for two BIOS Secure Boot bypass vulnerabilities (CVE-2022-3430 and CVE-2022-3431) last month, the fixes are incomplete, and Lenovo notebooks are still open to attack.Read more:
- Lenovo Notebook BIOS Vulnerabilities
- Firmware Patch Deep-Dive: Lenovo Patches Fail To Fix Underlying Vulnerabilities
New tool—Alert on Public Repos
Security firm PerimeterX has open-sourced a new tool called “Alert on Public Repos” that will alert GitHub organizations when one of their team members creates a repository in their personal account. The idea here is to alert admins about possible cases where a team member has accidentally put a work-related repo into their personal public account. Read more: Exposed Repository: Fixing the Accidental Public GitHub Repo
Updated on 2022-12-12
Remember Evilnum? It’s back in the news. Its latest campaign has been active for seven years now, which is targeting entities across a couple of industries. In another vein, an Australian telecommunications provider leaked the data for hundreds of thousands of customers and apologized. On the ransomware front, Hive claimed yet another victim in the education sector. Read along for the top 10 cybersecurity news from the past 24 hours.
More highlights from the past 24 hours
- The hack-for-hire group Evilnum was found targeting financial and travel entities in the Middle East and Europe. The campaign is, reportedly, active since 2015. Read more: Evilnum group targets legal entities with a new Janicab variant

- Around 360,000 Ontarians’ information was potentially compromised in a data breach of the Canadian province’s vaccine management system in 2021, revealed authorities. Read more: Data breach of Ontario’s vaccine booking system affects hundreds of thousands, province says
- Amazon is warning customers of a new smishing campaign that is breaking into their online accounts and stealing their personal data. Read more: Christmas is coming – must be time for another Amazon scam
- Researchers developed COVID-bit, a new attack tactic, that leverages electromagnetic waves to transmit data from air-gapped systems isolated from the internet. Read more: Air-gapped PCs vulnerable to data theft via power supply radiation
Lodestar Finance crypto-heist
A threat actor has abused an exploit in the smart contract of the Lodestar Finance DeFi platform and has stolen more than $5.8 million worth of cryptocurrency. The platform said it already recovered $2.4 million of the stolen funds and is still working to secure the rest. Just like most cryptocurrency platforms that get popped these days, Lodestar has offered to let the hacker keep some of the stolen funds and hide the intrusion under a “white-hat agreement.” Read more: Post Mortem Summary
Edge support on Windows 7/8
Microsoft plans to end support for its Edge web browser on Windows 7 and Windows 8/8.1 versions next year, on January 10, 2023. This is the same date when both Windows 7 and Windows 8/8.1 will reach End-Of-Life (EOL) after their extended support periods expire. Google also announced earlier this fall that Chrome version 110 would be the last to support both Windows 7 and Windows 8/8.1. Chrome 110 is scheduled for release in February 2023. Read more:
- Microsoft Edge and WebView2 ending support for Windows 7 and Windows 8/8.1
- Sunsetting support for Windows 7 / 8/8.1 in early 2023
Mis/disinformation framework
The EU Agency for Cybersecurity (ENISA) and the European External Action Service (EEAS) have put forward an analytical framework for the study of misinformation and disinformation. Read more: Foreign Information Manipulation Interference (FIMI) and Cybersecurity – Threat Landscape
International SMS spam on the rise
AdaptiveMobile researchers said they are seeing a new trend of using international numbers for the delivery of SMS spam and phishing messages to mobile subscribers in other countries. Read more: SMS Spammers Go Phishing in International Waters
IAB market trends
CYFIRMA has published a review of the initial access brokers (IAB) market and the trends and insights they’ve observed this year. Some of the report’s main conclusions:
- Before posting access to the underground forum, initial access brokers use ZoomInfo to compile data on the victim organization, including revenue, the industry it serves, the number of employees, and the type of business.
- Access to organizations in the United States is more expensive than in other countries.
- Access to banking domains is more expensive than any other domain. Banking access is sold for USD 10,000 to USD 160,000 (based on recent sales) by IABs.
- Some IABs post details on what data is available in the system to which they are selling access to provide heads-up to the buyer on what to expect in the system.
- Anti-Virus details in the victim system are shared in the sale posting.
Read more: Inside the World of Initial Access Broker (IAB): Insights and Trends
Python backdoor targeting ESXi
F5’s security team has uncovered a new Python-based backdoor that has been deployed on compromised VMWare ESXi servers. Read more: A Custom Python Backdoor for VMWare ESXi Servers
New ransomware
Fortinet researchers have a round-up of new ransomware strains they’ve seen in the wild over the past week. The list includes the likes of Vohuk, ScareCrow, and AERST. Read more: Ransomware Roundup – New Vohuk, ScareCrow, and AERST Variants
Cloud Atlas (Inception) APT
Check Point and Positive Technologies both published reports on the Cloud Atlas APT last week. Both companies observed that since the onset of the Russian-Ukrainian conflict, the group has narrowed down and focused its activities on Russia, but also Belarus and conflicted areas in Ukraine and Moldova. Read more:
- Cloud Atlas targets entities in Russia and Belarus amid the ongoing war in Ukraine
- APT Cloud Atlas: Unbroken Threat
DolphinCape
Ukraine’s CERT says that a threat actor is using spear-phishing emails with lures related to Iran kamikaze drones to distribute a Delphi-based malware strain known as DolphinCape. Targets include Ukrainian government organizations. No official confirmation this is an APT campaign, but let’s be candid here—what else could this be? Read more: Кібератака на державні організації з використанням тематики іранських дронів-камікадзе Shahed-136 та шкідливої програми DolphinCape (CERT-UA#5683)
Medical lab vulnerability
BishopFox researchers found a vulnerability in the servers of Avicena Medical Laboratory, a Bosnian healthcare organization, which allowed researchers to get access to COVID-19 patient records just by querying a publicly exposed API. Researchers said they obtained details for more than 160,000 patients using this vulnerability. Read more: 160K COVID-19 Records: Vulnerability in Avicena Medical Laboratory
Dirty Vanity technique
At the Black Hat Europe 2022 security conference last week, researchers from Deep Instinct presented details about Dirty Vanity, a new code injection technique. A public proof of concept is available here. Read more: Dirty Vanity: A New Approach to Code Injection & EDR Bypass
“This technique abuses the lesser-known [process] forking mechanism which is built in Windows operating systems.”
