Table of Contents
- Updated on 2022-11-30
- More highlights from the past 24 hours
- Updated on 2022-11-29
- More highlights from the past 24 hours
- Facebook fined €265 million
- EDF fine
- South Korean cyber sanctions
- AIVD threat actor assessment report
- CYBERCOM hunt forward operations in Ukraine
- Scam group detained in Spain
- EmBEARassment Disclosures
- ArvinClub evolution
- UK Crypto-fraud on the rise
- KEV update
- Botnet creation app
- CashRewindo
- New DFIR Report analysis
- Laplace Clipper
- Acer Secure Boot bypass
- Swatting incident
- Updated on 2022-11-28
- More highlights from the past 24 hours
- No WhatsApp breach
- More Windows 11 protections
- Digital sovereignty
- Defense Cyber Index
- Darknet market takedown
- Russian scammer gang detained
- Malicious Docker Hub images
- Potao source code
- Infostealer fingerprinting
- New npm malware
- Twitter amnesty watch
- Zanubis
- Koxic and Wiki
- APT-C-09
- CVE-2022-34721
- API security
- Updated on 2022-11-27
- A leak details Apple’s secret dirt on security startup Corellium
- Need a laptop repair? Don’t count on your privacy
- Indictments stand for French spyware maker
- Meta links pro-U.S. influence campaign to U.S. military
- Tax filing sites sent your data to Facebook
- Updated on 2022-11-25
- Guadeloupe cyberattack
- Westmount ransomware attack
- Don’t cyberattack here, plz
- Voting machine bug
- Cybersecurity Apprenticeship Sprint
- Operation HAECHI III
- Hacking back
- Birdsite security issues
- Hey, Google
- Bahamut APT
- CVE-2022-40300
- Argent vulnerability
- ENISA investments report
- Updated on 2022-11-24
- More highlights from the past 24 hours
- Ransomware Dominates UK Government Crisis Meetings
- Updated on 2022-11-23
- More highlights from the past 24 hours
- Updated on 2022-11-22
- More highlights from the past 24 hours
- Italy tracks and redirects entire ISP traffic
- Rewards for Russian hacktivists
- US State Department security audit
- CISA IRPF update
- NSO’s Supreme Court case
- Lurk leader has sentenced reduced
- Russian cybercrime investigation
- REvil investigation stalls
- Freebie Bots
- OMG!OMG! Market
- Karakrut starts recruiting
- Nighthawk C2 framework
- RobinBot
- Tofsee
- AWS vulnerability
- CVE-2022-41924
- Black Friday deals
- CISA on Mastodon
- LABScon 2022 videos
- IRISSCON 2022 videos
- 5G network security breaches
- AWS Nitro System
- Meta improves privacy on children’s accounts
- More Apple privacy drama
- Updated on 2022-11-21
- More highlights from the past 24 hours
- e-Tugra certificate authority exposing internal systems to the internet
- New NSA center opens up to outside researchers
- Amazon poaches top U.K. cybersecurity official
- Google settles location tracking suit
- ID.me, but in four hours or more
- AGs ask FTC for online privacy regulation
- Iran info-op in Latin America
- Russian bill to seize cybercrime profits
- Hackers detained in South Korea
- DDoS attacks on DNS servers
- Malware on Telegram
- New npm malware
- Conti off-shoots
- GRU 26165
- Infineon vulnerability
- CVE-2022-35803
- CVE-2022-26696
- Acquisition news
- OpenSSF adopts S2C2F
- Project Spaceman
- New tool—MI-X
- ResponderCon 2022 videos
- Updated on 2022-11-18
- More highlights from the past 24 hours
- Hyundai fined
- Dom.ru leak
- Google and Microsoft services in French edu sector
- Ad-blocker apocalypse getting closer
- CNIL fines Discord
- Russia’s cyber forces underperformed
- Universal health code in China
- US-China cyber report
- Chinese hacker
- Two scammers sentenced
- Elastic’s threat landscape report
- Record number of DDoS attacks
- Malware on npm
- WatchDog
- Typhon Reborn
- HZ Rat
- Dagon Locker ransomware
- Zendesk vulnerabilities
- New tool—Orpheus
- Jamf acquires ZecOps
- 2022 Aspen Cyber Summit stream
- Updated on 2022-11-17
- More highlights from the past 24 hours
- Updated on 2022-11-15
- More highlights from the past 24 hours
- Updated on 2022-11-15
- More highlights from the past 24 hours
- ESET’s APT report
- XDSpy
- Mastodon gets its tires kicked
- Wi-Peep attack
- PCspoof vulnerability
- Crypto hacks and rugpulls
- Google fine
- Red Hat deploys cryptographic signatures
- Firefox 107
- Two GAO reports
- UAE
- EU EDPS LOL
- Italy bans facial recognition
- Zeus Tank detained
- Koxic & Key Group
- AcridRain Stealer
- Updated on 2022-11-14
- More highlights from the past 24 hours
- Updated on 2022-11-13
- New tool—Canary Hunter
- New tool—Shufflecake
- GitHub private vulnerability reporting
- CVE-2022-32895
- LiteSpeed server vulnerabilities
- BadBazaar
- Inlock and Xorist ransomware
- Free decrypter
- State of Massachusetts sued
- Mastodon abuse
- Attacks on US midterm elections infrastructure
- 17 scam domains seized
- Switzerland sees main “cyber threat” coming from ransomware
- Russian sanctions 200 US citizens
- EU Cyber Defence
- Apple sued for ignoring privacy settings
- Microsoft blocks domain fronting on Azure
- DFX Finance crypto-heist
- BAH breach
- Irish health system ransomware victims to be contacted
- Home truths about macOS
- Australia faces consequences of standing up to ransomware
- Updated on 2022-11-11
- More highlights from the past 24 hours
- Plesk vulnerability
- CVE-2022-41049
- Security updates
- TA423/Leviathan/RedLadon
- JSP web shell targeting Zimbra
- Crypto-mining landscape
- Scam gang disrupted in Ukraine
- Cyber.org Range expands nationwide
- Apple limits AirDrop in China
- Kaspersky to discontinue VPN service in Russia
- Compensation for Yandex.Food users
- Major breach in Hungary
- Updated on 2022-11-10
- More highlights from the past 24 hours
- Updated on 2022-11-09
- More highlights from the past 24 hours
- New tool—Microsoft Section52 ICS Forensics Tools
- New tool—Shennina
- New tool—SpyGuard
- Patch Tuesday
- Ukraine Cyber Project
- Unknown APT
- Elibomi variants
- Calls for DDOS attacks on US election day
- DeimosC2
- Former Deloitte employee behind FIFA hacks
- Hushpuppi sentenced
- Cyber-attack cripples Mexico’s transportation system
- Pando Rings crypto-heist
- Updated on 2022-11-08
- More highlights from the past 24 hours
- Updated on 2022-11-07
- More highlights from the past 24 hours
- Solend crypto-heist
- Successful defense
- Personal Paraguay hack
- Qatar spied on FIFA officials
- Armenian cyber-attacks
- NCCoE guidance
- UK DfE lapse
- ACSC threat assessment
- Atlantis Cyber Army
- Hamas expanding in cyber domain
- New Sudo vulnerability
- PrivacyCon 2022 videos
- NSA job openings
- IDA Pro community
- Updated on 2022-11-06
- The most vulnerable place on the planet
- Fizz threatened to sue student security researchers after finding bugs
- How two-factor works in Antarctica
- NSA watchdog says one analyst’s surveillance project went ‘too far’
- States look to secure U.S. election ‘weak points’ ahead of midterms
- Updated on 2022-11-04
- More highlights from the past 24 hours
- Ransomware attack cripples 75 German schools
- Ransomware cripples Polish hospital
- Skyward crypto-heist
- IP addresses as spoils of war
- Twitter InfoOps
- Microsoft extends help to Ukraine
- Russia’s search for a Windows replacement
- Tax fraud ring indicted
- Russian hacker released from prison
- Adware explosion
- ENISA threat landscape
- P2P botnets
- Robin Banks moves to Russia
- Crimson Kingsnake BEC gang
- OrcusRAT
- Elbie and Surtr ransomware
- Next.js vulnerability
- Intel 471 acquires SpiderFoot
- HUMAN acquires clean.io
- Updated on 2022-11-03
- More highlights from the past 24 hours
- Updated on 2022-11-02
- More highlights from the past 24 hours
- Apache Batik vulnerability
- Checkmk vulnerabilities
- Impersonate attack
- No Hat 2022 videos
- APT trends report
- PayPal bug exploited
- Phishing kit stats
- Azov wiper
- US Treasury ransomware stats
- New CISA guidance
- Ransomware summit
- Cisco disables Meraki networks in Russia
- Updated on 2022-11-01
- More highlights from the past 24 hours
Updated on 2022-11-30
Healthcare data breaches are getting out of hand, impacting millions of individuals every so often. One such breach at a pediatric health IT software company impacted over two million patients and their sensitive information. In another vein, a China-linked threat actor was found using USB devices for nefarious purposes. We also have an old ransomware in the garbs of a new one, which is not very sophisticated but is still a threat. Here are the top 10 highlights from the past 24 hours.
More highlights from the past 24 hours
- Connexin Software started notifying over 2.2 million individuals of a healthcare data breach in August, which impacted their SSNs, treatment information, and other personal information. Read more: Third-Party Data Breach Impacts 119 Pediatric Practices, 2.2M Patients
- The Netherlands-based software firm ENC Security had leaked critical business data, including API keys, digital certificates, and configuration files, from May 27, 2021, to November 09, 2022, found Cybernews. Read more: Sony and Lexar-trusted encryption provider leaked sensitive data for over a year
- At least one threat actor operating a Russian dark web forum has started selling access to several networks compromised by abusing a critical authentication bypass flaw in Fortinet technologies. Read more: Cyberattackers Selling Access to Networks Compromised via Recent Fortinet Flaw
- The Spanish National Police took down a cybercrime operation that leveraged fake investment sites to defraud 300 victims, across Europe, and steal over $12.8 million. Read more: Spanish police dismantle operation that made €12M via investment scams
- New Jersey-based cybersecurity startup Sphere Technology Solutions raised $31 million in Series B, led by Edison Partners, with Forgepoint Capital as a participant. Read more: Investors Bet $31 Million on Sphere for Identity Hygiene Tech
- CloudWave announced the acquisition of Sensato Cybersecurity, a cybersecurity-as-a-service platform, for an undisclosed sum. Read more: CloudWave acquires Sensato to expand its healthcare cybersecurity portfolio
Updated on 2022-11-29
The education sector is being constantly targeted by ransomware actors. Today, we have two schools that fell victim to cyberattacks that disrupted operations and compromised sensitive information. Have you heard of the invisible man challenge on TikTok? Attackers have started using even that to their advantage. Read along to know what transpired in the past 24 hours.
More highlights from the past 24 hours
- The Durham District School Board (DDSB), Ontario, confirmed suffering a cyberattack that disrupted the school’s access to email and phone services, along with emergency contact. Read more: DDSB recovering from cyber attack that left schools without access to email or emergency contact information
- Group-IB tracked over 16,000 scam domains and 40 malicious apps on the Google Play Store abusing the FIFA World Cup in Qatar to target fans. Read more: Experts Find 16,000+ Scam FIFA World Cup Domains
- Binarly researchers discovered that Dell, HP, and Lenovo are still using outdated versions of the OpenSSL cryptographic library, posing a risk to the supply chain. Read more: Dell, HP, & Lenovo System Found Using Outdated OpenSSL Cryptographic Library
- Latest research by Akamai disclosed that the number of API and web app attacks on the financial services sector increased by 3.5 times year-on-year in the past 12 months. Read more: Web App and API Attacks Surge 257% in Financial Services
- A fake Android app on the Google Play Store was found acting as a secret relay for account creation services for Microsoft, Google, Facebook, and others. It has garnered 100,000 downloads. Read more: Malicious Android app found powering account creation service
- Law enforcement across 27 countries, along with Europol, took down 12,526 websites hosting illegal content related to counterfeiting and online piracy. Read more: Police Shutter 13,000 Sites in Piracy Crackdown
- The Australian government awarded up to $25.4 million in grants under the second round of the Cyber Security Skills Partnership Innovation Fund. Read more: Govt awards $25m in grants from cybersecurity skills fund
Facebook fined €265 million
Ireland’s data protection agency fined Meta €265 million in connection to the company’s April 2021 data breach. The Irish Data Protection Commission said that Meta failed to safeguard its Facebook platform from data scraping, which allowed a threat actor to compile details on more than 530 million Facebook users. This data was later sold on an underground cybercrime forum. Responding to the fine, Facebook told TechCrunch that they have since rolled out protections to detect scraping operations. With this fine, the Irish data protection agency has fined all of Meta’s three main platforms after it also fined Instagram €405 million in September 2022 and fined WhatsApp €228 million in September 2021. Read more:
- Meta hit with ~$275M GDPR penalty for Facebook data-scraping breach
- Data Protection Commission announces decision in Instagram Inquiry
- Data Protection Commission announces decision in WhatsApp inquiry
EDF fine
French privacy watchdog CNIL has fined nuclear energy group EDF €600,000 for multiple security and privacy lapses. CNIL said that EDF failed to inform users of its web portal how their data was collected and handled, in a clear violation of the EU GDPR regulation. In addition, CNIL said that EDF had also failed to secure passwords for 2.5 million users, which were hashed using the insecure MD5 algorithm and were not salted, according to industry-accepted security best practices. Read more: Prospection commerciale et droits des personnes : sanction de 600 000 euros à l’encontre d’EDF
South Korean cyber sanctions
The Seoul government said last week that it was considering imposing sanctions on North Korean individuals linked to the regime’s cyber operations. The US Treasury Department has already sanctioned multiple North Korean individuals and threat actors it said are behind a cybercrime spree that has stolen funds from banks and cryptocurrency platforms. The US government said these funds were later laundered and diverted to North Korea’s nuclear missile program. South Korean officials said they are now considering applying the same type of sanctions against North Korean cyber units after their northern neighbor has intensified nuclear missile tests over the past months, despite political promises not to do so. Read more: South Korea to review unilateral cyber sanctions if North Korea tests nuke
AIVD threat actor assessment report
Dutch intelligence agency AIVD has published an assessment of current state-backed threat actors. The agency has identified China and Russia as the biggest threats, highlighting China’s penchant for using state groups for intellectual property theft and Russia’s use of cyber for sabotage and physical espionage operations. Other potential threats, but to a lesser degree to impact the Netherlands, were Iran and North Korea, with state-backed groups from both countries engaging in both cyber-espionage and cyber-crime at the same time. Read more: Dreigingsbeeld Statelijke Actoren 2
CYBERCOM hunt forward operations in Ukraine
US Cyber Command has published details for the first time on its “hunt forward” mission the agency conducted in Ukraine ahead and after Russia’s invasion. Officials said the mission consisted of a joint team of Navy and Marine Corps operators, who worked together with local Ukrainian teams to hunt and detect malicious cyber activity on Ukrainian networks. CYBERCOM said the mission lasted from December 2021 to March 2022, and its operators were present in Ukraine when Russia began executing destructive cyber-attacks in mid-January. CYBERCOM described its Ukrainian mission as the “largest hunt forward team” the agency has deployed in the field so far. Read more: Before the Invasion: Hunt Forward Operations in Ukraine
Scam group detained in Spain
The Spanish National Police has detained six suspects on Tuesday for their alleged role in a criminal gang that has defrauded and stolen more than €12 million from more than 300 victims across Europe. Spanish authorities said the group ran several websites posing as banks and cryptocurrency portals through which they tricked users into making fraudulent investments that sent money to the group’s bank accounts. The group then proceeded to launder the money through accounts at several Spanish banks before transferring the money overseas. At the same time, Europol also announced it took down more than 12,500 websites across Europe that were being used to sell counterfeit goods and digitally pirated content. Read more:
- La Policía Nacional desarticula una organización criminal que defraudó más de 12 millones de euros mediante phishing
- International operation shuts down websites offering counterfeit goods and pirated content
EmBEARassment Disclosures
A Telegram channel titled EmBEARassment Disclosures claims to have found links between Swiss software company NeoSoft AG and the Russian intelligence agency FSB. The channel claims NeoSoft is a front company for Russian individuals associated with the FSB to sell spyware and surveillance tools to autocratic regimes from a safe European country. Documents shared in the channel claim to show that NeoSoft’s “tactical software and hardware solutions” have been sold to governments in Egypt, Ecuador, Vietnam, India, Pakistan, and Kazakhstan, but also to EU countries such as Sweden.