Vulnerability does not compute
VulnCheck researcher Jacob Baines has discovered that CVE-2022-28958, a vulnerability in D-Link routers, does not actually exist. This didn’t stop the Moobot botnet from integrating an exploit for it and obviously failing to infect any devices with it.\
“We conclude that CVE-2022-28958 is not a real vulnerability and at-scale exploitation has never occurred. The vulnerability should not be listed by MITRE, and it should not be in the CISA Known Exploited Vulnerabilities Catalog. We filed a dispute with MITRE and shared our findings with CISA in October 2022.”
Google One VPN security audit
A security audit of the Google One VPN service conducted by the NCC Group has identified 22 vulnerabilities across the VPN’s desktop and mobile apps, libraries, and architecture. The UK-based security assurance firm said that while “no significant risks were identified in this assessment,” the found issues should be addressed to ensure a robust defense and in-depth design. Read more: Public Report – VPN by Google One Security Assessment
Updated on 2022-12-09
The Hive ransomware gang has been extremely active throughout the year, stealing and posting data from its victims. A French sports company became the latest victim of this threat. An HR and payroll management company recently informed its corporate and individual customers of a data breach that exposed their information. In other news, the HHS issued a warning about another ransomware, which is relatively new but has already caused quite some disruption. Read along for the top 10 highlights from the past 24 hours.
More highlights from the past 24 hours
- Threat Fabric researchers spotted Zombinder, a third-party darknet service used to embed malicious payloads in legitimate Android apps, resulting in victims infecting themselves. Read more: Zombinder: new obfuscation service used by Ermac, now distributed next to desktop stealers
- Researchers found that common misconfigurations arising from how DNS is implemented in an environment can put air-gapped networks and high-value assets at risk. Read more: Report: Air-Gapped Networks Vulnerable to DNS Attacks
- Web Explorer – Fast Internet, an Android browsing app, left a Firebase instance open, exposing days’ worth of app and user data, including hardcoded sensitive information. Read more: Android app with over 5m downloads leaked user browsing history
- Threat-informed defense surface management platform Interpres Security emerged from stealth with $8.5 million in seed funding round, led by Ten Eleven Ventures. Read more: Interpres Security emerges from stealth and raises $8.5 million
Updated on 2022-12-08
Fake investment scams have become a quite lucrative business among cybercriminals. One such group stole over half a billion dollars from victims across several European countries. Remember that CommonSpirit breach in October? Further investigation revealed that a greater number of patients have been infected. In another vein, an Iranian threat actor was found using a data wiper against diamond companies. Read along for more updates from the cyberspace.
More highlights from the past 24 hours
- CryptosLabs, a previously unknown investment scam gang, raked in over $505 million from victims in Belgium, France, and Luxembourg, since its inception in 2018. Read more: Anatomizing CryptosLabs: a scam syndicate targeting French-speaking Europe for years
- Several Cincinnati restaurants suffered cyberattacks, resulting in the theft of thousands of dollars. The hackers hacked into their social media accounts. Read more: ‘It was instant panic’: Cincinnati restaurants under attack by cyber hackers
- New research by Sophos stated that scammers have lost more than $2.5 million to other scammers in criminal forums and marketplaces, in the past 12 months. Read more: The scammers who scam scammers on cybercrime forums: Part 1
- Security compliance and automation platform Drata raised $200 million in Series C funding round co-led by Iconiq Growth and GGV Capital. Read more: Security compliance and automation platform Drata nabs $200M at $2B valuation
- Ireland-based encryption-as-a-service provider Vaultree raised $12.8 million in Series A funding led by Molten Ventures and Ten Eleven Ventures. Read more: Vaultree raises $12.8M to let companies more easily work with encrypted data
Updated on 2022-12-07
Right after hackers attacked the Zwijndrecht police, another group hit the Belgian city of Antwerp, causing mass disruption. In other news, researchers found a Chinese APT gang behind attacks against a telco in the Middle East. Also, if you are following Elon Musk or any related accounts on Twitter, be careful of a new crypto giveaway scam. Here are the top 10 highlights from the past 24 hours.
More highlights from the past 24 hours
- Twitter accounts following Elon Musk, SpaceX, and Tesla are being targeted in a new crypto giveaway scam—Freedom Giveaway—with a fake promise of receiving up to 5,000 Bitcoins. Read more: Elon Musk “Freedom Giveaway” crypto scam promoted via Twitter lists
- Russian state-owned VTM Bank, the second-largest financial institution in the country, confirmed going through the largest DDoS attack in its history. Read more: Russia’s second-largest bank VTB Bank reveals it is facing the largest DDoS (distributed denial of service) attack in its history.
- Senhasegura, Brazilian privileged access management solutions provider, raised $13 million in Series A funding, led by Graphene Ventures. Read more: Brazilian PAM Company Senhasegura Raises $13 Million
- Cloud identity protection platform Rezonate closed an $8.7 million seed funding round, led by State of Mind Ventures and Flybridge. Read more: Rezonate raises $8.7M and launches its cloud identity protection platform out of stealth
Threema’s new Ibex protocol
E2EE instant messaging service Threema has launched a new cryptographic protocol suite named Ibex. The new protocol supports Perfect Forward Secrecy, and Threema said it worked with external cryptographers for more than 18 months to make the protocol “future proof.” In addition to deploying Ibex, Threema said it also added E2EE support for group calls, something that very few secure messaging services currently support. Read more: New Communication Protocol “Ibex” and Extended Protocol Suite
EU funds Cyber Lab in Ukraine
The EU has financed and delivered software and hardware equipment for the creation of a cyber lab inside the Ukrainian Armed Forces. The lab will allow Ukraine to train military cyber defense professionals in a virtual environment using real-time simulations. The lab was formally unveiled in Kyiv last week, and EU officials hope it will help Ukraine’s military detect and respond to cyberattacks faster and more efficiently. Read more: Ukraine: EU sets up a cyber lab for the Ukrainian Armed Forces
ANSSI boss leaves post
Guillaume Poupard, the director of France’s cybersecurity agency ANSSI, said he’s leaving his post at the end of the year after almost nine years in the role. Poupard announced his departure on LinkedIn. A day before, Arne Schönbohm, the chief of Germany’s BSI intelligence service, also said goodbye to his colleagues on LinkedIn after being dismissed following a political scandal. Read more: „Schneller Präsidentenwechsel“Oberster Cyber-Boss wird nach Böhmermann-Recherche abgelöst
Dutch SIM swapper gets four years
A 20-year-old from the Dutch town of Eelderwolde was sentenced to four years in prison for breaking into the IT systems of Dutch mobile operator T-Mobile. Officials said the man worked with a 17-year-old and executed spear-phishing and SIM-swapping attacks to break into bank accounts and steal more than €100,000 from dozens of victims. Read more: Vier jaar cel voor jonge cybercrimineel uit Eelderwolde
IRS fraudsters arrested
The US Department of Justice has announced the arrest of four suspects, three Nigerians and one UK national, on charges related to identity fraud and filing fraudulent tax returns on behalf of US citizens and businesses. US officials said the suspects used the xDedic cybercrime marketplace to buy access to servers operated by US companies, stole PII data stored on these systems, and then filed fraudulent tax returns seeking huge payouts on behalf of the victims. The suspects were detained in the UK and Sweden in November and December, and DOJ officials said they are working to have them extradited to the US. Read more: Four Men Arrested In Transnational Wire Fraud And Identity Theft Conspiracy
Money launderers arrested
Europol and law enforcement across 25 countries have detained 2,469 suspects as part of an international crackdown against money mule gangs. Suspects were detained in Europe, but also in countries as far as Colombia, Singapore, and Australia. Europol said they also seized €17.5 million from the suspects and prevented the funds from being laundered. Read more: 2469 money mules arrested in worldwide crackdown against money laundering
New npm malware
Thirteen new malicious npm packages were spotted on Monday. Check out GitHub’s security advisory portal for details.
IoT malware evasion techniques
Nozomi researchers have a summary of recent techniques used by IoT malware strains to evade detection and reverse-engineering. Read more: How IoT Botnets Evade Detection and Analysis – Part 2
DanaBot
Zscaler has an analysis of the DanaBot malware and its infamously advanced obfuscation techniques. Read more: Technical Analysis of DanaBot Obfuscation Techniques
AndroxGh0st
Cloud security company Lacework says it discovered a new threat actor group named Xcatze that uses a Python named AndroxGh0st to take over AWS servers and send out massive email spam campaigns. Lacework says the malware operates by scanning web apps written in the Laravel PHP framework for exposed configuration files to identify and steal server credentials. Researchers said AndroxGh0st specifically searches for AWS, SendGrid, and Twilio credentials, which it uses to take control of email servers and accounts and send out the spam campaigns. Read more: AndroxGh0st – the python malware exploiting your AWS keys
ChatGPT tools
Stairwell security researcher Daniel Mayer and Kaspersky researcher Ivan Kwiatkowski have released IDA Pro plugins that use the ChatGPT algorithm to explain decompiled functions. A big warning that these explanations may not be accurate, a warning that should be taken very seriously since StackOverflow has banned ChatGPT-generated answers on its platform due to the large number of inaccuracies in most posts. Read more: Temporary policy: ChatGPT is banned
New tool—SandboxSecurityTools
Microsoft has released a collection of tools that security researchers can use to test sandbox technologies the company uses for its Windows OS.