ArvinClub evolution
Threat intelligence analyst Marco A. De Felice has published a report on ArvinClub and how the group has recently and suddenly changed from a ransomware and data extortion gang to a hacktivist group that now regularly targets Iranian governmental structures. Read more: The metamorphosis of Arvin Club, from a ransomware group to a group of activists against the Iranian Islamic regime
UK Crypto-fraud on the rise
According to a freedom of information request to UK police unit Action Fraud from the Financial Times, UK crypto fraud rose by a third in one year, police data show, with criminals stealing hundreds of millions of pounds from consumers. Read more: Crypto fraud jumps by a third in UK
KEV update
CISA has updated its KEV database with two vulnerabilities that are currently being actively exploited in the wild. The two are a Chrome zero-day (CVE-2022-4135) patched last week and an auth bypass in Oracle Access Manager from 2021 (CVE-2021-35587) that recently came under attack. Read more: CISA Adds Two Known Exploited Vulnerabilities to Catalog
Botnet creation app
Evina security researcher Maxime Ingrao has discovered a malicious Android app available on the Google Play Store that turns infected smartphones into virtual phone numbers that can be used to register accounts on various social media networks. Ingrao said the malicious app appears to be the backend of a website that allows users to buy bulk accounts on social media sites. The researcher said the app has been downloaded more than 100,000 times already and is currently ranked first in India for the SMS tools category. Read more: Malicious Android app found powering account creation service
CashRewindo
Ad security platform Confiant says that a malvertising group it is tracking as CashRewindo is using domains registered years before to bypass security protections on advertising platforms and run malicious ads. While the group could be buying old domains from domain-reputation-building markets, Confiant researchers believe the group is registering domains themselves and then sitting on the URLs for years before deploying them in their malvertising operation. Read more: CashRewindo: How to age domains for an investment scam like fine scotch
New DFIR Report analysis
We all love DFIR Report write-ups, and they just published another one—detailing how a phishing campaign delivering LNK shortcut files turned into an Emotet infection and then a domain-wide ransomware attack. Read more: Emotet Strikes Again – LNK File Leads to Domain Wide Ransomware
Laplace Clipper
OALABS has some tips and IOCs for those looking to improve their detection and threat-hunting of Laplace, a Go-based malware strain designed to steal data from OS clipboards currently sold on underground cybercrime forums.
Acer Secure Boot bypass
Hardware vendor Acer has patched a vulnerability (CVE-2022-4020) that could be abused to disable the Secure Boot option inside the company’s BIOS firmware.The vulnerability was discovered by Slovak cybersecurity firm ESET earlier this year and is a variation of the same bug also impacted Lenovo devices. Lenovo shipped patches at the start of November. If exploited, both vulnerabilities could allow a threat actor to tamper with an operating system’s loading process. Read more Security Vulnerability Regarding Vulnerability That May Allow Changes to Secure Boot Settings
Swatting incident
Bot Sentinel Founder Christopher Bouzy said that he was swatted over the weekend at his home in New Jersey. Police said they intervened after they received a call about a child screaming in Bouzy’s home. Nobody was hurt in the incident. Read more: Bot Sentinel founder says he was ‘swatted,’ North Bergen police probing possible ‘trolling’
Updated on 2022-11-28
Twitter users are definitely having a perplexing time over at the social media platform. Millions of personal user details were found on a dark web forum, and that too, for free. Ragnar Locker is back in the news by attacking a Belgian police force and stealing loads of highly sensitive information. In other news, another small U.S. college fell victim to the Vice Society ransomware group. Here’s everything that happened this weekend.
More highlights from the past 24 hours
- Scammers abused the official website of FC Barcelona in an advanced third-party fraud campaign. The suspicious link led to an online gambling portal. Read more: FC Barcelona’s Website Used by Scammers for Fraud
- African police arrested 10 individuals associated with $800,000 worth of global fraud, following a four-month-long operation. The police took action against 200,000 malicious cyber infrastructure elements. Read more: African Police Bust $800K Fraud Schemes
- Dragos reported that Russian hacker groups, Xenotime and Kamacite, are conducting “exploratory research” into Dutch LNG terminal systems. Read more: Russian Hackers Target Dutch LNG Terminal
- Harry Rosen, Canadian menswear retailer, confirmed that it suffered a cyberattack last month. The acknowledgment comes after the BianLian ransomware group listed the company on its leak site. Read more: Canadian menswear chain Harry Rosen confirms cyber attack
No WhatsApp breach
A threat actor has been circulating an alleged leak of WhatsApp data. It’s fake. It’s just a list of phone numbers, according to Alon Gal of Hudson Rock.
More Windows 11 protections
Microsoft will add a new detection and logging capability to Windows 11 that will allow security tools to detect when malware might attempt to bypass KASLR protections for the Windows kernel. The feature, a new ETW event, is undergoing testing in Windows 11 23H2 insider versions. Read more: An End to KASLR Bypasses?
Digital sovereignty
Speaking at a digital forum last week, Russia’s Minister of Digital Transformation said that after most foreign IT companies have left Russia following EU and US sanctions, Russia has now achieved “digital sovereignty” (I don’t think that’s how digital sovereignty works, but ok, whatever). In addition, the Russian official also said that even if a large number of IT specialists have left Russia, the number is not so large to “cause irreparable damage to the [IT] industry.” These are some very funny statements to make on the same day that rumors emerged that Russia’s largest IT company—Yandex—was looking to leave the country for greener pastures. Read more:
- Минцифры объявило о достижении цифрового суверенитета: иностранные IT-компании ушли
- ‘Russia’s Google’ wants to sell its Russian businesses and flee the country with its most promising tech
Defense Cyber Index
While the Belfer Center is known for its national offensive cyber index, MIT has joined the rank-your-country party with an index on which state has the best defensive capabilities. Topping the list for the year is Australia, the Netherlands, and South Korea. Read more: The Cyber Defense Index 2022/23
Darknet market takedown
Interpol said that authorities in Eritrea have taken down a darknet market that was selling hacking tools and cybercrime-as-a-service components. The takedown was part of a joint operation with AFRIPOL to crack down on African cybercrime gangs active inside African countries. This operation has also led to the arrest of ten suspects linked to online scams and fraud activities, the recovery of $150,000 from groups involved in data infringement and copyright cases, and takedowns of server infrastructure hosting malware, botnets, phishing sites, and online extortion operations. Read more: Operation across Africa identifies cyber-criminals and at-risk online infrastructure
Russian scammer gang detained
Russian authorities said they detained three suspects from the city of Kolpino, near Sankt Petersburg, for their alleged role in an international phone fraud network. Officials said the gang used more than 12,000 SIM cards to call victims as part of a scheme where they warned them about an impending theft from their bank account and tricked them into transferring funds into so-called “safe accounts”—that were under their control. The three suspects hosted IT infrastructure for the gang, which also consisted of members located outside Russia’s borders, according to the Russian Ministry of Internal Affairs. Read more: Полицейские Санкт-Петербурга задержали подозреваемых в организации технической поддержки международной сети телефонных мошенников
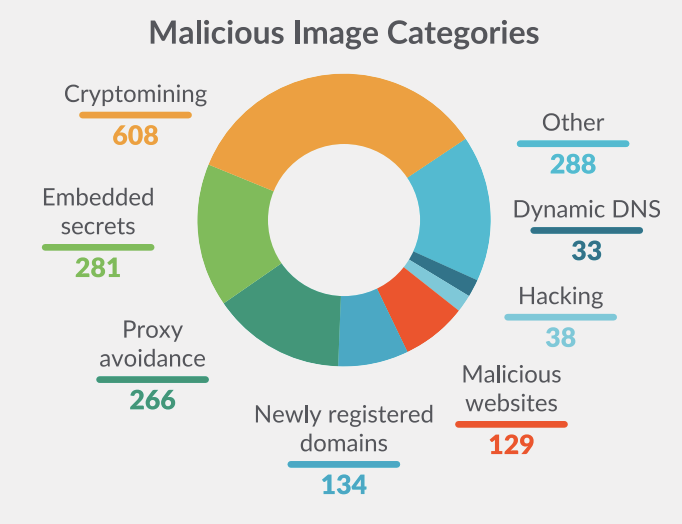
Malicious Docker Hub images
Cloud security firm Sysdig said it identified 1,652 malicious Docker images uploaded on the official Docker Hub portal. More than a third contained cryptomining code, while others contained hidden secret tokens that an attacker could later use as a backdoor into a server. Other Docker images contained proxy malware or dynamic DNS tools. Read more: Analysis on Docker Hub malicious images: Attacks through public container images
Potao source code
A threat actor is claiming to sell the source code of Potao, a malware strain historically linked to the Sandworm APT. Gonna chuck this into the “very likely scam” bin. Read more: Operation Potao Express: Analysis of a cyber‑espionage toolkit
Infostealer fingerprinting
Equinix security researcher William Thomas has a write-up on how you can discover infostealer infrastructure by using IoT search engines to fingerprint their control panels. Read more: Detecting and Fingerprinting Infostealer Malware-as-a-Service platforms
New npm malware
Check out GitHub’s security advisory portal for details.
Twitter amnesty watch
After super-genius Elon Musk announced plans to reinstate banned accounts on Twitter, threat researchers are now keeping an eye on how many of the old Russian political propaganda accounts will be coming back online. An archive of those can be found here. In the meantime, enjoy watching Twitter devolve into a right-wing cesspool with conspiracy theories constantly trending on the platform, driven by abhorrent bot networks. Oh, and death threats, personal attacks, and account reporting raids. Read more: ‘Opening the gates of hell’: Musk says he will revive banned accounts
Zanubis
Something we missed two months ago is this technical report on Zanubis, a new Android banking trojan. More on how to find samples from VT. Read more: Zanubis LATAM Banking Trojan
Koxic and Wiki
AhnSec researchers have reports on Koxic and Wiki, two new ransomware strains they’re seeing distributed in South Korea. Read more:
APT-C-09
Qihoo 360 researchers published a report on recent attacks carried out by the APT-C-09 (Patchwork) threat actor, where they used spear-phishing to infect their targets with the BADNEWS backdoor. Read more: APT-C-09(摩诃草)组织针对巴基斯坦最新攻击活动
CVE-2022-34721
CYFIRMA researchers said they believe that a threat actor is using an exploit for CVE-2022-34721 to target Windows systems that have yet to be patched. The vulnerability is a remote code execution in the Windows IKE protocol that Microsoft patched in September. CYFIRMA said the attacks are linked to a campaign named “流血你”—which translates from Chinese to “bleed you.” An exploit for this was shared on GitHub in September. Read more:
- Windows Internet Key Exchange (IKE) Remote Code Execution Vulnerability Analysis
- Windows Internet Key Exchange (IKE) Protocol Extensions Remote Code Execution Vulnerability: CVE-2022-34721
- 78ResearchLab/PoC
API security
Google Cloud said that half of the 500 companies it surveyed in a report released last week have experienced at least one API security incident over the past 12 months. Furthermore, the same survey identifies misconfigurations as the main threat to API infrastructure. Read more: 2022 API Security Research Report: Latest Insights and Key Trends
Updated on 2022-11-27
A leak details Apple’s secret dirt on security startup Corellium
Corellium, a cybersecurity startup that sells virtual iPhones and Android phones for app and pen-testing, offered or sold its tools to makers of government spyware and hacking tools, according to a leaked document prepared by Apple that contains internal Corellium communications. The document says Corellium offered iOS spyware maker NSO Group a trial, as well as offered to provide a quote to purchase its software to DarkMatter, a former cybersecurity company with close ties to the UAE. Corellium says it later denied NSO and DarkMatter requests to purchase the full version following its vetting process, which it explained more in a blog post after Wired’s story went up. But Corellium didn’t answer questions about why it allowed phone hacking companies Cellebrite or Elcomsoft to use its tech, or why Pwnzen was allowed to be a customer, despite helping to hack the phone of a suspected Chinese dissident back in 2019. Read more:
- A Leak Details Apple’s Secret Dirt on a Trusted Security Startup
- How We Vet Our Customers
- How the Biden administration wants to tackle foreign commercial spyware
Need a laptop repair? Don’t count on your privacy
A new study shows that laptop repairs often come hand in hand with privacy violations. When researchers recovered logs from 12 laptops that each went to a different repair shop, half came back with evidence that personal data from those laptops had been accessed. Unsurprisingly, female customers endure the most violations. Read more: Thinking about taking your computer to the repair shop? Be very afraid
Indictments stand for French spyware maker
An appeals court in France upheld the indictment of the French company Amesys for complicity in acts of torture in the sale of spyware to the former Gaddafi-run authoritarian regime in Lybia, more than a decade after it happened, reports RFI (en français]. FDIH, a human rights organization, said the news was a “source of hope” that the company would face justice. Read more:
- Libye: la mise en examen de la société française Amesys et l’inculpation de deux cadres, confirmées en appel
- Surveillance and torture in Libya – The Paris Court of Appeal confirms the indictment of AMESYS and its executives, and cancels that of two employees
- French spyware bosses indicted for their role in the torture of dissidents
Meta links pro-U.S. influence campaign to U.S. military
Facebook owner Meta dropped the goods on a U.S.-run influence operation across YouTube, Twitter, and Facebook aimed at making the U.S. and its allies look great in the eyes of CIS and Middle Eastern countries, while making Russia and China look terrible. But according to Meta, the fake posts created for the operation had “little to no genuine engagement.” To nobody’s surprise, @WaPoEllen had the scoop back in September, reporting that the Pentagon began auditing its clandestine information warfare operations after they were, well, caught out doing exactly what other nations were doing. Read more:
- Facebook Parent Meta Links Influence Campaign to US Military
- Pentagon reviews psychological operations amid Facebook, Twitter complaints
- Meta claims US military link to online propaganda campaign
Tax filing sites sent your data to Facebook
H&R Block, TaxAct, and TaxSlayer were all sending sensitive financial information to Facebook when U.S. residents filed their taxes online, according to new findings. It’s because Meta Pixels, the near-invisible website code that tracks website visitor activity, was transmitting back to the social giant things like names, email addresses, but also data on users’ income, filing status, refund amounts, and dependents’ college scholarship amounts, regardless if a tax filer had a Facebook account or not. Ars Technica reports that H&R Block and TaxSlayer removed the pixel. Read more:
- Major tax-filing websites secretly share income data with Meta
- Tax Filing Websites Have Been Sending Users’ Financial Information to Facebook
Updated on 2022-11-25
Guadeloupe cyberattack
In a message posted on its official website, the government of the Caribbean island Guadeloupe, a French overseas region, said it was hit by “a large-scale computer attack.” Officials said they shut down all affected systems to protect data and diagnose the problem. The incident took place on Monday, and systems have yet to be restored. Security experts believe this is a ransomware attack, although the perpetrators have not yet been identified.
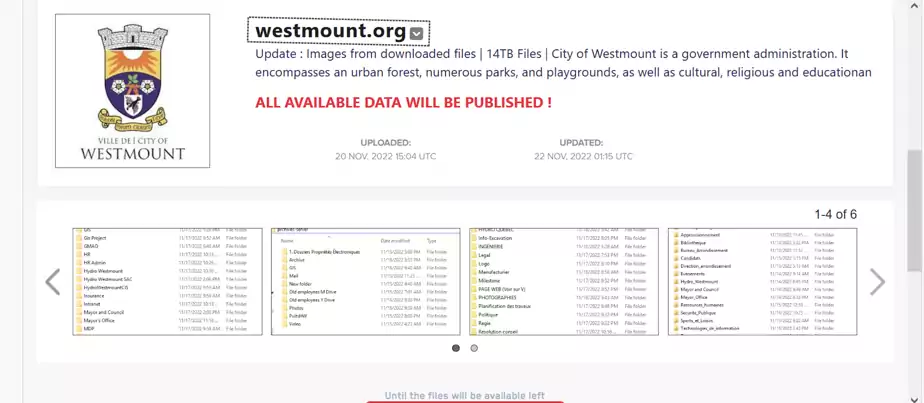
Westmount ransomware attack
The local government of Westmount, part of the Montreal urban area, said it’s dealing with a ransomware attack that crippled its IT network. Local press said the attackers have already demanded a ransom payment, but officials do not intend to pay. Read more: Les pirates affichent des dossiers sensibles qu’ils auraient volés
Don’t cyberattack here, plz
Retired US General Ben Hodges told Reuters that a cyber attack on the German ports of Bremerhaven or Hamburg would severely impede NATO efforts to send military reinforcements to its allies. That’s one way to say, “don’t cyberattack here.” I wonder how many threat actors have had their interests piqued by this article. Read more: Cyber as important as missile defences – ex-NATO general
Voting machine bug
Former Brazilian President Jair Bolsonaro filed a lawsuit claiming that more than 280,000 voting machines used in the recently-concluded presidential election contain a software bug. Bolsonaro’s camp said that the voting machines, all dating before 2020, lacked individual identification numbers in internal logs and asked a judge that votes from these systems be ignored. According to Bolsonaro’s lawyer, this would be enough to grant the former President the election victory. Read more: Bolsonaro contests Brazil election loss, wants votes voided
Cybersecurity Apprenticeship Sprint
The US government said that it hired 7,000 apprentices in official cybersecurity roles following an apprenticeship sprint held over the summer. Around 1,000 of the new hires came from the private sector. The sprint was launched in July by the White House and the Department of Labor as a way to boost the government’s cybersecurity workforce. Read more: US Gov Cybersecurity Apprenticeship Sprint: 190 New Programs, 7,000 People Hired
Operation HAECHI III
Interpol said it detained 975 suspects and seized nearly $130 million as part of a crackdown against cybercrime groups the agency calls Operation Haechi III. Officials said the suspects were involved in phishing, romance scams, sextortion, investment fraud, and money laundering criminal operations. Read more: Cyber-enabled financial crime: USD 130 million intercepted in global INTERPOL police operation
Hacking back
Security firm Bugdroid said it identified a vulnerability in the command and control (C&C) servers of the Mars Stealer malware. Bugdroid said the vulnerability can be used to tamper with Mars servers to delete data collected from infected users, terminate connections to infected systems, and even lock Mars operators out of their own servers by scrambling their admin passwords. The company told TechCrunch it neutralized five Mars Stealer servers so far and that the same vulnerability is also present in servers for the Erbium malware. Read more: Erbium Stealer Malware Report
Birdsite security issues
Some threat intel companies are telling their customers that they can no longer guarantee takedowns of malicious or reputation-damaging content from Twitter as there is nobody in Twitter’s abuse team to respond to requests anymore.