New tool—GCPGoat
Online learning platform INE has open-sourced GCPGoat, an intentionally vulnerable-by-design GCP setup that can be used by security professionals to test their skills and learn to detect misconfigurations and vulnerable systems. The company has released similar tools for Azure and AWS infrastructure as well.
Updated on 2022-12-06
The U.S. government acknowledged that Chinese hackers stole millions in state unemployment funds – the first pandemic fraud connected with foreign cybercriminals. In another vein, hackers are selling 1.1 million records belonging to Israeli firms on clear web forums for quite a hefty price. Remember the new Cryptonite ransomware? Researchers discovered that it functions as a data wiper too – an accident on the threat actors’ part. Read along for more highlights from the past 24 hours.
More highlights from the past 24 hours
- A group of hackers were found selling a hoard of 50GB of data for sale on two forums with a price tag of 1BTC per database. The data belongs to 29 Israeli transportation, logistics services, and forwarding firms. Read more: Data of Israeli Employees from 29 Logistics Firms Sold Online
- A new report by Lupovis disclosed that Russian hackers compromised the networks of 15 healthcare organizations, a dam monitoring system, and others in the U.K and the U.S. to launch cyberattacks against Ukraine. Read more: Russia compromises major UK and US organisations to attack Ukraine
- CloudSEK published a new advisory warning against the Team Mysterious Bangladesh hacker group that claims to have compromised the Indian Central Board of Higher Education (CBHE) systems. Read more: Indian Central Board of Higher Education Compromised by Team Mysterious Bangladesh
- An advanced cyberespionage campaign, allegedly conducted by an Iranian state-sponsored group, was found targeting journalists, diplomats, politicians, and human rights activists working in the Middle East. Read more: Iranian espionage campaign targets journalists, diplomats, activists, says Human Rights Watch
Updated on 2022-12-05
Every day, some new malware is spotted on the Android app store. Researchers found several new malicious apps downloaded over two million times. While we are on the topic of malicious apps, Lazarus is propagating malware via fake crypto apps. We also have the latest DeFi hack wherein the hacker made a pretty buck. Read along for everything from the weekend.
More highlights from the past 24 hours
- Dr. Web researchers spotted a new set of Android adware, malware, and phishing apps on the Google Play Store with over two million installations. Read more: Android malware apps with 2 million installs spotted on Google Play
- A hospital center in Versailles, France, confirmed suffering a cyberattack that limited patient reception and cut off all computer networks. Read more: Versailles hospital targeted by cyberattack
- An IT failure in a newly launched Dutch app, by the political party Forum voor Democratie, exposed the names, addresses, and bank details of 93,000 current and former party members. Read more: FvD data leak leaves 93,000 members and former members exposed
- As per a Capterra report, 67% of healthcare cyberattacks affect patient data while 48% affect patient care. Read more: Connected medical devices are the Achilles’ heel of healthcare orgs
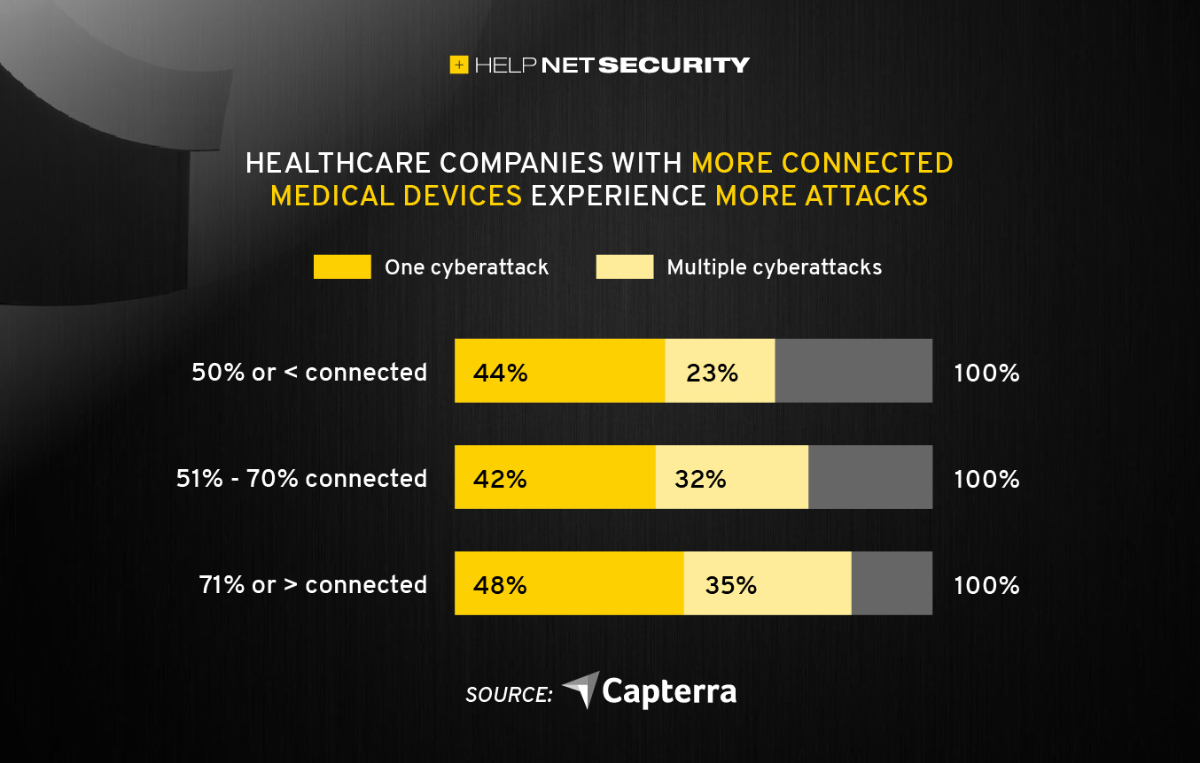
- A cybersecurity incident hit the offices of the San Diego Unified School District, disrupting its computer network. Additional update will be provided once investigation concludes. Read more: ‘Cybersecurity incident’ hits San Diego Unified computer network
CoinTracker email leak
Cryptocurrency wallet CoinTracker said that a compromise of one of its service providers exposed a list of customer emails and referral links. CoinTracker said no other personal data was exposed and that hackers did not gain access to any of its infrastructure.