Hey, Google
Do your job!
Bahamut APT
Cyber-mercenary group Bahamut has been spotted using boobytrapped Android VPN apps to infect users with spyware. Spotted by ESET, the company said this campaign has been taking place since January, and the group has used a website posing as the SecureVPN service to distribute their spyware—made to look like the SoftVPN or OpenVPN applications. ESET said the campaign is still ongoing. Read more: Bahamut cybermercenary group targets Android users with fake VPN apps
CVE-2022-40300
ZDI has a report out on CVE-2022-40300, a Zoho ManageEngine SQLi vulnerability that could be used to hijack servers via its built-in password manager capability. Read more:
- CVE-2022-40300: SQL INJECTION IN MANAGEENGINE PRIVILEGED ACCESS MANAGEMENT
- Multiple SQL Injection Vulnerabilities in ManageEngine Password Manager Pro, PAM360 and Access Manager Plus
Argent vulnerability
Cryptocurrency platform Argent fixed a vulnerability last week that could have allowed a threat actor to empty customer wallets without any user interaction. Read more: Zero-Click Argent Contract Vulnerability, Explained
“The vulnerability is exploited by sending a transaction in a certain way that bypasses Argent Contract signature verification logic. This would allow an attacker to send any transaction with an empty or false signature that would get executed and accepted on-chain.”
ENISA investments report
The EU’s cybersecurity agency analyzed investments in the IT and cybersecurity field and found that information security budgets were “significantly lower compared to last year.” In a report on Wednesday, ENISA said the median percentage of IT budgets spent on information security in 2022 was 6.7%, 1% point lower compared to last year’s numbers. In addition, ENISA found that the estimated direct cost of a major security incident this year was around €200,000, twice as large as in 2021, indicating an increase in the cost of incidents. Read more: NIS Investments 2022 | NIS Investments 2022.pdf
Updated on 2022-11-24
Killnet has become a menace with its constant campaigns against significant government entities. It took down the website of the European Parliament, however, briefly. Misconfigured databases are bad, worse when they contain sensitive information on children. This is something that a now-defunct online interview system did. Meanwhile, researchers found another backdoored Chrome extension. Read along for the top 10 highlights from the past 24 hours.
More highlights from the past 24 hours
- A misconfigured database belonging to Tridas eWriter, containing 16,000 records, was found exposing the sensitive PII of thousands of children. Read more: Medical Software Firm exposes vulnerable children’s sensitive data
- Hospitality company Sonder recently revealed suffering a data breach, on November 14, that potentially affected guest records, including usernames, encrypted passwords, and contact details. Read more: Sonder Security Update
- The Ontario Secondary School Teachers’ Federation (OSSTF) revealed that it underwent a ransomware attack between May 25 and 30, which encrypted its systems. Read more: OSSTF victim of ransomware attack, notifies members of personal data compromised
- A ‘Transfer Money to safe account’ scam is currently underway in the Netherlands, warned Dutch Fraud reporting site FraudeHelpDesk. Read more:
Ransomware Dominates UK Government Crisis Meetings
Ransomware attacks comprise the majority of the British government’s crisis management or “Cobra” meetings, according to a report in The Record.
The Record’s article highlights the lack of ministerial interest in ransomware and points out that “the need to regularly hold cross-departmental meetings reveals how little progress Westminster has made to address the risks ransomware poses to the country”.
This is a stark contrast to the approach of Clare O’Neal, the Australian Minister for Cyber Security, who has led a strong Australian whole-of-government response after recent nationally significant breaches, including the announcement of a standing anti-ransomware disruption task force.
We’ll have to see if this approach works, but it is interesting to see a post on a Russian cybercrime forum concerned that the “Australian market” for ransomware has been killed. Read more: Ransomware incidents now make up majority of British government’s crisis management ‘Cobra’ meetings
Updated on 2022-11-23
The stealer-as-a-service business model has grown exponentially as researchers spotted multiple Russian hacking groups that stole over 50 million passwords in the first seven months of the year. LockBit 3.0 seems to be an unstoppable force as it claimed credit for an attack against a Canadian town. In other news, internal messages belonging to the Yanluowang group were released, leading researchers to an interesting discovery. To find that out, read through the top 10 highlights.
More highlights from the past 24 hours
- The Smith Family, an Australian children’s charity, suffered a cyberattack that exposed the personal information and credit card details of 80,000 donors. Read more: Children’s charity The Smith Family hit by cyberattack
- The Home Trust Mortgage company notified of a ransomware attack on its networks, impacting 1.5GB worth of personal information of clients. Read more: Home Trust Mortgage hit by Ransomware attack
- CERT-NZ recorded a whopping loss of $9 million due to online fraud, in just three months. Twelve victims lost $100,000 each to elaborate scams. Read more: Scammers siphon millions from Kiwi victims in elaborate cyber attacks
- BleepingComputer found that the Donut extortion group has resorted to deploying ransomware in double-extortion attacks against organizations. Read more: Donut extortion group also targets victims with ransomware
Updated on 2022-11-22
API mishandling can lead to bad circumstances. Users of a popular API solution, deployed by thousands of companies, are in trouble as their data could be at risk from hundreds of apps with insecure implementations. The Daixin Team is on a roll as they leaked some data belonging to a Malaysian airline. ‘Tis the holiday season and you’ll need gift cards but beware of one such scam that promises free gift cards but gifts you malware instead. Here are the top 10 highlights from the past 24 hours.
More highlights from the past 24 hours
- CloudSEK researchers found around 1,500 apps leaking the Algolia API key & Application ID, possibly exposing user data. Algolia API is used by 11,000 companies, including Slack and Medium. Read more: Thousands of Algolia API Keys Could Expose Users’ Data
- Tehama County, California, started notifying employees, service recipients, and affiliates of a data breach that potentially impacted their personal information, including SSNs. Read more: California County Says Personal Information Compromised in Data Breach
- A new Tesco gift card scam is targeting visitors by claiming that they can receive gift cards worth between $100 and $500 and leading them to malicious domains. Read more: Tesco Gift Card scam explained
- New research by Trellix revealed that phishing attempts against victims in the Middle East surged by 100% since last month, owing to the upcoming World Cup in Qatar. Read more: World Cup phishing emails spike in Middle Eastern countries
Italy tracks and redirects entire ISP traffic
Italian police said they tracked and redirected the internet traffic from all internet service providers in order to identify people who subscribed to a pirate IPTV service. Cool, but maybe they can use the same “capability” next time to detect Italian systems connecting to known malware C2—and be actually useful to their citizens. Read more: Police Tracked Traffic of All National ISPs to Catch Pirate IPTV Users
Rewards for Russian hacktivists
Dmitry Gusev, a deputy in the Russian Duma, has floated the idea of awarding Russian hacktivists state awards and military ranks as a way to thank them for attacks carried out across the world.
US State Department security audit
A security audit carried out in September 2022 found vulnerabilities in eight of nine domains managed by the US State Department “despite the Department’s expenditure of substantial resources on information system security.” [See OIG report/PDF] Read more: IG dings State Department’s information security program in annual report
CISA IRPF update
CISA has updated its Infrastructure Resilience Planning Framework (IRPF), released last year, with more information to better help state, local, tribal, and territorial (SLTT) planners protect infrastructure. Read or download the full IRPF v1.1 here/PDF. Read more: CISA UPDATES THE INFRASTRUCTURE RESILIENCE PLANNING FRAMEWORK
“[IRPF] can be used to support capital improvement plans, hazard mitigation plans, and other planning documents, as well as funding requests. Today’s update adds important new resources and tools to better support partners as they face an evolving threat environment.”
NSO’s Supreme Court case
In an update on the NSO-vs-Facebook lawsuit and NSO’s attempt to have the case heard at the US Supreme Court to overturn an initial ruling, the US Supreme Court has asked the US Department to weigh in. According to a document [PDF] filed this week, the DOJ told the Supreme Court that it sees no reason for NSO Group to receive state-level immunity for how their tools were used to hack into personal WhatsApp accounts and recommended the Supreme Court not to hear their case.
“Whether or not common-law immunity for an entity acting as the agent of a foreign state might be appropriate in some circumstances, NSO plainly is not entitled to immunity here. The State Department has not filed a suggestion of immunity in this case. There is no established practice—or even a single prior instance—of the State Department suggesting an immunity for a private entity acting as an agent of a foreign state. And no foreign state has supported NSO’s claim to immunity; indeed, NSO has not even identified the states for which it claims to have acted as an agent. Nor does the court of appeals’ decision otherwise warrant review. It does not conflict with any decision of this Court. The question presented has not divided the courts of appeals—indeed, it has seldom arisen at all. And this unusual case would be a poor vehicle for considering that question in any event. The petition for a writ of certiorari should be denied.”
Lurk leader has sentenced reduced
A Moscow court has reduced the prison sentence of Konstantin Kozlovsky, the leader of the Lurk cybercrime group, to 13 years and four months in prison. Kozlovsky had his sentence reduced by eight months from the initial 14 years in prison he received earlier this year. Read more:
- Хакерам пересчитали сроки
- The Curious Case of Konstantin Kozlovsky
- Russia Jails Hacking Ringleader for 14 Years
Russian cybercrime investigation
Russian law enforcement has seized two Bitcoin wallets from a law enforcement official who was investigating the Infraud cybercrime organization. According to court documents, the wallets held more than 1,000 bitcoin and are believed to have been bribes the investigator received from the gang’s lawyer. Read more: Thirty-six Defendants Indicted for Alleged Roles in Transnational Criminal Organization Responsible for More than $530 Million in Losses from Cybercrimes
REvil investigation stalls
Kommersant reports that the criminal case against members of the REvil gang detained by Russian officials earlier this year has stalled after US investigators broke communications and cooperation with their Russian counterparts following Russia’s invasion of Ukraine. Read more:
- Американские банковские карты не помогли российскому следствию
- FSB arrests REvil ransomware gang members
Freebie Bots
Kasada researchers said they identified a new type of automated bot attack named Freebie Bots that operates by scanning retail websites for mispriced goods and services and purchasing them at scale before the error is fixed. Read more: Kasada Details the Latest Threat to Retailers this Holiday Season – Freebie Bots
“Kasada research has found more than 250 retail companies recently being targeted by Freebie Bots, with over 7 million messages being sent monthly in freebie communities. Members within one popular freebie community used Freebie Bots to purchase nearly 100,000 products in a single month, at a combined retail value of $3.4 million. Kasada’s research reveals that the total cost of the goods for Freebie Bot users was only $882, helping some individuals to realize a monthly profit of over $100,000.”
OMG!OMG! Market
Threat intel outfit DarkOwl has a profile out on OMG!OMG! Market, a Russia-based dark web market that appears to have taken one of the top spots as the go-to destination after the Hydra seizure earlier this year. The market is primarily known for its drug-trading ecosystem. Read more: Darknet Marketplace Snapshot Series: OMG!OMG! Market
Karakrut starts recruiting
Karakurt, a group with ties to the former Conti gang [1, 2, 3] and known for its hack-and-leak extortion operations, announced this week they are recruiting people to breach networks, malware coders, social engineers, and personnel to extort companies for payments.
Nighthawk C2 framework
Proofpoint has an analysis on Nighthawk, an up-and-coming red-team tool from MDSec. Proofpoint said it hadn’t seen Nighthawk abused by threat actors, but it can see its appeal as a possible C&C framework for malware operations. Read more: Nighthawk: An Up-and-Coming Pentest Tool Likely to Gain Threat Actor Notice
RobinBot
QiAnXin researchers said they spotted a new IoT malware strain named RobinBot that has been used to carry out DDoS attacks. Researchers said the malware uses code borrowed from the Mirai and Gafgyt families, supports multiple DDoS attack methods, and can spread via both Telnet password brute-forcing and vulnerability exploitation. Read more: RobinBot——快速扩张中的新型 DDoS 僵尸网络
Tofsee
The Tofsee spam botnet is still alive, apparently, and doing very well [PDF]. Read more: Taking a look at Tofsee
AWS vulnerability
DataDog’s Nick Frichette has disclosed a vulnerability in the AWS AppSync service that could have been exploited to break tenant barriers and access other customers’ resources. Amazon has rolled out a fix this week and says that no customer has been affected by this issue. Read more:
CVE-2022-41924
Emily Trau has a detailed write-up on remote code execution and DNS rebinding vulnerabilities in the Tailscale Windows VPN client. According to Trau, a threat actor can exploit the vulnerabilities by luring users to a malicious website. Vendor updates are available. Read more:
- CVE-2022-41924 – RCE in Tailscale, DNS Rebinding, and You
- Action required: Upgrade Windows clients to v1.32.3
Black Friday deals
Aussie security researcher Mike Monnik has compiled a list with some of the upcoming cybersecurity-themed Black Friday and Cyber Monday deals. Read more: 0x90n/InfoSec-Black-Friday
CISA on Mastodon
After a fake account was spotted for CISA Director Jen Easterly on Mastodon, CISA now has an official account on the platform.
LABScon 2022 videos
Talks from the LABScon 2022 security conference, which took place back in September, are available on YouTube. RiskyBizNews was told more videos will be uploaded in the coming days/weeks, so keep an eye on the playlist.
IRISSCON 2022 videos
Talks from the IRISSCON 2022 security conference, which took place earlier this month, are available on YouTube.
5G network security breaches
According to a survey commissioned by Nokia among 5G network operators, at least a third of all 50 respondents said they experienced eight or more security breaches over the past year. More in the survey itself or in CybersecurityDive’s coverage. Read more:
AWS Nitro System
Amazon has published details about the security design of its AWS Nitro System [PDF], the underlying virtualization platform on which all modern EC2 instances run. Read more: The Security Design of the AWS Nitro System
Meta improves privacy on children’s accounts
Meta announced this week that it would apply default options with increased privacy settings for children under the age of 18/16 that register new accounts on its Facebook and Instagram platforms. In addition, the company said it was also developing new tools to stop the spread of self-generated intimate images online. Read more: Protecting Teens and Their Privacy on Facebook and Instagram
More Apple privacy drama
Security researchers Tommy Mysk and Talal Haj Bakry said they found that Apple’s analytics service creates an identifier named “dsId” (Directory Services Identifier) that is unique for each user and tied to their iCloud account. The duo warns that because of this, Apple can track and identify users as they navigate the web and link them to their real-world identities. As MacRumors points out, the issue here is that Apple states on its privacy and legal page that no information from a device for analytics purposes can be traced back to any specific user. Read more: Apple Device Analytics Contain Identifying iCloud User Data, Claim Security Researchers
Updated on 2022-11-21
Hundreds and thousands of Mastodon users were targeted as threat actors were found scraping off their personal details. Threat actors are back, in a new SEO poisoning attack that abuses a legitimate Google service. The weekend introduced the cyber world to three new ransomware families as well. Read along for the top 10 highlights.
More highlights from the past 24 hours
- An Elasticsearch server was found scraping the posts and public information on Mastodon users and exposing it to the public. So far, it has scrapped the details of 150,000 users. Read more: Leaky Server Exposing Scraped Data of 150,000 Mastodon Users
- In a new SEO poisoning attack, threat actors are exploiting Google’s Looker Studio to lend credibility to their malicious websites promoting torrents, pirated content, and spam. Read more: Google Search results poisoned with torrent sites via Data Studio
- Cyble identified three new ransomware families – Alice Ransomware, Octocrypt, and AXLocker. The first two are RaaS families and AXLocker steals Discord tokens. Read more: AXLocker, Octocrypt, And Alice: Leading A New Wave Of Ransomware Campaigns
- The Central Depository Services Limited (CDSL), India, suffered a cyberattack on its servers, halting thousands of transactions associated with Demat accounts. Read more: CDSL services down due to cyber attacks
- A report by BlueVoyant revealed that 19% of private equity firms fail to implement proper cyber risk management in their portfolio companies. Also, the U.S. accounted for the highest number of firms impacted, followed by the U.K. Read more: Private Equity Exposed by Cyber-Hygiene Shortcomings
Certificate authorities are important. They vouch for the legitimacy of websites that you visit online with HTTPS certificates and are trusted by the big browsers. But Carroll found e-Tugra, a Turkey-based certificate authority, had exposed internal administrative tools and systems to the internet with their default credentials published on the exposed pages themselves. Carroll received no response from the authority after privately disclosing the issue. Read more: Security concerns with the e-Tugra certificate authority
New NSA center opens up to outside researchers
“No guns, no guards, no gates.” That’s the NSA’s new cybersecurity collaboration center, a largely unclassified but new space to make it easier for the agency to work with private sector security researchers. The so-called CCC now works with over 250 partner organizations to collaborate against foreign cyber threats. It seems to be working, with researchers taking notice. “It’s not a one-sided conversation. It’s not the usual government bullshit of, ‘Give us everything and go away, please,’” @juanandres_gs. Read more: ‘No guns, no guards, no gates.’ NSA opens up to outsiders in fight for cybersecurity
Amazon poaches top U.K. cybersecurity official
Ian Levy, the former technical director at the U.K. National Cyber Security Centre, will join Amazon in an unspecified role. The move was reportedly vetted by the so-called U.K. Advisory Committee on Business Appointments (ACOBA), which “scrutinises applications about new jobs for former ministers and senior civil and crown servants.” There’s going to the private sector after more than two decades in government, and there’s going to the dark side. Then, there’s Amazon. Read more: Amazon poaches top National Cyber Security Centre exec Levy
Google settles location tracking suit
Search and ads giant Google has agreed to pay a record $392M settlement with 40 states over allegations it tracked people’s devices even after they had turned location tracking off. It follows reporting by the Associated Press in 2018, which first found Google tracked users even when logged out of their apps. If you were wondering how little the settlement will affect Google, @1Br0wn calculated that it’s about 0.15% of Google’s $257 billion in revenue last year. Read more:
- AP Exclusive: Google tracks your movements, like it or not
- Google Agrees to $392 Million Privacy Settlement With 40 States
ID.me, but in four hours or more
Identity provider ID.me “inaccurately overstated” its ability to conduct verification services to the IRS when it was contracted to take over for the federal agency last year. ID.me said it took only about two hours to authenticate taxpayers using its verification service. Turns out that was “misleading” (and the rest…) and it was only discovered when everything for the company started melting down. The IRS later suspended the service, though ID.me is still used by some agencies. Read more:
- ID.me CEO backtracks on claims company doesn’t use powerful facial recognition tech
- Documents shed light on ID.me’s messaging to states about powerful facial recognition tech
- ID.me misled IRS on processing times for identity verification, congressional investigators found
AGs ask FTC for online privacy regulation
A coalition of 33 state attorneys general have urged the US Federal Trade Commission to pass regulation around online data collection practices. AGs said they are “concerned about the alarming amount of sensitive consumer data that is amassed, manipulated, and monetized,” and that they regularly receive inquiries from consumers about how their data is being hoarded and abused. [Read the full letter here/PDF] Read more: AG BALDERAS JOINS BIPARTISAN COALITION URGING THE FTC TO ACCOUNT FOR CONSUMER RISKS OF ONLINE SURVEILLANCE
Iran info-op in Latin America
Threat intelligence company Recorded Future has published a report detailing a years-long influence operation carried out by the Iranian and Venezuelan governments that targeted audiences in Latin America. The campaign revolves around the Colombian businessman Alex Saab, detained and extradited by the US from Cape Verde in 2020 for helping the Venezuelan government establish business ties with Iran and avoid US sanctions. Recorded Future claims that since Saab’s arrest, news outlets associated with the Iranian and Venezuelan governments, together with social media “influencer” accounts, have promoted the idea across Latin America that Saab, who was appointed as a special envoy for the Venezuelan government, was kidnapped by the US in contradiction to diplomatic immunity and international norms. Read more: Iran and Venezuela: The Alex Saab Trans-regional Influence Campaign to Increase Anti-US Sentiment in Latin America
Russian bill to seize cybercrime profits
Two Russian government officials have submitted a bill to the Russian State Duma with an amendment to the Russian criminal code that would allow the Russian government to easily seize funds obtained through cybercrime offenses, Kommersant reported. According to the bill’s text, the government plans to use the seized funds to compensate victims. Read more: В Госдуму внесен законопроект о конфискации имущества киберпреступников
Hackers detained in South Korea
South Korean police have arrested ten suspects who allegedly orchestrated a very targeted phishing campaign against the owners of popular Naver blogs. Police said the gang targeted only 500 of the most popular Naver blogs, managed to hack into 18, and made 200 million won ($149,000) from reselling the accounts to third parties. Officials said they are still hunting for other suspects who they believe helped the hackers. Read more: 네이버 인기 블로그 탈취해 되팔이…2억 챙긴 그놈들 수법
DDoS attacks on DNS servers
A CAIDA research paper has found that DDoS attacks targeted “millions of domains (up to 5% of the DNS namespace)” but that “most attacks did not substantially harm DNS performance,” even if some attacks did end up bringing down services or increasing resolution times of up to 100 times. The research paper analyzed data from a 17-month period between November 2020 and March 2022. Read more: Investigating the impact of DDoS attacks on DNS infrastructure
Malware on Telegram
Russian security firm Positive Technologies published a report on Telegram’s budding cybercrime ecosystem. According to the company’s scans, Telegram has slowly replaced hacking forums and is currently being used for advertising a wide spectrum of hacking services and malware, with the sale of remote access trojans, corporate network accounts, and cash-out services being some of the most popular topics on the platform. Read more: Cybercriminal market in Telegram
New npm malware
Check out GitHub’s security advisory portal for details. Read more: GitHub Advisory Database
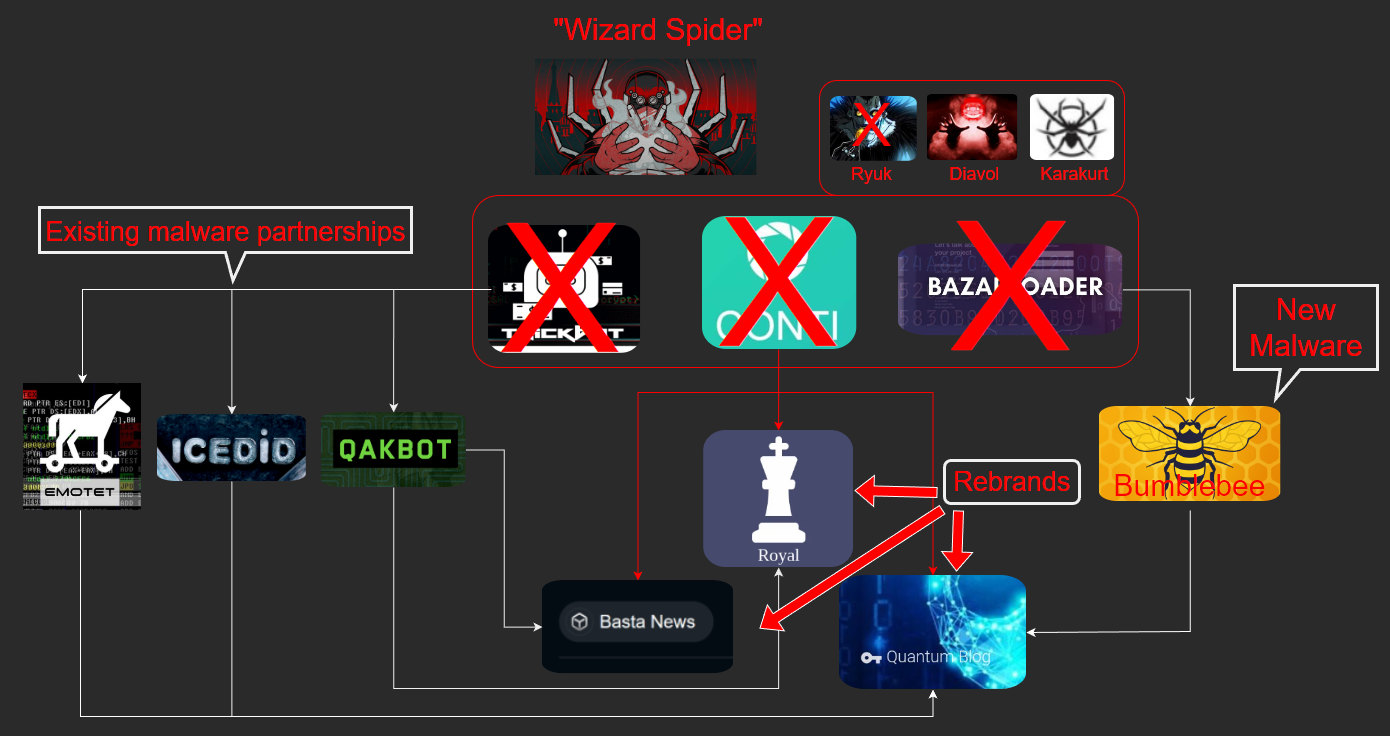
Conti off-shoots
Equinix security researcher William Thomas has a report on how members of the former Conti gang have scattered across the malware ecosystem since disbanding in early 2022. Read more: The Continuity of Conti
“The members of Conti have continued attacks, but seemingly under several different names, including Quantum, Royal, and Black Basta (also highlighted by Vitali Kremez here). Campaigns previously attributed to Conti such as Karakurt and Diavol have also continued in 2022 since the leaks. These new data-theft-extortion ransomware campaigns, though, have been supported by malware other than Trickbot and BazarLoader, this includes the new BumbleBee malware, as well as three malware botnets previously associated with Conti attacks: IcedID, Qakbot, and Emotet.”
GRU 26165
The Atlantic Council has a report on GRU Unit 26165, a cyber unit of the Russian military intelligence service that has used on-site agents to hack into their targets’ networks. The unit has been linked to an attempted hack of the Organization for the Prohibition of Chemical Weapons (OPCW), based in Amsterdam, the Netherlands. Read more:
“After loading a car with technical equipment—including a wireless network panel antenna to intercept traffic—the four individuals scouted the OPCW’s headquarters in The Hague for days, taking photos and circling the building before being intercepted by the Dutch General Intelligence and Security Service (Algemene Inlichtingen- en Veiligheidsdienst or AIVD) and sent back to Moscow. Seemingly, the plan had been for the operatives to hack into the OPCW’s systems to disrupt investigations into the attempted GRU chemical weapon attack [on former Russian intelligence officer Sergei Skripal and his daughter Yulia in Salisbury, England].”
Infineon vulnerability
German chipmaker Infineon is apparently using an eight-year-old version of OpenSSL for the trusted-platform module (TPM) for some of its chips, according to a report from Binarly, a security firm specialized in firmware security. Other companies like Lenovo, Dell, and HP were also found to use extremely old versions of OpenSSL as well, with Lenovo and Dell using an OpenSSL version released back in 2009. Read more: OpenSSL Usage In UEFI Firmware Exposes Weakness In SBOMs
CVE-2022-35803
NorthSec researchers have published details on CVE-2022-35803, a vulnerability in the Windows Common Log File System (CLFS) logging service that Microsoft patched earlier this year in September. Read more:
- Windows Kernel: Exploit CVE-2022-35803 in Common Log File System
- Windows Common Log File System Driver Elevation of Privilege Vulnerability: CVE-2022-35803
CVE-2022-26696
SecuRing researcher Wojciech Reguła has published details on CVE-2022-26696, a vulnerability in the macOS Terminal that can be exploited to escape the macOS sandbox. The bug was fixed in mid-September 2022. Read more:
Acquisition news
Palo Alto Networks announced plans to buy Cider Security, a company that develops application security (AppSec) and software supply chain security solutions. Read more: Palo Alto Networks Signs Definitive Agreement to Acquire Cider Security
OpenSSF adopts S2C2F
The Open Source Security Foundation (OpenSSF) has adopted the Secure Supply Chain Consumption Framework (S2C2F), a policy framework developed by Microsoft for hardening projects against supply chain attacks. Read more:
- OpenSSF Expands Supply Chain Integrity Efforts with S2C2F
- Microsoft contributes S2C2F to OpenSSF to improve supply chain security
Project Spaceman
An article from Richard J. Aldrich goes into Project Spaceman, a project by British computer maker ICL that provided secure systems to the MI5 and the British government in the early 80s. Read more: Project Spaceman: early British computer security and automatic data processing
New tool—MI-X
Cybersecurity firm Rezilion has open-sourced a tool named MI-X (Am I Exploitable?) that allows researchers and developers to know if their containers and hosts are impacted by specific, high-profile vulnerabilities. Read more: Rezilion Releases MI-X, A New Open Source Vulnerability Validation Tool
ResponderCon 2022 videos
Talks from the ResponderCon 2022 security conference, which took place in September, are available on YouTube. Read more: ResponderCon 2022 – Investigating Ransomware
Updated on 2022-11-18
Reflecting on the recent past, federal agencies had released a warning about increased Hive ransomware activities. In a new such alert, the CISA revealed that the ransomware group collected ransom payments from over a thousand companies. Mustang Panda is back in the headlines as it has been targeting multiple sectors across the world. In another update on ransomware threats, researchers revealed that the transportation industry was badly affected by them in the past quarter. Read along to know more.
More highlights from the past 24 hours
- New report by Trellix revealed that ransomware attacks surged 100% quarter-over-quarter in the U.S. transportation and shipping sector, in Q3 2022. Read more: Transportation sector targeted by both ransomware and APTs
- Akamai found an advanced phishing kit targeting North Americans since mid-September. The kit features a token-based system, ensuring that every victim is led to a unique phishing URL. Read more: Highly Sophisticated Phishing Scams Are Abusing Holiday Sentiment
- Kaspersky detected 438,035 malicious installation packages, in Q3 2022, of which 35,060 packages were associated with mobile banking trojans and 2,310 were mobile ransomware trojans. Read more: IT threat evolution in Q3 2022. Mobile statistics
- The Australian government’s cybersecurity minister announced plans to launch the Joint Standing Operation task force, merging domestic police and foreign intelligence resources, to disrupt international cybercrime. Read more: Australia Unveils Plan to Counter Global Cybercrime Problem
Hyundai fined
South Korea’s data privacy watchdog has fined automaker Hyundai 3 million won ($2,000) after the company’s engineers shipped untested code to one of its servers that exposed the personal data of six customers. According to the commission’s inquiry, the server in question was responsible for an app that broadcasts real-time sales information.
Dom.ru leak
Hackers have leaked the alleged database of Dom.ru, a Sankt Petersburgh-based internet service provider. The data allegedly contains the personal details of 4 million of the company’s customers, including full names, dates of birth, phone numbers, customer comments, and service-related information. Read more: В открытый доступ выложили личные данные 4 миллионов клиентов «Дом.ру» из Петербурга. Обновлено
Google and Microsoft services in French edu sector
As spotted by privacy expert Alexander Hanff this week, the French government has apparently told and warned educational institutions that the use of cloud products like Microsoft 365 and Google Workspace is technically forbidden across France because of their illegal data harvesting practices, which are not compliant with the GDPR. They’re still used in some schools, though.
Ad-blocker apocalypse getting closer
After AdGuard published a limited version of its ad-blocker to comply with Chrome’s new Manifest V3 extension design rules, AdBlock Plus did so as well this week, and it also complained about their ad-blockers extremely limited blocking capabilities. Crazy world we live in, where ad companies can neuter all ad-blockers in their browser without a formal government inquiry into its monopolistic behavior. Weird, eh? Read more:
- AdGuard publishes the world’s first ad blocker built on Manifest V3
- How Adblock Plus is Getting Ready for Manifest V3
CNIL fines Discord
France’s CNIL data protection agency has fined Discord €800,000 for multiple GDPR infractions. These included keeping data more than necessary and having a password management policy that was not sufficiently strong, such as allowing six-characters-long passwords. CNIL said the company has since corrected its password policy, which now also includes basic brute-force detection on failed login attempts. Read more: DISCORD INC. fined 800 000 euros
Russia’s cyber forces underperformed
Speaking at the Aspen Cyber Summit, Mieke Eoyang, deputy assistant secretary of defense for cyber policy at the Department of Defense, said that Russian forces “underperformed expectations” in both the cyber and military space. Read more: Russia’s cyber forces ‘underperformed expectations’ in Ukraine: senior US official
“Eoyang said some of that underperformance from the Russians could be tied to their underestimation of how long it takes to prepare for cyber operations and cyberattacks prior to a war.”