ARSAT incident
ARSAT, an Argentinian state-owned terrestrial and satellite telecommunications provider, said it suffered a security breach of its corporate network. Although the incident took place right before the Argentina-vs-Poland World Cup soccer match, ARSAT said customer service was not disrupted by the attack.
Beeline hack
Hackers have leaked the personal information for thousands of Beeline employees. Beeline—one of Russia’s largest mobile telecommunications providers—confirmed the leak to Russian news outlet Vedomosti. The hackers claimed they obtained the data after accessing one of the company’s internal LDAP servers. The same group previously leaked data from other major Russian organizations, such as the Russian state-owned postal service, travel booking platform Tutu, delivery service DeliveryClub, and online learning platform GeekBrains. Read more: Информация о сотрудниках «Билайна» утекла в сеть
Chrome Enhanced Protection
In its quarterly report for Q3 2022, the Chrome security team said they saw a 16% quarter-over-quarter growth in the number of Chrome users who opted into the Enhanced Safe Browsing Protection feature. In addition, Google said they also revamped rules and increased payouts for the Chrome bug bounty program, which resulted in an increase in submissions that contained functional exploits and bisections (where the bug reporter points out the specific commit or commit range where the bug was introduced in the Chrome source code). Read more: Manage Enhanced Safe Browsing for your account
UK MSP regulation
The UK government has introduced new mandatory reporting rules for managed service providers (MSPs). Following an update to its NIS regulation, the UK government says that MSPs have become an unofficial part of most of the UK’s critical infrastructure, and just like most operators in this field, they will have to report all cybersecurity-related incidents that disrupt their infrastructure and the services of their customers. Besides new reporting rules to government agencies like Ofcom, Ofgem, and the ICO, MSPs will also have to follow a set of basic cybersecurity standards to ensure their systems are protected against common attacks. Organizations that fail to follow the new rules could be fined up to £17 million ($20.9 million), the government said. Read more: Press Release: Cyber laws updated to boost UK’s resilience against online attacks
Fidesz abused government data for political spam
A report from Human Rights Watch says that Hungary’s ruling political party Fidesz has abused personal data stored in government databases to send political-themed spam to citizens in this year’s parliamentary elections. HRW says that data from the country’s COVID-19 vaccine signups and tax benefits applications was pilfered by Fidesz officials and then bombarded with political campaign messages. The party’s entire campaign was fraught with abuses, and international observers noted that Fidesz abused its control over government resources to break campaign financing rules and restrict the opposition’s air time. Read more:
Coordination between Russian kinetic and cyberattacks
Microsoft said it is continuing to see “strong circumstantial evidence” that Russia is coordinating cyberattacks and military kinetic operations in Ukraine. In a report published on Friday, Microsoft said they saw destructive malware deployed in Ukrainian regions that were often hit by missile strikes a few days later. The report covers operations that took place in October 2022, and is the third report Microsoft published this year—after one in April and then June—where the company saw the same pattern of Russia deploying destructive malware before launching military operations. Read more:
- Preparing for a Russian cyber offensive against Ukraine this winter
- The hybrid war in Ukraine
- Defending Ukraine: Early Lessons from the Cyber War
Black Panthers gang
Authorities in Spain have detained 55 members of the Black Panthers cybercrime gang, a group suspected of stealing more than €250,000 from more than 100 victims. Spanish police said the Black Panthers operated out of Barcelona, and the gang was split into multiple cells, each specialized on one single task, such as phishing, vishing, carding, social engineering, and SIM-swapping attacks. The group’s leader was also detained in the recent raids. Read more: La Policía Nacional desarticula una organización criminal dedicada a las estafas bancarias mediante SIM swapping
SIM swapper gets 18 months
A New York judge has sentenced Florida man Nicholas Truglia to 18 months in prison for helping launder more than $20 million worth of stolen cryptocurrency. The Justice Department said Truglia made his cryptocurrency wallet available to a group of SIM swappers, which then used it to send stolen funds and then redirect the profits to their own accounts. US officials said Truglia’s account was used to launder $20 million, of which he kept $673,000 for himself. Read more: Florida Man Sentenced To 18 Months For Theft Of Over $20 Million In SIM Swap Scheme
$140 million revenue
A team of academics says that data they collected from 30 dark web underground markets over a period of eight months suggests that cybercrime groups made roughly $140 million from the sale of stolen data. The report, published in January this year, compiled data from 96,672 ads placed by 2,158 vendors across the dark web’s largest markets. Academics say marketplaces had 26,342 sales and generated $5,847,417 in revenue on average, but a large part of the profits was concentrated in a few hotspots, such as Agartha ($91 million), Cartel ($31 million), and DeepMart ($9 million). Read more:
- The Network of Online Stolen Data Markets: How Vendor Flows Connect Digital Marketplaces
- Darknet markets generate millions in revenue selling stolen personal data, supply chain study finds
$3.3 billion in crypto stolen
Blockchain security firm PeckShield said roughly $391 million worth of cryptocurrency funds were stolen in November 2022, bringing this year’s total to more than $3.37 billion so far.