Universal health code in China
The Chinese government is planning to digitize the health records of its citizens and assign them a “universal health code” by 2025. The move has sparked fear among Chinese activists that the digitized health records could be used to bar citizens’ access to certain services, jobs, or benefits based on their medical history, genetic information, or family history. Read more: Planned ‘universal health code’ linked to health data platform sparks fears in China
US-China cyber report
In its yearly report to Congress, the US-China Economic and Security Review Commission has found that “China has developed formidable offensive cyber capabilities over the past decade and is now a world leader in vulnerability exploitation.” The commission also found that China “enjoys an asymmetric advantage” over the US in cyberspace due to its unwillingness to follow norms for responsible state behavior. The report found that China selectively applies and promotes norms to benefit its authoritarian view of cyberspace and is “creating new organizations to supplant existing cyber governance mechanisms in line with its vision for the internet.” Read more: 2022 Annual Report to Congress
Chinese hacker
Chinese authorities have sentenced a hacker named Li Moumou to 10 years and six months in prison for stealing 384 Ether coins, worth $110,000 at the time of the theft in early 2018, from the wallet of a local man. Authorities said Moumou obtained the funds using a trojan planted on the victim’s device and that after his arrest, they managed to return the stolen funds to the victim. Read more: 男子转走384个以太币 获刑十年零六个月
Two scammers sentenced
George Ugochukwu Egwumba, 47, and Princewell Arinze Duru, 33, both from California, were sentenced this week to 132 and 81 months in federal prison for their involvement in BEC, romance, and elder fraud scam operations. According to the DOJ, the men worked as middlemen with a Nigerian cybercrime gang, helping the group launder stolen funds. Read more: Orange County Man and Sacramento Man Sentenced to Prison for Participating in Massive Fraud and Money Laundering Conspiracy
“The conspiracy involved the laundering of at least $6 million in fraudulently obtained funds and the attempted theft of at least an additional $40 million.”
Elastic’s threat landscape report
Elastic’s security team its 2022 Global Threat Report. Some of the company’s main findings are below:
- CobaltStrike was the most popular malicious binary or payload for Windows endpoints, with ~35% of all detections.
- On macOS, almost 48% of detections were linked to the MacKeeper binary, considered by many security firms as adware.
- On Linux, Meterpreter was the most common malicious payload, with almost 14% of all detections, followed closely by Gafgyt (12%) and Mirai (10%).
Record number of DDoS attacks
Security firm NCC Group said that the month of October saw the highest number of DDoS attacks this year, with a 14% increase from September, to 2,090 recorded attacks. Per Matt Hull, Global Head of Threat Intelligence at NCC Group, “this shift is even more notable this month as overall ransomware attacks decreased.” Read more: NCC Group Monthly Threat Pulse – October 2022
Malware on npm
Malware has been found in three npm libraries named geocomponents, babel-preset-geocaching, and geocaching-express-account-middleware.
WatchDog
Cado Security has a report out on the WatchDog crypto-ming botnet, which has seen a resurgence over the summer. Previous reports on this botnet are also available via Trend Micro, Lacework, and AquaSec. In a 2021 report, Palo Alto Networks called WatchDog one of the oldest crypto-mining gangs in operation today. Read more:
- WatchDog Continues to Target East Asian CSPs
- TeamTNT Returns — Or Does It?
- How Watchdog smuggles malware into your network as uninteresting photos
- Threat Alert: New Malware in the Cloud By TeamTNT
- WatchDog: Exposing a Cryptojacking Campaign That’s Operated for Two Years
Typhon Reborn
PAN’s Unit42 has analyzed Typhon Reborn, a newer version of the Typhon Stealer, currently advertised in underground Telegram channels. Read more: Typhon Reborn With New Capabilities
“These new features include block listed usernames and countries, new message clients and a crypto-extension stealer for Google Chrome and Microsoft Edge. The author also removed a few existing features, including the keylogging ability as well as the clipboard stealing and crypto mining features.”
HZ Rat
German cybersecurity company DCSO has a report out on HZ RAT, a lesser-known trojan that hosts many of its command and control servers in China. Read more: HZ RAT goes China
Dagon Locker ransomware
A new ransomware strain named Dagon Locker has been spotted being distributed in the wild. According to AhnLab and Symantec researchers, Dagon features strong code similarities to the MountLocker and Quantum ransomware strains. Currently, the Dagon crew does not run a leak site to shame victims, nor does it delete volume shadow copies, which may allow some of the encrypted data to be recovered. Read more:
Zendesk vulnerabilities
Varonis researchers have published details on an SQL injection vulnerability in Zendesk Explore, an analytics and reporting service for the Zendesk CRM platform. Read more: Varonis Threat Labs Discovers SQLi and Access Flaws in Zendesk
“Zendesk started working on a fix the same day it was reported. The company fixed multiple bugs in less than one workweek with zero customer action required.”
New tool—Orpheus
TrustedSec has open-sourced a new tool named Orpheus that can bypass current Kerberoasting protections. Read more: The Art of Bypassing Kerberoast Detections with Orpheus
Jamf acquires ZecOps
Cybersecurity firm Jamf has acquired ZecOps, a small security shop specializing in iOS security. Read more: ZecOps acquisition expands Jamf’s mobile security capabilities
2022 Aspen Cyber Summit stream
A recorded live stream of the 2022 Aspen Cyber Summit, which took place this week, is available on YouTube and embedded below. A text summary of the hours-long event is available via The Record, as well. Read more: Aspen Cyber Summit 2022 — Live Coverage
Updated on 2022-11-17
These data breaches have honestly gone out of hand! Hundreds of thousands of inmates in a Kentucky health facility had their PHI exposed. Times are tough as federal agencies warned against Iranian threat groups abusing the Log4Shell flaw. In another bone-chilling news for the cyber community, Emotet is back with an upgraded arsenal. Read along for the top 10 highlights from cyberspace.
More highlights from the past 24 hours
- A server misconfiguration at Kentucky-based CorrectCare Integrated Health leaked the sensitive details of 600,000 inmates who had received medical attention during the past decade. Read more: Misconfigured Server Exposed PHI of 600,000 Inmates
- New report by Comparitech revealed that, since 2018, 500 publicly-disclosed ransomware attacks cost the healthcare industry $92 billion in downtime, impacting 49 million patient records. Read more: Since 2018, ransomware attacks on healthcare organizations have cost the world economy $92bn in downtime alone
- Europol’s EC3, along with law enforcement agencies from 19 countries, conducted a month-long operation and arrested 59 scammers as part of an international crackdown against credit card fraud. Read more: Police just launched an e-commerce fraud crackdown. Here’s how to protect yourself from scammers
- A report by the U.S. DOD states that hackers are increasingly targeting the agency itself and the U.S. defense industrial base. It found that a majority of cyber incident reports are incomplete. Read more: Majority of DOD cyber incident reports are incomplete, GAO finds
- SaaS-based secrets management platform Akeyless raised $65 million in Series B funding, led by NGP Capital and existing investors as participants. Read more: Akeyless secures a cash infusion to help companies manage their passwords, certificates and keys
- AppSec startup ArmorCode raised $14 million in Series A round led by Ballistic Ventures, with Sierra Ventures and Cervin Ventures as participants. Read more: AppSec Startup ArmorCode Raises $14 Million
Updated on 2022-11-15
The much-reported menace of cloud data leaks continues to haunt organizations. Now, researchers found PII in exposed Amazon RDS snapshots. Over 800 of those btw! A new dangerous malware loader has been spotted that infected a lot of systems in a very short period. No sector seems to be safe from it. The Killnet group, once again, claimed responsibility for a DDoS attack against the FBI. Read along to know what transpired in the past 24 hours.
More highlights from the past 24 hours
- A ransomware attack forced Jackson County Intermediate School District officials to take offline their networks. The system outage impacted phones, classroom tech, and heating. Read more: Ransomware attack responsible for shutdown affecting Jackson, Hillsdale schools
- The FBI director warned against Chinese exploitation of TikTok for controlling data collection of millions of users or controlling the recommendation algorithm. Read more: FBI Director warns of potential Chinese gov’t exploitation of TikTok
- The FBI issued a PSA warning against tech support scams, in which scammers impersonate support staff from software firms and trick users into giving up their bank account details. Read more: Scammers Using Computer-Technical Support Impersonation Scams to Target Victims and Conduct Wire Transfers
- Attack surface management firm Bishop Fox raised $46 million in Series B funding led by WestCap, with participation from NextEquity Partners and Rockpool Capital. Read more: Bishop Fox Adds $46 Million to Series B Funding Round
- Zero trust cybersecurity solution provider ThreatLocker announced the acquisition of Third Wall, a risk management platform for DeFi protocols, for an undisclosed sum. Read more: ThreatLocker acquires Third Wall to provide endpoint protection for MSPs
Updated on 2022-11-15
As phishing campaigns continue surging at an alarming rate, it is imperative that netizens stay cautious. A large-scale sophisticated phishing campaign was observed exploiting reputed brands across several industry verticals. In other news, a massive data breach hit a Russian mobility service, which impacted millions of customers. The holiday season is approaching and so are online scams, warned NCSC. Here are the top 10 highlights from the past 24 hours.
More highlights from the past 24 hours
- The NCSC-U.K cited that online shoppers lost around $18 million between November 2021 and January 2022 to scammers. Around 45% of victims were in the 19–25 age group. Read more: UK Shoppers Lost £15m+ to Scammers Last Winter
- Cyble spotted threat actors in a phishing campaign targeting Bank Rayat Indonesia. They automatically fetch OTP from a compromised device using the SMS Stealer Android malware. Read more: Phishing Campaign Targeting Indonesian BRI Bank Using SMS Stealer
- VirusTotal reported 1,700 URLs and 400 government-related domains in over 50 territories propagating malware, including ransomware, trojan, coin miners, and others. Read more: Deception at scale: How attackers abuse governmental infrastructure
ESET’s APT report
Slovak cybersecurity firm and antivirus maker ESET published a report on the APT activity over the second trimester of 2022 (months May to August). The company’s report includes detailed activity for the primary groups originating from Russia, China, Iran, and North Korea, the primary sources of maligned state-sponsored activity in T2 2022. Read more: ESET APT Activity Report T2 2022
XDSpy
Chinese security firm Anheng Hunting Labs has published a report on new attacks carried out by the XDSpy APT against Russian organizations, including the Ministry of Defense. The XDSpy APT was first discovered in 2020 by CERT-Belarus and ESET and hasn’t been linked to any particular government yet, even if it has been active since at least 2011. Read more: XDSpy APT组织近期针对俄罗斯国防部的攻击活动分析
Mastodon gets its tires kicked
PortSwigger team has kicked the tires on Mastodon’s security features, and they found a way to steal account passwords from Mastodon users by leveraging an HTML injection vulnerability without needing to bypass CSP. Read more: Stealing passwords from infosec Mastodon – without bypassing CSP
Wi-Peep attack
Academics from Canada and the US have published details on Wi-Peep, a new attack that exploits loopholes in the WiFi 802.11 protocol to localize a target’s WiFi devices inside a predefined space, like a building or room. The paper is here [PDF], while Mathy Vanhoef, another security researcher known for his work on WiFi security, has an explanation of the attack on Mastodon [embedded below].
“Attacker spoofs beacons to pretend there’s buffered traffic. Clients request this traffic & reveal their MAC address. Fake frames are sent to the victim & time-of-flight of the response is used for localization. This can be done from cheap drones. They used an ultra-light DJI mini 2 drone with two lightweight WiFi chips: an ESP8266 & ESP32. Idea is that you can now “look inside a room” and learn where devices are located. For instance, you can learn the location of WiFi security cameras.”
PCspoof vulnerability
Researchers from the University of Michigan and NASA have published details about PCspoof, a vulnerability impacting Time-Triggered Ethernet (TTE), a networking protocol that uses time scheduling to synchronize and deliver network packets across Ethernet. TTE is widely used in spacecraft and aircraft technologies because the packet synchronization feature allows multiple systems to co-exist safely on the same hardware inside mission-critical devices. According to the research team, the PCspooF attack breaks this isolation and synchronization between different systems and allows network traffic from one system to interact with other systems on the same device. Technical details are available in this research paper [PDF]. Read more: Cyber vulnerability in networks used by spacecraft, aircraft and energy generation systems
Crypto hacks and rugpulls
Cryptocurrency platform DeFiAI said it was hacked and lost $4 million worth of customer tokens. In the meantime, the maintainers of the Flare token appear to have disappeared with their investors’ money in a type of scam known as a “rugpull” in the cryptocurrency community. Flare investors are believed to have lost more than $18 million.
Google fine
In the largest multi-state data privacy settlement in US history, Google has agreed to pay $391.5 million, representing a fine for lying and misleading users into thinking they had disabled location tracking in their account settings sections. Attorney General Offices across 40 US states sued Google in 2018 following an AP article that found that Google was tracking its users even when they enabled a Google account privacy setting that claimed to turn off location tracking. Google’s statement on the lawsuit settlement is here. Read more:
- 40 Attorneys General Announce Historic Google Settlement over Location Tracking Practices
- AP Exclusive: Google tracks your movements, like it or not
- Managing your location data
Red Hat deploys cryptographic signatures
Something we missed last month was that enterprise software giant Red Hat added cryptographic signatures for its ZIP file packages, a move that will protect its supply chain and ensure customers can tell if a library came from Red Hat’s servers. This feature has been live since October 4, and a technical breakdown of how it works is available here: Cryptographic signatures for zip distributions
Firefox 107
…is out, along with security updates. Read more:
Two GAO reports
The US Government Accountability Office has released two reports this week. In the first, GAO chided the Defense Department for not fully implementing processes for managing cybersecurity incidents, not having complete data on cyber incidents, and not notifying individuals affected by incidents. In the second, GAO praised the Secret Service for making headway in implementing a zero trust architecture. Read more:
- DOD Cybersecurity: Enhanced Attention Needed to Ensure Cyber Incidents Are Appropriately Reported and Shared
- Cybersecurity: Secret Service Has Made Progress Toward Zero Trust Architecture, but Work Remains
UAE
Amid a report from the Washington Post that the United Arab Emirates tried to manipulate the American political system through intensive lobbying, BreakingDefense also has a report out on the country’s recent efforts to establish itself as a cybersecurity and secure comms hub. Read more:
- U.S. intelligence report says key gulf ally meddled in American politics
- With shows, acquisitions and partners, UAE hopes to emerge as cybersecurity, secure comms hub
EU EDPS LOL
The European Data Protection Supervisor wants the EU to ban “highly advanced military-grade spyware.” Ok, skippy! Good luck with that. Read more: EU Media Freedom Act: EDPS calls for better protection for all journalists and a ban on highly advanced military-grade spyware
Italy bans facial recognition
The Italian data protection agency has banned the use of smart glasses and facial recognition software until the end of 2023 or until a specific law is adopted by the central government. The agency, which recently ruled in a case against two municipalities, said the only permitted use of facial recognition would be for law enforcement and judicial investigations. Read more: Videosorveglianza: stop del Garante privacy a riconoscimento facciale e occhiali smart. L’Autorità apre istruttorie nei confronti di due Comuni
Zeus Tank detained
Vyacheslav “Tank” Penchukov, the accused 40-year-old Ukrainian leader of the JabberZeus Crew, has been arrested in Switzerland, according to a report from KrebsOnSecurity. Penchukov has been charged in the US since 2014 for his role in deploying and operating a version of the Zeus banking trojan. Read more:

Koxic & Key Group
Attacks with new ransomware strains named Koxic and Key Group were spotted this month. Read more:
AcridRain Stealer
Threat actors are advertising a new infostealer trojan named AcridStealer on underground forums. Per Sekoia, AcridStealer has all the features of a classic infostealer, meaning it can extract credentials from web browsers, crypto browser extensions, crypto wallet apps, and multiple desktop applications, such as email and messenger clients. The stolen data, along with a fingerprint of the infected host, is exfiltrated to a remote C&C server.
Updated on 2022-11-14
A crypto exchange suffered a massive heist and had to report bankruptcy. Indeed a bad day for crypto owners. Black Basta group has been making quite a name for itself in the cybercrime underground as it claimed a supermarket chain as its latest victim. In other news, Bahrain suffered cyberattacks right before an election. Read along for more news from the weekend.
More highlights from the past 24 hours
- An initial access broker claimed to have hacked into Deutsche Bank to gain access to 21,000 machines in the bank’s network. It is now offering network access for sale online. Read more: An initial access broker claims to have hacked Deutsche Bank
- Attackers targeted Bahrain official websites right before a parliamentary election. Bahrain News Agency and parliament websites remain offline. Read more: Bahraini websites hacked hours before parliamentary election
- Abraham’s Ax, an Iranian hacking group, claimed to have gained entry into the Saudi Ministry of Interior systems and released a proof-of-concept file. Read more: Iranian Hacking Group Abraham’s Ax claims hack on Saudi Ministry of Interior
- GitHub introduced a new private vulnerability reporting capability for security researchers to report any bugs found in their code to repository maintainers. Read more: GitHub Introduces Private Vulnerability Reporting for Public Repositories
Updated on 2022-11-13
New tool—Canary Hunter
Optiv security researcher Curtis Ringwald open-sourced Canary Hunter, a red-team tool meant to detect canary tokens installed across an organization’s network or files.