Pass-the-Cookie attacks
Netwrix has a basic breakdown of a Pass-the-Cookie attack. These types of attack is seeing broader adoption by phishing kits, as it allows them to steal cookies via phishing sites, not only just the user’s credentials. These authentication cookies are then used to bypass 2FA protections. Read more: Bypassing MFA with the Pass-the-Cookie Attack
BlackProxies
DomainTools researchers have a report out on BlackProxies, a malicious proxy service that has been gaining adoption in the cybercrime underground. The service claims to have access to more than one million residential IP addresses, which it offers to rent out to cybercrime gangs to help disguise their malicious operations. Read more: Purpose Built Criminal Proxy Services and the Malicious Activity They Enable
New npm malware
Five new malicious npm packages spotted. Check out GitHub’s security advisory portal for details.
Conti gang
Chinese security firm has a report out on the Conti ransomware gang and some of its recent attacks that leveraged an Exchange vulnerability to breach corporate networks. Read more: Operation(верность)mercenary:陷阵于东欧平原的钢铁洪流
Titan Stealer
OALABS has TTPs and IOCs for the new Titan Stealer malware.
Influence operations
Google’s TAG security team has published a summary of the coordinated influence operation campaigns terminated on Google platforms in Q4 2022 (so far). The biggest takedowns this quarter were linked to China (5,197 YouTube channels and 17 Blogger blogs) and Russia (783 YouTube channels, 5 AdSense accounts, and 2 Google News domains), as always, but also one influence op in Brazil that was propping up Jair Bolsonaro’s campaign. Read more: TAG Bulletin: Q4 2022
Artifact poisoning
Researchers from Legit Security have published a report on a new technique called Artifact Poisoning that can be used to modify a GitHub project’s resources using the GitHub Actions feature. Researchers said the technique is useful for carrying out supply chain attacks.
“We have discovered that when transferring artifacts between different workflows, there is a major risk for artifact poisoning – a technique in which attackers replace the content of a legitimate artifact with a modified malicious one and thereby initiate a supply chain attack. This is similar to the CodeCov supply chain breach, where attackers put a backdoor into one of Codecov’s artifacts which were later used by users to update their software and thereby got hacked.”
Visual Studio Code RCE
Microsoft has fixed a major vulnerability in its Visual Studio Code service that could have been used for remote code execution on the web and desktop versions of Visual Studio Code. Read more: Visual Studio Code: Remote Code Execution
Hell’s Keychain
Cloud security firm Wiz discovered a vulnerability that allowed them to access the internal infrastructure of IBM Cloud. Wiz says they could have modified the company’s CI/CD pipeline and poison artifacts deployed in the company’s production-ready PostgreSQL environments. IBM has patched the vulnerability, which Wiz named Hell’s Keychain. IBM said it was aware of Wiz’s actions at all times, and no customer data was ever in danger. Read more:
- IBM Cloud Databases for PostgreSQL was affected by a security vulnerability
- Hell’s Keychain: Supply-chain vulnerability in IBM Cloud Databases for PostgreSQL allows potential unauthorized database access
CertPotato attack
Orange’s SensePost team has a report out on CertPotato, a new privilege escalation attack for elevating virtual and network service accounts to NT AUTHORITY\SYSTEM. The attack abuses the Windows Active Directory Certificate Service (ADCS). Read more: CertPotato – Using ADCS to privesc from virtual and network service accounts to local system
Updated on 2022-12-04
ICE in hot water
U.S. immigration enforcement accidentally released the identities — including names, nationalities and detention locations — of more than 6,200 immigrants who have fled torture and persecution and are seeking asylum to the United States. ICE said that the exposure was caused by a “routine” website update and lasted five hours. A Homeland Security official told the Los Angeles Times that the disclosure was potentially dangerous for those affected. Immigrant advocacy group Human Rights First first notified ICE of the data breach. Read more: ICE accidentally released the identities of 6,252 immigrants who sought protection in the U.S.
Updated on 2022-12-02
How far can cyberattacks impact educational institutions? A South Jersey school district was forced to cancel classes multiple days in a row, among other things. Even the Pope isn’t safe from hackers as the official Vatican website had to be taken down. In a latest revelation, a joint advisory by federal authorities disclosed some interesting stats about the Cuba ransomware. Here are the top 10 highlights from the past 24 hours.
More highlights from the past 24 hours
- The Gloucester County school district, New Jersey, had to cancel its classes three days in a row, owing to technical issues caused by unauthorized access by a third party. Read more: Internet issues caused by ‘unauthorized third party’ close South Jersey school
- Passwordless MFA provider HYPR raised $25 million in Series C1 led by Advent International, with participation from RRE Ventures, Top Tier Capital, and others. Read more: HYPR raises $25 million to reduce reliance on passwords
- API-first cybersecurity platform Pangea Cyber raised $26 million in Series B led by Google Ventures, with participation from Okta Ventures and Decibel. Read more: Investors Double Down on Pangea Cyber API Security Bet
Updated on 2022-12-01
Breaches at one company can and often do cascade to other firms associated. Something like this happened to LastPass, which has already suffered another major data breach this year. These are indeed risky times for Android users as a new campaign is attempting to steal their Facebook credentials. Medibank hackers finally dumped every bit of data they had in their possession and closed the case, or so they said. Read along for more from the past 24 hours.
More highlights from the past 24 hours
- McAfee analyzed a new payment fraud malware targeting mobile payment users in Japan by pretending to be a legitimate mobile security app on the Google Play Store. Read more: Fake Security App Found Abuses Japanese Payment System
Guatemala ransomware attack
The Guatemala government says it is investigating a ransomware attack that impacted the IT network of the Ministry of Foreign Affairs. The Ministry’s data was added to the leak site of the Onyx ransomware group on September 27 and was added again on November 21. Read more: Guatemala’s Foreign Ministry investigating ransomware attack
Nomad Bridge hack
Google’s Mandiant has a post-mortem report on the bug that led to the very “public” hack of the Nomad Bridge cryptocurrency exchange. Read more: Decentralized Robbery: Dissecting the Nomad Bridge Hack and Following the Money
Google sues review scammer
Google has filed a lawsuit against the owners of an online service called G Verifier that was allegedly defrauding small businesses by impersonating Google in telemarketing calls. Google said G Verifier was calling small business owners and offering to set up Google Business Profiles, a service that Google was providing for free. In addition, Google said that G Verifier agents also offered to provide fake reviews on the Business Profiles and boost a company’s reputation. The lawsuit also alleges that G Verifier also ran websites that sold fake reviews, either positive or negative, to manipulate a company’s business profile in Google Search results and Google Maps listings. Read more: Protecting small businesses from scammers
Amazon Security Lake
Amazon has launched a new product called Security Lake, a service that can aggregate security feeds and data from cloud systems, on-premises, and custom sources, to help security teams have a better view of their security posture and threat levels. The service is currently in preview. Read more: Introducing Amazon Security Lake (Preview)
US shoots down US-Cuba subsea cable
The US Department of Justice advised the Federal Communications Committee to deny the application of two US telecom companies to build a subsea cable system to link the United States with Cuba. The DOJ says that its vision for the internet is for “an open, interoperable, secure, and reliable” system, which the Cuban government does not share. More from Assistant Attorney General Matthew G. Olsen of the Justice Department’s National Security Division. Read more: Team Telecom Recommends the FCC Deny Application to Directly Connect the United States to Cuba Through Subsea Cable
“As long as the Government of Cuba poses a counterintelligence threat to the United States, and partners with others who do the same, the risks to our critical infrastructure are simply too great.”
South Dakota bans TikTok
South Dakota Governor Kristi Noem has banned the use of the TikTok mobile application on devices of state employees and contractors. Noem said the ban is the state’s response “to the growing national security threat posed by TikTok due to its data gathering operations on behalf of the Chinese Communist Party (CCP).” Read more: Gov. Noem Signs Executive Order Banning TikTok
Albania charges five government workers
Prosecutors in Tirana have charged and asked for the house arrest of five government employees in connection to an investigation of a series of cyberattacks carried out by Iranian state-sponsored hackers that crippled multiple Albanian government systems in July this year. Prosecutors say the accused failed to apply security updates to government systems and also failed to detect that hackers had been in their network as far back as April 2021. Albania cut diplomatic ties with Iran following the incident and also considered invoking NATO’s infamous Article 5 over Iran’s actions. Read more: Albania Prosecutors Seek to Grill Five Officials Over Cyber-attacks
Dutch emergency warning
The Dutch government just told its citizens to stock up on food and medicine in the case of a national emergency, which also includes the likes of a debilitating cyber attack. Also, a nuclear attack. Thanks for the apocalyptic reminder, but a Happy Holidays would have sufficed! Read more: Denkvooruit.nl biedt informatie over voorbereiden op noodsituaties en crises
NSO sued by journalists
Fifteen journalists, along with members of El Faro, an independent news agency in Central America, filed a lawsuit in a US court against Israeli spyware maker NSO Group. The lawsuit alleges that NSO Group broke multiple laws, including the US Computer Fraud and Abuse Act (CFAA), when it designed and then helped deploy the Pegasus spyware on the devices of El Salvador journalists and human rights activists. Read more:
- El Faro Journalists, Knight Institute Sue NSO Group Over Spyware
- Project Torogoz – Extensive Hacking of Media & Civil Society in El Salvador with Pegasus Spyware
“The plaintiffs are filing the lawsuit in the same district in which two other lawsuits have been filed against NSO Group: one by Apple and one by WhatsApp. The Supreme Court is expected to decide imminently whether to grant a cert petition filed by NSO Group in the WhatsApp case.”