New tool—Shufflecake
The team at Kudelski Security has open-sourced a new tool named Shufflecake that can be used to “create multiple hidden volumes on a storage device in such a way that it is very difficult, even under forensic inspection, to prove the existence of such volumes.” Researchers said they developed this tool for “people whose freedom of expression is threatened by repressive authorities or dangerous criminal organizations,” such as activists, whistleblowers, and journalists. Read more: INTRODUCING SHUFFLECAKE: PLAUSIBLE DENIABILITY FOR MULTIPLE HIDDEN FILESYSTEMS ON LINUX
GitHub private vulnerability reporting
Code-hosting platform GitHub has added a new feature to its service to allow security researchers to report vulnerabilities in public repositories to their respective owners via a private channel. The new feature will allow sensitive security-related reports to be filed to repo owners without having to file a publicly-viewable entry in a repo’s Issues Tracker. Instructions on how repo owners can enable this feature are here. Read more: Privately report vulnerabilities to repository maintainers
CVE-2022-32895
Trend Micro has published a write-up on CVE-2022-32895, a vulnerability in the macOS PackageKit Framework that can be used by malicious apps to modify protected parts of the file system. The vulnerability is a variation of the older CVE-2019-8561 vulnerability. Read more: CVE-2019-8561: A Hard-to-Banish PackageKit Framework Vulnerability in macOS
“Users who fail to update their operating systems can be vulnerable to root privilege escalation, signature bypassing, and SIP bypassing. It is therefore imperative for users to install all updates to keep their systems secure.”
LiteSpeed server vulnerabilities
Palo Alto Networks’ Unit42 security team has published details about three vulnerabilities in the LiteSpeed open-source web server. The three bugs include an RCE, a privilege escalation, and a directory traversal issue. Read more: Unit 42 Finds Three Vulnerabilities in OpenLiteSpeed Web Server
BadBazaar
Security firm Lookout said it identified two suspected Chinese government surveillance operations that targeted its minority groups throughout the past years. The first campaign targeted Uyghurs and other Turkic ethnic minorities in China and abroad using a novel piece of malware known as BadBazaar, while the second campaign used spear-phishing messages on WhatsApp to infect Tibetan activist groups with malware known as Moonshine. Lookout said they linked the first campaign to a group known as APT15 (or Vixen Panda), while evidence suggested the second campaign was carried out by a group known as Poison Carp (or Evil Eye). Extensive previous reporting links both groups to the Chinese government. More in the company’s CyberWarCom slides, including some cool timelines. Read more: Lookout Discovers Long-running Surveillance Campaigns Targeting Uyghurs
Inlock and Xorist ransomware
Fortinet researchers have published a write-up on two new ransomware variants known as Inlock and Xorist. Read more: Ransomware Roundup: New Inlock and Xorist Variants
Free decrypter
Bitdefender released a free decrypter for the RanHassan ransomware, allowing victims to recover their files without paying the attacks. K7Security Labs has a technical analysis of the RanHassan (also known as DCDcrypt) here. Read more: RanHassan Ransomware Decryptor Now Available
State of Massachusetts sued
The Massachusetts Law Reform Institute, a nonprofit organization, has sued the state of Massachusetts on behalf of thousands of low-income families who had funds stolen from their food assistance benefits after they used their SNAP debit cards on ATMs compromised with card skimming devices. The goal of the lawsuit was to force the state to reimburse victims of SNAP card skimming, something the US Department of Agriculture (USDA), which funds the food assistance SNAP cards program, does not allow under the current rules, even for victims of obvious cybercrime. Read more: Lawsuit Seeks Food Benefits Stolen By Skimmers
Mastodon abuse
You’re not a true social network until someone uses your infrastructure for C2 comms. Mastodon
Attacks on US midterm elections infrastructure
Internet infrastructure company Cloudflare—which provides free services to state and local governments through the Athenian Project and to political campaigns through the Cloudflare for Campaigns programs—published a summary of what threats the company saw directed at these two projects over the last month and through the US midterm elections. Long story short, while some attacks were detected and mitigated, there was no super major cyber-attack that tried to compromise websites or disturb the US electoral process. Read more: 2022 US midterm elections attack analysis
17 scam domains seized
The FBI and the US Postal Inspection Service seized 17 websites that were part of a large-scale fraud operation. The websites posed as recruiting portals for work-at-home jobs, where US citizens were tricked into receiving stolen goods or stolen money and asked to reship the products or funds to another address controlled by the scammers. Officials said the operation had been going on since February 2021 and that hired applicants were paid $20 for each reshipped package.
Switzerland sees main “cyber threat” coming from ransomware
In its annual threat assessment report, the Swiss government said last week that it sees cybercrime, and specifically ransomware, as the main cyber threat to the country’s critical infrastructure, as opposed to state-backed APT groups. Read more: L’environnement politico-sécuritaire de la Suisse s’est durablement détérioré
“So far, the war in Ukraine has confirmed that in the context of armed conflicts, cyber means are above all used in a support function. They aim to reduce the adversary’s military capabilities and damage critical infrastructure. Given international interdependencies, such cyberattacks can also cause collateral damage and therefore indirectly affect Swiss facilities.”
Russian sanctions 200 US citizens
The Russian government has sanctioned 200 US citizens for their support of the Ukrainian government. Among the list of sanctioned Americans, who are now forbidden from entering Russia, there are also several infosec figures, such as Dmitri Alperovich, co-founder of Crowdstrike and founder and chairman of the Silverado Policy Accelerator, Chris Krebs, former CISA head and co-founder of the Krebs Stamos Group, and Jen Easterly, CISA’s current director. Read more: Заявление МИД России в связи с введением персональных санкций в отношении граждан США
EU Cyber Defence
The European Commission proposed an action plan last week that would boost the EU’s cyber defense capabilities and strengthen coordination and cooperation between civilian and military cyber-security organizations. The document also calls on member states to ensure EU cyber defense interoperability and coherence through common standards and asks the EU to develop “full-spectrum state-of-the-art cyber defense capabilities.” For this, the European Commission urges the cultivation of a strong and agile European cyber defense industry and for states to address “a real and alarming cyber skills gap” in its current defense workforce—with the European Cybersecurity Organization (ECSO) estimating that a total of 500 000 professionals are needed now in 2022 to cover all available job openings. Read more: Cyber Defence: EU boosts action against cyber threats
Apple sued for ignoring privacy settings
After two app developers found that Apple was collecting data about all its users even if they checked the “disable the sharing of Device Analytics” option in the App Store settings, two class-action lawsuits were filed last week against the tech giant in California and Philadelphia, respectively. Read more:
- Apple Is Tracking You Even When Its Own Privacy Settings Say It’s Not, New Research Says
- Apple getting sued over App Store user data collection
Microsoft blocks domain fronting on Azure
Microsoft has notified customers that it intends to “block any HTTP request that exhibits domain fronting behavior” starting on November 8, 2023. Domain fronting is a technique used to configure servers in a way to allow online services to bypass internet censorship. The technique has been widely used by Telegram to bypass censorship in Russia and Iran. With Microsoft’s decision, all three major cloud providers will have blocked domain fronting after both Google and Amazon Web Services blocked domain fronting back in 2018. Microsoft signaled it would crack down on domain fronting back in March 2021, but this week the company imposed a hard cut-off date for all its customers. A copy of the email Microsoft sent users last week is available here. Read more:
- A Google update just created a big problem for anti-censorship tools
- Amazon’s AWS just kicked some censorship-evading apps to the curb
- Securing our approach to domain fronting within Azure
DFX Finance crypto-heist
DeFi platform DFX Finance said it lost $4.185 million worth of cryptocurrency assets following an attack on its platform late last week. The company said the incident was identified as a reentrancy attack.
BAH breach
Intelligence services giant Booz Allen Hamilton disclosed a security breach last week to Montana’s OAG, revealing that a former employee illegally downloaded a report containing his colleague’s personal data from one of the company’s internal SharePoint servers. See breach notification letter here [PDF].
Irish health system ransomware victims to be contacted
More than 100,000 people whose personal information was stolen during Ireland’s health service ransomware attack last year will soon be contacted by authorities, per The Irish Times. Ireland’s health service was breached in 2021 by the Russia-based Conti ransomware gang, prompting the Irish government to task its military to help with the response. Thousands of appointments were forced to be canceled and some hospitals had to rely on paper records. Read more:
- HSE cyberattack: More than 100,000 people whose personal data stolen to be contacted
- HSE cyber-attack: Irish health service still recovering months after hack
- A year on: Inside the Defence Forces response against the HSE ransomware hack
Home truths about macOS
macOS is used by millions of people around the world (myself included, shocker), but the big question for many is when to upgrade to the newer operating system version. The security bug fixes (and security support!) is worth it, but there is a tradeoff for those who delay upgrading, because newer versions of macOS are so often full of bugs. This is worth the read if you’re trying to decide if the cost/benefit of immediate upgrades is right for you. Read more: Last Week on My Mac: Home truths about macOS
Australia faces consequences of standing up to ransomware
This week, the Australian government accused cybercriminals believed to be in Russia for the breach at Medibank, the country’s largest private health insurer after some of the stolen data was published online. The ransomware attack is a major incident for Australia, with close to 10 million people’s information stolen, including health data. The data includes some personal information and diagnosis codes. The incident is extremely compromising for about half of the population for years, potentially. The Australian company didn’t pay the ransom (per the government’s advice), which seems to be the only thing it did right, even if it did result in the most damaging data leak in Australia’s recent history. Read more:
- Australia Faces Consequences of Standing Up to Ransomware
- Australian police to Medibank hackers: ‘We know who you are’
- Australia tells Medibank hackers: ‘We know who you are’
- Medibank v the hackers: how the health insurer fell to a mass data theft
Updated on 2022-11-11
Microsoft finally could attribute the wave of Prestige ransomware attacks in Ukraine and Poland to a Russia-linked threat actor, who shares overlaps with another nation-state actor. While changing themes in phishing campaigns is a common practice for hackers, sometimes age-old themes of financial bait work too. Hackers are impersonating the Spanish tax agency with poorly built phishing pages. In other news, Uyghurs are under attack by two previously-undisclosed Android surveillance malware. Read along for more from the past 24 hours.
More highlights from the past 24 hours
- A new phishing campaign was found posing as Agencia Tributaria, the Spanish tax agency, in an attempt to pilfer credit card data. Read more: New phishing campaign posing as Spain’s Tax Agency
- Lookout researchers discovered two surveillance campaigns targeting Uyghurs in China and abroad. The threat actors are using BadBazaar and MOONSHINE Android surveillance tools. Read more: Lookout Discovers Long-running Surveillance Campaigns Targeting Uyghurs
- The European Commission proposed a cyber defense policy, urging member states to “significantly increase” cybersecurity investment in the light of attacks on energy, transportation, and space assets. Read more: Europe calls for joint cyber defense to ward off Russia
- Privacy and security framework compliance firm Laika raised $50 million in Series C funding, led by Fin Capital, with participation from J.P. Morgan Growth Equity Partners, Canapi, and ThirdPrime. Read more: Laika laps up $50M for its automated security compliance platform
Plesk vulnerability
Security firm Fortbridge has published details about a vulnerability in the Plesk web hosting automation software, which the company says was able to compromise via four CSRF vulnerabilities in its REST API. Read more: COMPROMISING PLESK VIA ITS REST API

CVE-2022-41049
Security researcher Kuba Gretzky published an analysis of CVE-2022-41049, a Mark-of-the-Web bypass patched earlier this week by Microsoft. Read more: Exploring ZIP Mark-of-the-Web Bypass Vulnerability (CVE-2022-41049)
Security updates
On the trail of Patch Tuesday, security updates have also been released for Apple and Cisco devices and the Google Cloud Platform.
TA423/Leviathan/RedLadon
At the CyberWarCon conference on Thursday, Proofpoint researchers said they linked cyber-espionage operations carried out by TA423 (also known as Leviathan and RedLadon) against Malaysian off-shore energy companies to kinetic maritime intimidation operations conducted by the Chinese Coast Guard in the South China Sea. See original research here: Rising Tide: Chasing the Currents of Espionage in the South China Sea
JSP web shell targeting Zimbra
Out of the blue and with no context, CISA published a malware analysis report (MAR) on a JSP web shell targeting Zimbra. Read more: Malware Analysis Report (AR22-314A) 10410305-1.v1 JSP Webshell
“Four CVEs are currently being leveraged against ZCS: CVE-2022-24682, CVE-2022-27924, CVE-2022-27925 chained with CVE-2022-37042, and CVE-2022-30333.”
Crypto-mining landscape
Antivirus maker Kaspersky published a report this week on the landscape of crypto-mining malware. Some of the report’s main findings are below.
- In Q3 2022, nearly one in six cases of exploiting well-known vulnerabilities were accompanied by a crypto-miner infection.
- Q1 2022 saw the biggest number of users (over 500,000) affected by malicious mining software and the smallest number of new malicious miner variants.
- The country with the highest number of attacked users was Ethiopia, where cryptocurrencies are banned officially.
- Monero (XMR) is the most popular cryptocurrency for malicious mining.
Scam gang disrupted in Ukraine
Ukraine’s Cyber Police said it raided and disrupted a local company that operated a call center linked to phone scams all over the world that defrauded users out of more than €200 million a year.
Cyber.org Range expands nationwide
A Louisiana pilot program called Cyber.org Range—designed to teach K-12 students cybersecurity skills—announced it would expand to all 50 US states after receiving funding, including from the US Cybersecurity and Infrastructure Security Agency. Read more:
“The CYBER.ORG Range is accessible to all K-12 students but is primarily geared toward high school students interested in learning core cybersecurity concepts and curriculum.”
Apple limits AirDrop in China
iPhone users in China will not be able to use the Airdrop file-sharing feature using the “Share to Everyone” option for more than 10 minutes. The change has rolled out to everyone this week with the release of iOS 16.1.1. The feature has been widely abused in recent weeks to secretly share anti-government posters and materials criticizing China’s leader Xi Jinping. It was also used in previous years to share instructions and other helpful materials during the Hong Kong anti-government protests. There is rampant—and obviously well-grounded—speculation that Apple might have caved in to a request/threat from the Chinese government. There is no technical reason to limit that feature to only 10 minutes. It’s actually a dumb idea since it will prevent the successful sharing of any larger files. Apple also told Bloomberg it also plans to expand this feature globally next year, in a serious hit to protesters and a helpful hand to all oppressive governments around the world. Read more:
- Apple to restrict ‘Everyone’ option in AirDrop to 10 minutes in China with iOS 16.1.1 [U]
- Apple Limits iPhone File-Sharing Tool Used for Protests in China
Kaspersky to discontinue VPN service in Russia
Russian security company Kaspersky said it would discontinue its Kaspersky Secure Connection VPN application for its Russian customers. The free version will be discontinued on November 15, while the paid/commercial version will end service at the end of the year. The news comes after the Russian government has spent the last year banning various VPN services within its borders. Read more:
- Приложение Kaspersky Secure Connection перестанет работать в России
- Kaspersky to kill its VPN service in Russia next week
Compensation for Yandex.Food users
The 13 users who sued Yandex after their personal information was stolen and dumped online were awarded a 5,000 rubles ($82) compensation (each) for their troubles by a Moscow court this week. Each had initially asked for at least 100,000 rubles ($1,650). Read more: Суд впервые взыскал с «Яндекс.Еды» компенсацию в пользу наших заявителей
Major breach in Hungary
A hacking group named Sawarim has breached eKRÉTA, the company behind a school management platform widely deployed across Hungary. The platform is believed to store the personal details of more than 720,000 Hungarian students, aged between 6 and 18 years. While the hackers told a local news outlet they don’t plan to release any of the students’ personal details, they have already begun leaking some of the software company’s source code, internal chats, and email messages, including with state officials. Read more: A fejlesztőcég megpróbálta elhallgatni a KRÉTA feltörését
Updated on 2022-11-10
WordPress is once again hard-pressed as researchers found thousands of websites compromised in a new campaign. Remember earlier in 2022 when Mandiant researchers identified an attack by APT29 against a European entity? New details about the attack vector have emerged. The Medibank breach keeps getting worse since hackers leaked the data like they threatened to. Read along to know what else transpired over the last 24 hours.
More highlights from the past 24 hours
- Data from Dtex revealed that 12% of all employees carry sensitive intellectual property with them when they leave their company, making it a concerning insider threat. Read more: Insider Risk on the Rise: 12% of Employees Take IP When Leaving Jobs
- Several county tax assessors and collector’s office employees in Arkansas were forced to shut down their computer servers, owing to a cyberattack at Apprentice Information Systems. Read more: County offices across Arkansas working without computers during possible breach
Updated on 2022-11-09
As midterm elections come to a close, cyberattacks are still going strong. A DDoS attack took down multiple Mississippi state websites. Experts expect more such disruptions. The healthcare sector is once again under trouble from Iranian hackers, warned the federal government. Remember the Vultur trojan? It amassed hundreds of thousands of downloads on the Android app store. Here are the top 10 highlights from the past 24 hours.