Insivible npm packages
JFrog researchers have found that several of the security tools built inside the npm CLI fail to show warnings for any malicious library that contains a dash or hyphen in their version number, in the form of 1.2.3-a. Read more: Invisible npm malware – evading security checks with crafted versions
WordPress backup scans
Wordfence says that it detected more than 70 million scan events of threat actors probing WordPress sites and looking for backup archives. Wordfence says that backup files often contain credentials to access a WordPress site and its database, which makes them ideal targets for threat actors looking to hijack and backdoor an unprotected website. Read more: Configuration Probing: Your Backups Might Be Your Greatest Weakness
Malspam trends
HP’s Wolf Security says that archive files have almost surpassed spreadsheets as the preferred method of delivering malspam in the second quarter of 2022—per its quarterly threat report. Read more: HP Wolf Security Threat Insights Report Q3 2022
Xiongmai exploitation
Threat intelligence company VulnCheck has a very interesting write-up about seven vulnerabilities in Xiongmai IoT devices, five of which have been exploited in the wild. Although the attacks have gotten little attention, VulnCheck believes they should, as there are more than 200,000 Xiongmai devices connected to the internet that can be ideal cannon fodder for botnets and initial access brokers. Read more: Xiongmai IoT Exploitation
TAG-56
Recorded Future says it spotted a spear-phishing campaign conducted by TAG-56, a cyber-espionage group the company considers to have an Iran nexus. The campaign took place in early November and targeted a Washington think tank using email lures related to the 2022 Sir Bani Yas Forum, an economic forum hosted by the government of the United Arab Emirates (UAE). Read more: Suspected Iran-Nexus TAG-56 Uses UAE Forum Lure for Credential Theft Against US Think Tank
Operation ShadowTiger
The same QiAnXin team has a second report out on Operation ShadowTiger, a series of attacks carried out by an East Asian APT group they call Tiger Hibiscus, or APT-Q-11. The campaign took place from 2019 to 2021 and involved the use of spear-phishing, (browser and intranet) zero-days, and an intranet watering-hole attack. Read more: Operation(호랑이머리깃발)ShadowTiger:盘踞在佛岩山上的过林之虎
Metador’s Mafalda
SentinelOne has published a technical breakdown of Mafalda, a malware implant used by the mysterious Metador APT. Read more: The Mystery of Metador | Unpicking Mafalda’s Anti-Analysis Techniques
Linux vulnerability
Qualys researchers have found a race condition vulnerability (CVE-2022-3328) in one of the default packages installed on several Linux distros, including the highly popular Ubuntu. Read more: Snapd Race Condition Vulnerability in snap-confine’s must_mkdir_and_open_with_perms() (CVE-2022-3328)
Huawei hypervisor vulnerability
More than a year after it was patched, Impalabs has published details on CVE-2021-39979, a vulnerability that can be used to execute malicious code inside the secure hypervisor used by Huawei’s HarmonyOS mobile operating system. Impalabs discovered the vulnerability during their extensive research of the HarmonyOS security hypervisor. Read more:
iOS updates
Apple has also released iOS 16.1.2, which the company marked as a security update, so make sure to update.
Snyk vulnerabilities
There are also two code injection vulnerabilities in the Snyk CLI and IDE plugins, two popular source code-checking utilities. Read more: Code injection vulnerabilities (CVSSv3 5.8) found in Snyk CLI and IDE plugins
Hive Social vulnerabilities
Researchers have found several vulnerabilities in Hive Social, one of the many social networking apps that have popped up as Twitter replacements. The vulnerabilities can allow attackers to access a user’s private data, including private posts, private messages, shared media, and deleted DMs. Shortly after researchers publicly disclosed their findings and said that Hive Social lied about fixing the issues, the company announced it was temporarily shutting down servers for the upcoming days to finally address the vulnerabilities. Read more: ⚠️ Warning: do not use Hive Social 👉🐝👈
Vulnerabilities in remote keyboard apps
Synopsys researchers said they found seven vulnerabilities across three Android apps that can be used as remote keyboards for a user’s computer. The research team says the vulnerabilities can be used to intercept keystrokes and/or run malicious code on connected computers. The three apps are named Lazy Mouse, Telepad, and PC Keyboard, and they have more than two million combined downloads via the Google Play Store. None of the app developers replied to Synopsys’s reports, and the vulnerabilities remain unpatched. Read more: CyRC Vulnerability Advisory: Remote code execution vulnerabilities in mouse and keyboard apps
Delta Electronics vulnerabilities
Austrian cybersecurity firm CyberDanube has helped patch several vulnerabilities in Delta Electronics wireless devices, typically deployed in industrial networks to provide internet connectivity for ICS/SCADA equipment in remote locations. Read more:
- [EN] AUTHENTICATED COMMAND INJECTION IN DELTA ELECTRONICS DVW-W02W2-E2
- [EN] MULTIPLE VULNERABILITIES IN DELTA ELECTRONICS DX-2100-L1-CN
OT vulnerabilities
Security firm Forescout says it found and helped patch three vulnerabilities impacting industrial equipment. The vulnerabilities impact the Festo automation controllers and the CODESYS runtime. The two Festo vulnerabilities allow unauthenticated reboots of devices, which could pose a big physical security risk in some industrial networks. Read more: OT:ICEFALL Continues: Vedere Labs Discloses Three New Vulnerabilities Affecting OT Products – How to Mitigate
AllInfosecNews
Looking for an aggregator for infosec news, podcasts, videos, and jobs? Meet AllInfosecNews from Foorilla. This is an ideal default browser homepage.
Black Hat USA 2022 videos
Talks from the Black Hat USA 2022 security conference, which took place in August, are finally out and available on YouTube. Enjoy!