More highlights from the past 24 hours
- The HHS warned against Iranian threat actors impersonating doctors, reporters, and think tank researchers, conducting social engineering schemes to target the healthcare sector. Read more: Feds Warn of Iranian Threats to Healthcare Sector
- The Champaign County Clerk’s office, Illinois, reported suffering disruptions in computer server performance due to DDoS attacks on its servers and networks. Read more: Champaign County Clerk reports cyber-attacks on servers
- Threat actors are using a malicious Android installation package and the Spymax RAT variant to target Indian defense personnel. The RAT imitates the Adobe Reader app. Read more: Android RAT Group Targets Indian Defense Personnel
- Wib, an Israel-based API security firm, raised $16 million in a funding round led by Koch Disruptive Technologies, with Kmehin Ventures, Venture Israel, and others as participants. Read more: Wib Launches API Security Platform After Raising $16 Million
New tool—Microsoft Section52 ICS Forensics Tools
Microsoft has open-sourced this week a new collection of tools to enable investigators to identify suspicious artifacts on ICS environments and to detect compromised devices during incident response or manual checks. Read more:
New tool—Shennina
Cybersecurity engineer Mazin Ahmed has open-sourced a new tool this week named Shennina, a tool for automated host exploitation. Read more:
New tool—SpyGuard
Sekoia security researcher Félix Aimé has released a tool called SpyGuard, an enhanced version of TinyCheck, a tool to detect signs of compromise by monitoring network flows transmitted by a device.
Patch Tuesday
Yesterday was also November’s Patch Tuesday. We had security updates being released by Adobe, Microsoft, SAP, Android, VMware, Citrix, and others. This month, Microsoft has fixed 67 security flaws, including the ProxyNotShell vulnerabilities, and four actively-exploited zero-days:
- CVE-2022-41128 – an RCE in the JScript9 scripting language, detected in the wild by Google TAG
- CVE-2022-41091 – a MotW bypass also known as ZippyReads
- CVE-2022-41073 – an EoP in the Windows Print Spooler service, discovered by MSTIC
- CVE-2022-41125 – an EoP in the Windows CNG Key Isolation Service, detected by MSTIC and MSRC.
Ukraine Cyber Project
The National Security Archive—a project of the George Washington University in Washington, DC—has launched a new initiative called the Ukraine Cyber Project, in which researchers will document the role of cyber operations in Russia’s invasion of Ukraine and how they helped augment traditional kinetic warfare.
“Although Russia’s overt resort to cyberattacks has not matched the level of intensity most observers expected – a lesson in itself – the Ukraine war has offered many fascinating insights into topics such as: how smaller states can effectively counter the actions of a larger aggressor; the importance of alliances and cooperative relationships among cyber actors; the key role of the private sector and the dynamics of its interactions with governments; the wide-ranging impact hackers have had and the mix of motivations behind their actions, in addition to the nature of their connections to governments they used to consider bitter adversaries.”
Unknown APT
CYFIRMA researchers have also studied the attacks of an unknown APT that has targeted the personnel of the Indian Defence Force with malicious Android applications. Read more: Unknown Nation-Based Threat Actor Using Android RAT to Target Indian Defence Personnel
Elibomi variants
Trend Micro has analyzed a phishing and malware campaign targeting the customers of Indian banks with mobile malware strains like FakeReward, AxBanker, and Elibomi (including two variants known as IcRAT and IcSpy). Read more: Massive Phishing Campaigns Target India Banks’ Clients
Calls for DDOS attacks on US election day
Wordfence researchers said they’d seen a pro-Russian hacktivist group named “The People’s Cyberarmy” call on its members and fellow hacktivist groups to launch DDOS attacks on websites linked to the American Democratic party on November 8, during the US midterm elections. Read more: Russian Hacktivist Group Targets Political Websites with DDOS Attacks
DeimosC2
Trend Micro also has a breakdown of DeimosC2, an open-source command-and-control framework that has been recently gaining adoption with malware gangs. Read more: DeimosC2: What SOC Analysts and Incident Responders Need to Know About This C&C Framework
Former Deloitte employee behind FIFA hacks
Deloitte said it fired an employee named Aditya Jain, who was exposed over the weekend as one of the individuals behind WhiteInt, an India-based hacker-for-hire cyber-mercenary group that allegedly helped the Qatari government hack FIFA officials in the run-up of Qatar receiving hosting rights for the 2022 Soccer World Cup. Read more:
Hushpuppi sentenced
A US judge sentenced Ramon Abbas, also known as “Ray Hushpuppi,” an infamous BEC scammer, to 11 years in federal prison. The 40-year-old Nigerian national was also ordered to pay more than $1.7 million in restitution back to two victims of his BEC scams, estimated to be in the realm of tens of millions of US dollars. Read more: Nigerian Man Sentenced to Over 11 Years in Federal Prison for Conspiring to Launder Tens of Millions of Dollars from Online Scams
Cyber-attack cripples Mexico’s transportation system
According to a report, Mexico’s transportation ministry has stopped issuing new permits, license plates, and driver’s licenses for commercial truck operators until December 31 because of a cyberattack that hit the IT infrastructure of the Secretariat of Infrastructure, Communications and Transport (SICT) in late October. Read more:
- Borderlands: Cyberattack disrupts Mexico’s transportation system
- Informa SICT que software malicioso no dañó sistemas internos ni vulneró datos personales
Pando Rings crypto-heist
DeFi platform Pando said it was the target of a hack last Saturday when a threat actor tried to steal more than $70 million worth of cryptocurrency from the platform’s wallets. The company said it managed to freeze $50 million of the stolen funds, but the attacker successfully stole more than $21.8 million of its funds. Pando said the hacker used an Oracle attack against one of its protocols and is still hoping to negotiate with the attacker to return some of the stolen funds. Read more: Alert to Pando Community:Hack of Pando Rings
Updated on 2022-11-08
A breach here and a breach there and a whole lot of consequences. A new group of threat actors leaked the stolen data belonging to an IT vendor in Saudi Arabia. Along similar lines, a Canadian packaged meats company suffered system outages due to a cyber incident. In a new update, researchers discovered that the new Azov ransomware is a wiper in disguise. Read along for more from the past 24 hours.
More highlights from the past 24 hours
- Justice Blade threat actors published online the stolen data, including personal information, CRM records, contracts, and others, from Smart Link BPO Solutions. Read more: ‘Justice Blade’ Hackers are Targeting Saudi Arabia
- Maple Leaf Foods, Canada, confirmed suffering a cybersecurity incident that caused system outages and disrupted operations. Investigation is ongoing. Read more: Maple Leaf Foods suffers outage following weekend cyberattack
- Massive phishing campaigns were found targeting the clients of seven major Indian banks with Elibomi, IcSpy, IcRAT, FakeReward, and AxBanker malware families. Read more: Massive Phishing Campaigns Target India Banks’ Clients
- The Albany City School District suffered constant cyberattacks on its computer systems and warned teachers and students to not use the internet for three days. Read more: Attempted cyberattack leads to internet shutdown at Albany schools
- Secure and compliant team communication app Worldr raised $11 million in seed funding led by Molten Ventures, with participation from IQ Capital, Playfair Capital, and others. Read more: Worldr raises £10m to let businesses control their messaging data
Updated on 2022-11-07
It’s a fresh week and we have a fresh set of LockBit victims. While the ransomware group threatened to leak the data belonging to a management consulting firm, it already went a step further in an attack on a school. In other news, Transparent Tribe is back with a new campaign against Indian government entities. Read along for the top 10 highlights from the weekend.
More highlights from the past 24 hours
- Harcourts, an Australian real estate agency, confirmed suffering a data breach last month, which potentially compromised the names, contact details, and signatures of tenants, landlords, and tradespeople. Read more: Aussie real estate agency Harcourts reveals names, addresses possibly compromised in cyber attack
- A ransomware attack against Norman Public Schools, Oklahoma, disrupted operations. School officials are warned against using their school-issued devices or connecting it to any network. Read more: Norman Public Schools experiencing malicious ransomware attack
- MITRE released an updated version of the Attack Flow project, which would allow defenders to gain better visibility into a potential threat. Read more: MITRE Attack Flow Gives CISOs Valuable Context for Better Risk Management
- Password manager 1Password acquired Passage, a developer-first passwordless authentication firm. Terms of the deal weren’t disclosed. Read more: 1Password acquires Passage to make progress toward a passwordless future
Solend crypto-heist
DeFi platform Solend said it lost $1.26 million worth of cryptocurrency following an Oracle attack on its platform, targeting the Hubble (USDH) currency.
Successful defense
In a post-mortem, pNetwork said it successfully defended an attack on its pGALA token. Read more: pGALA post-mortem: measures taken to safeguard the ecosystem from malicious actors and recovery plan
Personal Paraguay hack
Paraguay’s Personal ISP service disclosed last week that it was the victim of a cyber-attack.
Qatar spied on FIFA officials
A report in Swiss media claims that Qatar officials “orchestrated a large-scale and long-standing intelligence operation against FIFA officials with the help of former CIA operatives” in the run-up to Qatar being awarded the FIFA 2022 World Cup. The report claims that “the highest echelons of the Qatari government were involved” and that the cyber-espionage campaign targeted critics inside and outside FIFA alike.
“The scale of the espionage activities is considerable. One sub-operation alone involved the planned deployment of at least 66 operatives over nine years. The budget amounted to $387 million. And the activities spanned five continents.”
The AP reported last week that the FBI started an investigation against Kevin Chalker, a former CIA agent and the founder and CEO of Global Risk Advisors, the company that helped the Qatari government orchestrate this operation. Read more:
- ‘Project Merciless’: how Qatar spied on the world of football in Switzerland
- FBI probing ex-CIA officer’s spying for World Cup host Qatar
Armenian cyber-attacks
Azerbaijan officials said they successfully mitigated “large-scale cyberattacks by Armenia” following the second Karabakh War in September 2022. No details were provided on what those cyber-attacks were. Read more: Azerbaijan prevented large scale cyberattacks by Armenia during Second Karabakh War – official
NCCoE guidance
The National Cybersecurity Center of Excellence (NCCoE), a part of the National Institute of Standards and Technology (NIST), published guidance on how the manufacturing and industrial sectors can respond to cyber-attacks on their OT/ICS networks. Read more: Responding to and Recovering from a Cyber Attack: Cybersecurity for the Manufacturing Sector
UK DfE lapse
An investigation by the UK Information Commissioner’s Office (ICO) found that the Department for Education (DfE) had a major privacy lapse in its LRS database. The LRS system was designed to let educational institutions inspect a record of a pupil’s qualifications before admittance to courses or special programs, but British press and the ICO confirmed that the DfE granted access to the system to a company named Trustopia, which then used it to allow online gambling companies to verify if a new account was over 18. Read more: Department for Education warned after gambling companies benefit from learning records database
“This data sharing meant the information was not being used for its original purpose. This is against data protection law. The ICO issued a reprimand to the DfE setting out clear measures they need to action to improve their data protection practices so children’s data is properly looked after.”
ACSC threat assessment
Australia’s Cyber Security Centre (ACSC) published on Friday its annual cyber threat report for the period of July 2021 to June 2022. Some of the report’s main findings include:
- An increase in financial losses due to BEC to over $98 million.
- A rise in the average cost per cybercrime report to over $39,000 for small businesses, $88,000 for medium businesses, and over $62,000 for large businesses.
- A 25% increase in the number of publicly reported software vulnerabilities.
- Over 76,000 cybercrime reports (13% up from the previous year).
- A cybercrime report every 7 minutes on average.
- 150,000 to 200,000 SOHO routers in Australian homes and small businesses are vulnerable to compromise.
Read more: ACSC Annual Cyber Threat Report, July 2021 to June 2022
Atlantis Cyber Army
Israeli cybersecurity firm CyberInt said it found a new mercenary hacking group Atlas Intelligence Group, also known as the Atlantis Cyber Army. The company said the group is led by an individual going by the name of Mr. Eagle, and they provide services such as exclusive data leaks, DDoS, RDP, and other methods of access to organizations. A Times of Israel report makes this look like some top apex hacker-for-hire actor, but a CyberInt report from July actually paints the picture of a run-of-the-mill initial access broker advertising stuff on Telegram. Read more:
- Israeli cyber intel firm shines bright light on new, shadowy cybercrime collective
- Atlas Intelligence Group (A.I.G) – The Wrath of a Titan
Hamas expanding in cyber domain
A report from the Atlantic Council highlights Hamas’ efforts to expand into the cyber domain, where it is slowly becoming a capable threat actor. Read more: The cyber strategy and operations of Hamas: Green flags and green hats
” [The] analysis will show how Hamas’s cyber activities do not indicate a sudden shift in strategy but, rather, a realignment that augments operations. In other words, offensive cyber operations are a new way for Hamas to do old things better. As the title of this report suggests, Hamas is like a green hat hacker—a term that is not specific to the group but recognized in the information security community as someone who is relatively new to the hacking world, lacking sophistication but fully committed to making an impact and keen to learn along the way. Hamas has demonstrated steady improvement in its cyber capabilities and operations over time, especially in its espionage operations against internal and external targets. At the same time, the organization’s improvisation, deployment of relatively unsophisticated tools, and efforts to influence audiences are all hallmarks of terrorist strategies. This behavior is in some ways similar to the Russian concept of ‘information confrontation,’ featuring a blend of technical, information, and psychological operations aimed at wielding influence over the information environment.”
New Sudo vulnerability
The Sudo project patched last week a major vulnerability tracked as CVE-2022-43995 that can allow a threat actor to run code on a vulnerable system.
“This can be triggered by arbitrary local users with access to Sudo by entering a password of seven characters or fewer. The impact could vary depending on the system libraries, compiler, and processor architecture.”
PrivacyCon 2022 videos
Talks from the FTC’s PrivacyCon 2022 conference, which took place last week, are now available on the agency’s website. Read more: PrivacyCon 2022
NSA job openings
The NSA has a fast-track program for former employees, including for cybersecurity roles.
IDA Pro community
Updated on 2022-11-06
The most vulnerable place on the planet
From one extreme environment to the next… It’s no secret that the internet is just a series of tubes — well, specifically undersea cables — that connect the world together. (If that just blew your mind, check out the submarine cable map.) But cables are vulnerable to a raft of issues. Fishing trawlers, earthquakes, and terrorism all damage cables, and sometimes for weeks at a time, like Tonga and Liberia, which have only one cable each — and Egypt, which features in this Wired story. Read more:
- The Most Vulnerable Place on the Internet
- Submarine Cable Map
- The race to reconnect Tonga
- Massive cyber-attack grinds Liberia’s internet to a halt
Fizz threatened to sue student security researchers after finding bugs
Fizz (previously Buzz), a Stanford startup that bills itself as an “anonymous” social network, was riddled with security bugs that allowed three security researchers, who are Stanford University students, to deanonymize users’ posts. The trio responsibly disclosed the bugs to the app’s founders Ashton Cofer and Ted Solomon, who then threatened to sue them if the researchers disclosed the bugs. The EFF defended the team pro bono, and they went forward and published their findings — and the lawyers’ letter (brilliant!). More from @Riana_Crypto in the tweets. Read more: Opinion | Fizz previously compromised its users’ privacy. It may do so again.
How two-factor works in Antarctica
If you’ve ever wondered how two-factor works in one of the most remote, networkless places on earth, wonder no longer, as this blog explains how. The challenge is real: there are lots of different types of two-factor, all supported by different sites, and that can be difficult when you absolutely have to rely on near non-existent cell service. Read more: SMS Multifactor Authentication in Antarctica
NSA watchdog says one analyst’s surveillance project went ‘too far’
The NSA’s inspector general found that an “experienced” analyst working at the U.S. spy agency broke the rules and likely the law, according to a heavily redacted 2016 report that just became public after a lengthy FOIA battle. Details of the project aren’t known but the program was centered on SIGDEV, or the ability to find and improve intelligence gathering, like eavesdropping, which may have scooped up Americans’ communications (which is illegal under U.S. law, even if it’s often violated). The project was concerning enough for two whistleblowers to come forward internally. For those asking “what’s new” in all this? Even in a post-Snowden agency, new surveillance abuses are still being discovered, even today. @JasonLeopold explains more in his thread. Read more:
- NSA Watchdog Concluded One Analyst’s Surveillance Project Went Too Far
- FBI and NSA violated surveillance law or privacy rules, a federal judge found
States look to secure U.S. election ‘weak points’ ahead of midterms
With just days before the U.S. midterms and Twitter is a free-for-all on verified accounts, there’s concern (like always!) that bad actors will use this time for election interference. NBC News looks at some of the pressing issues ahead of election day, like election reporting websites — an easy target by cybercriminals for simple cyberattacks — that could sow discord and confusion about the vote count. NBC also says more than 100 state and local jurisdictions are still seeking help from the federal government to ensure that their election-related systems are secure, even if the risk of an attack by foreign hackers is practically impossible given most election infrastructure is offline. The federal “bandwidth issue” just goes to show this area needs more funding and resources (you know, so we can keep that wonderful place we call home!) Also, bonus @CISAJen was interviewed by CBS News last Sunday, the transcript is worth the read if you want a tl;dr of where we are in terms of election security today. Read more:
- After a series of cyberattacks, states look to secure election results websites
- Transcript: CISA Director Jen Easterly on “Face the Nation,” Oct. 30, 2022
- More than 100 election jurisdictions waiting on federal cyber help, sources say
Updated on 2022-11-04
Another day, another LockBit victim. This time, the gang added a multinational automotive group to its leak site and threatened to release all the stolen data. A cyber incident at a Boeing subsidiary rendered flights inoperable, while the firm struggles to restore services. Another U.S. community college was added to the long line of educational institutions victimized by cyberattacks. Read along for the top 10 cybersecurity highlights from the past 24 hours.
More highlights from the past 24 hours
- North Idaho College fell victim to a cyberattack and had to shut down its college networks. While most critical systems were restored within 24 hours, investigation is still ongoing. Read more: North Idaho College recovering from cyberattack that led to network shutdown
- A report by the Australian Signals Directorate revealed that cybercrime in Australia spiked by 13% to 76,000 incidents in 2020–2021. The average loss rose by 14% to $39,000 and $62,000 for small and large businesses, respectively. Read more: Cyberspace ‘a battleground’ as reports of cybercrime in Australia jump 13%
- At least 85 people in Singapore lost around $237,000 since January to scam emails purporting to come from SingPost and Singtel, revealed Singapore police. Read more: Victims lose $237,000 amid resurgence in SingPost and Singtel phishing scams: Police
- AstraZeneca left out a list of credentials, including AZ&ME app data, online for over a year, exposing confidential patient information. The pharma giant blamed ‘user error’. Read more: AstraZeneca password lapse exposed patient data
- Applications security startup Apiiro raised $100 million in Series B funding led by General Catalyst, with Greylock and Kleiner Perkins as participants. Read more: Applications security startup Apiiro pulls in $100M Series B from A-list investors
- Customer protection platform Darwinium raised $10 million in seed funding round co-led by Blackbird and Airtree. Read more: Darwinium raises $10 million to deliver a new approach to customer protection
Ransomware attack cripples 75 German schools
Seventy-five schools across Bavaria—with 55 schools in Munich alone—have been cut off from their internal databases after a ransomware attack hit a server operated by the Munich-Land province. Officials said they discovered the ransomware attack as soon as it happened, after a mysterious server restart, and shut down the affected system until remediation. Officials believe the attacker gained access to the server after phishing one of their employees. Read more: Hackerangriff auf Schulverwaltung: Phishing-Mail wohl Auslöser
Ransomware cripples Polish hospital
A ransomware attack this week has crippled the activity of a major hospital in Lodz, Poland’s third-largest city. According to local media, the attack took down the hospital’s entire IT network, forcing doctors to issue prescriptions on paper. Tomographs, magnetic resonance imaging, and other computerized testing equipment have been down since the attack, but officials hope to have everything back up by the end of the week. The attack comes two weeks after the Polish government made more than 200 million zlots (~$41.5 million) available to healthcare organizations as a cybersecurity upgrade fund. Read more:
- Atak hakerów na Centrum Zdrowia Matki Polki. NFZ ma pieniądze na cyberbezpieczeństwo
- Aktualności Centrali
Skyward crypto-heist
DeFi platform Skyward Finance confirmed on Wednesday a report that a hacker exploited a vulnerability in its smart contract and stole $3 million worth of cryptocurrency. Read more: Skyward finance exploit allegedly results in $3M loss
IP addresses as spoils of war
At the RIPE85 conference held last week in Belgrade, members of the RIPE organization—which manages the IP address space of European countries—have decided to impose a “temporary freeze” on the transfer of Ukrainian IP addresses to new owners, especially to Russian companies. According to a report from Techaint and a message sent via the organization’s mailing list, the request to impose this block came from Ukrainian IT companies in areas occupied by the Russian Army, who have had IP address blocks stolen and then illegally transferred to Russian network operators. Read more:
Twitter InfoOps
Analysts from the Digital Forensic Research Lab and the Stanford Internet Observatory have published details about six Twitter bot networks—five from China and one from Iran—that tried to sway the discourse about the upcoming US 2022 Midterm Elections and various geopolitical issues, such as the Russia-Ukraine war and America’s foreign policy on China. Researchers said the networks used follow-back practices in an attempt to integrate themselves into “highly-active” Twitter communities on both right- and left-leaning US political groups. All six networks tried to pose as US citizens, but despite this, they failed to garner any online following or visibility for their content. Read more: Assessing Inauthentic Networks Commenting on the US Midterms
“The networks did not appear to achieve significant engagement from the online public or strong infiltration within American political-activist networks on Twitter; the most-engaged tweet had 31,303 engagements, and of the 705,864 tweets spanning the six sets, 592,333 had zero likes. While these inauthentic accounts at times participated in conversations alleging fraud in 2020, and commented about concern for the integrity of the midterms, these conversations remain dominated by authentic activity from political influencers, politicians, and the American public. Nonetheless, we present our findings to help inform the American public’s understanding of foreign influence activities, and additionally observe here that the diligence of Twitter’s integrity team ensured that these networks were disrupted before they managed to obtain significant reach. “
Microsoft extends help to Ukraine
Microsoft announced Thursday it was extending its pledge to help the Ukrainian government with IT services throughout Russia’s invasion with another $100 million, bringing the company’s total commitment so far to $400 million worth of covered costs. This help includes providing hosting for the Ukrainian government’s IT systems on its cloud servers to avoid physical compromise by Russian troops and cybersecurity protection and incident response services in the face of a wave of cyberattacks from Russia’s numerous state-sponsored threat groups. Read more: Extending our vital technology support for Ukraine
Russia’s search for a Windows replacement
The Russian Ministry of Digital Development ran a survey among the country’s biggest IT firms to identify the best replacement for the Windows OS across Russian government and private-sector networks. According to Kommersant, all three are Linux-based operating systems, named Astra Linux, ALT OS, and Red OS, respectively. The Russian government is seeking a replacement after Microsoft pulled out of Russia, stopped delivering security updates to Russian systems, and started blocking Russians’ access to Windows installation files. Read more: Минцифры нацеливает ОС
Tax fraud ring indicted
The US DOJ charged eight suspects this week for a massive tax fraud scheme that took place between 2015 through 2019. DOJ officials said the group purchased credentials from the dark web to the internal networks of several Certified Public Accounting (CPA) companies across the US. Officials said the group accessed CPA networks, stole the tax returns of “thousands of taxpayers,” created six tax preparation businesses in south Florida, and used those companies to file more than 9,000 fraudulent tax returns in the victims’ names, hijack tax refunds towards their own accounts. Read more: Band Of Cybercriminals Responsible For Computer Intrusions Nationwide Indicted For RICO Conspiracy That Netted Millions
Russian hacker released from prison
Vladimir Drinkman, a Russian hacker who stole more than 160 million credit card numbers from several US payment processors in the late 2000s, was released from prison this week after serving a 12-year sentence, according to RadioFreeEurope. Read more:
- Two Russian Nationals Sentenced to Prison for Massive Data Breach Conspiracy
- Russian Hacker Behind Massive Data Breach Released From U.S. Prison
Adware explosion
Antivirus maker Avast said it observed an explosion in adware activity in Q3 2022, following distribution campaigns specifically aimed at Central, South, and Eastern Europe. In addition, the company also noted that despite cryptocurrency exchange rates crashing this quarter, illegal cryptomining operations remained at a steady pace, decreasing by only 4% from the previous quarter. Read more: Avast Q3/2022 Threat Report
ENISA threat landscape
ENISA, the EU’s cybersecurity agency, published this week its threat landscape report, covering a reporting period starting from July 2021 up to July 2022. Some of the most interesting stats include:
- More than 10 TBs of data are stolen monthly in ransomware attacks.
- More than 60% of affected organizations appear to have paid the ransom demand.
- 66 zero-day vulnerabilities were disclosed in the reporting period.
- The DDoS landscape reached its all-time activity peak in July 2022.
- Third-party incidents, such as supply chain attacks, accounted for 17% of all reported intrusions in 2021, up from only 1% in 2020.
Download ENISA Threat Landscape 2022
P2P botnets
Qihoo 360’s Netlab network security division has a review of today’s most active IoT P2P-based botnets. The list, based on botnet size and activity, includes Pink, Hajime, Mozi, FritzFrog, and Panchan. Read more: P2P Botnets: Review – Status – Continuous Monitoring
Robin Banks moves to Russia
Cybersecurity firm IronNet said that after they exposed a new phishing-as-a-service (PhaaS) platform named Robin Banks earlier in July, the service had to relocate servers to a Russian hosting provider after Cloudflare booted the gang off its infrastructure. Read more:
Crimson Kingsnake BEC gang
Abnormal Security said it observed a BEC gang they have codenamed as Crimson Kingsnake target organizations across the globe by impersonating law firms. The security firm said that based on its investigation, “at least some of the actors associated with Crimson Kingsnake may be located in the United Kingdom.” Read more: Crimson Kingsnake: BEC Group Impersonates International Law Firms in Blind Third-Party Impersonation Attacks
OrcusRAT
The ANY.RUN team has a report out on the Orcus remote access trojan, first released in 2016 by a Canadian coder, but still active even today. Read more: What is Orcus RAT? Technical Analysis and Malware Configuration
Elbie and Surtr ransomware
AhnLab warned this week about a campaign distributing the Elbie ransomware across South Korea disguised as an IE add-on (out of all the stupid distribution lures). They also published a second warning about a campaign distributing the Surtr ransomware. Read more:
- Elbie Ransomware Being Distributed in Korea
- Surtr Ransomware Being Distributed in Korea
- Surtr Ransomware Pays Tribute to REvil
Next.js vulnerability
A vulnerability in the IPX component of Netfify’s Next.js JavaScript framework allows a persistent cross-site scripting (XSS) and full-response server-side request forgery (SSRF) attack on any website that relies on the framework, including many of today’s JS-based static site generators and many cryptocurrency portals. Read more:
- Exploiting Static Site Generators: When Static Is Not Actually Static
- Exploiting Web3’s Hidden Attack Surface: Universal XSS on Netlify’s Next.js Library
Intel 471 acquires SpiderFoot
Threat intelligence giant Intel 471 announced it acquired this week SpiderFoot, a provider of open-source intelligence, attack surface management, and digital investigations resources. Read more: Intel 471 Acquires SpiderFoot
HUMAN acquires clean.io
HUMAN Security (formerly White Ops) announced it acquired clean.io, a service for protecting websites against malvertising and e-commerce fraud. Read more: HUMAN Acquires Anti-Malvertising Leader, clean.io, to Enhance Protection Across the Media Ecosystem
Updated on 2022-11-03
The FakeUpdates malware is back in a new supply chain attack campaign, affecting media organizations across the U.S. Vodafone Italia started notifying its customers of a September data breach. And once again, we have a crypto hack. A hacker stole millions worth of assets from a cryptocurrency derivatives firm. Read along to know what transpired in the cyberspace over the past 24 hours.
More highlights from the past 24 hours
- Vodafone Italia is notifying its customers of a data breach at its partner FourB S.p.A., compromising contact details, subscription details, and identity documents. Read more: Vodafone Italy discloses data breach after reseller hacked
- A technical glitch forced the U.K’s Royal Mail Click and Drop to shut down its website. The data leak led to some customers accessing others’ order information. Read more: Royal Mail customer data leak shutters online Click and Drop
- Managed detection and response provider Binary Defense Systems raised $36 million in first institutional growth equity funding round led by Invictus. Read more: Binary Defense Raises $36 Million From Invictus Growth Partners to Propel Rapid Expansion as the Most Trusted MDR Platform
- California-based cybersecurity provider Akto bagged $4.5 million in seed funding. The startup aims to mitigate cyber threats by making a real-time inventory of APIs for DevSecOps security. Read more: API security key to protecting DevSecOps pipelines, Akto raises $4.5M in funding
Updated on 2022-11-02
Dropbox fell victim to a phishing campaign impersonating CircleCI and ended up exposing over a hundred GitHub repos. Once again, another unprotected ElasticSearch database belonging to Amazon was found leaking a massive amount of data. In other news, Thales was hacked by LockBit 3.0, who is now threatening a data leak. Here are the top 10 highlights from the past 24 hours.
More highlights from the past 24 hours
- An ElasticSearch database, belonging to Amazon, was found leaking 215 million records of pseudonymized viewing data. Dubbed Sauron, the database contained Prime Video viewing habits. Read more: Leaked Amazon Prime Video Server Exposed Users Viewing Habits
- New report by the U.S. Treasury states that financial institutions in the country reported a loss of $1.2 billion to ransomware attacks and ransom in 2021. Read more: US Treasury: Financial institutions reported $1.2 billion in ransomware losses in 2021
- Threat actors are using a new spyware, named SandStrike, against the Persian-speaking practitioners of the Bahá’í faith. The malware is propagated via a malicious VPN app for Android users. Read more: New SandStrike spyware targets Android users with booby-trapped VPN application
- Osaka General Medical Center was forced to suspend non-emergency outpatient operations and services, following a ransomware attack on its electronic medical record system. Read more: Osaka hospital suspends services after ransomware cyberattack
- The CISA issued two fact sheets aiming to highlight threats faced by systems and accounts with a certain form of MFA implemented. It recommends implementing phishing-resistance MFA. Read more: CISA Publishes Multi-Factor Authentication Guidelines to Tackle Phishing
Apache Batik vulnerability
Details and a PoC are available for an SSRF-to-RCE vulnerability in Apache Batik, a Java library for working with SVG images. The vulnerability is tracked as CVE-2022-40146. Read more:
- VULNERABILITIES IN APACHE BATIK DEFAULT SECURITY CONTROLS – SSRF AND RCE THROUGH REMOTE CLASS LOADING
- cckuailong/CVE-2022-40146_Exploit_Jar
Checkmk vulnerabilities
SonarSource researchers have published details on several vulnerabilities in Checkmk, a tool and service for IT infrastructure monitoring. Read more: Checkmk: Remote Code Execution by Chaining Multiple Bugs (1/3)
Impersonate attack
Orange’s SensePost team published details about a new way to compromise Windows domains by abusing access tokens. The token exploit mechanism does not rely on LSASS, meaning it can bypass many EDR solutions. The code for this attack is available on GitHub. Read more:
No Hat 2022 videos
Talks from the No Hat 2022 security conference, which took place two weeks ago, are available on YouTube.
APT trends report
Kaspersky has also published its quarterly APT threat and trends report, widely regarded as one of the most comprehensive in the industry. Now, for the first time, in a video version as well. Read more: APT trends report Q3 2022
PayPal bug exploited
Forcepoint researchers said they identified a bug in the PayPal service that allows phishing gangs to send legitimate PayPal invoices for non-existent products/services. The company says that PayPal has yet to respond to its report. Read more: Hackers Exploit PayPal Invoicing Bug to Launch Advanced Phishing Attacks
Phishing kit stats
In its quarterly DNS threat report, Akamai researchers said they tracked 299 unique phishing toolkits being used in attacks in the wild in the third quarter of 2022. In addition, the company also reported that 14% of customer devices contacted a malicious domain and that DNS-over-TLS adoption rose by 40% from the previous quarter. Read more: Akamai DNS Threat Report — Q3 2022
Azov wiper
Several security researchers have spotted a new destructive data-wiping malware strain being deployed on computers across the world in limited numbers over the past few days. According to current evidence, the malware is deployed on computers that have been previously infected with the SmokeLoader malware. Once deployed, the malware wipes user files and leaves a ransom note behind, trying to pose as an attack by the Azov ransomware. The ransom note claims the ransomware was developed by Polish malware researcher Aleksandra “hasherezade” Doniec in an attempt to bring attention to Russia’s invasion of Ukraine, which is obviously a ruse meant to disguise its true origin and destructive actions. Read more: New Azov data wiper tries to frame researchers and BleepingComputer
US Treasury ransomware stats
On the day of the International Counter Ransomware Summit, the Financial Crimes Enforcement Network (FinCEN) unit, part of the US Treasury Department, published statistics [PDF] on ransomware-related events reported by banks and other financial institutions through Bank Secrecy Act (BSA). FinCEN said that in 2021, filings related to suspected ransomware payment “substantially increased from 2020,” amassing to almost $1.2 billion. The agency estimates that roughly 75% of these payments were made to ransomware gangs located in Russia. Read more: FinCEN Analysis Reveals Ransomware Reporting in BSA Filings Increased Significantly During the Second Half of 2021
New CISA guidance
The US Cybersecurity Infrastructure and Security Agency has released guidance urging organizations and federal agencies to roll out phishing-resistant multi-factor authentication (MFA) [PDF] and number-matching protections if they use mobile push-notification-based MFA [PDF].
Ransomware summit
The White House is hosting this week the second edition of the International Counter Ransomware Summit, a two-day event where members from more than three-dozen countries and a dozen private sector companies will be discussing ways to address the current threat posed by ransomware gangs. Read more:
- Background Press Call by a Senior Administration Official Previewing the Second International Counter Ransomware Initiative Summit
- White House invites dozens of nations for ransomware summit
Cisco disables Meraki networks in Russia
US networking equipment vendor Cisco allegedly disabled WiFi networks managed through its Meraki service in Russia. According to multiple online reports, the company failed to give customers any warning and just renamed all networks in Russia as “12345-Sanctions.”
Updated on 2022-11-01
The use of privacy-violating tracking mechanisms in various online services has become a norm. However, it can lead to a breach of patient information as disclosed by a North Carolina-based hospital system in a case impacting nearly half a million people. The not-so-hidden secret behind the surge in ransomware activity is the sale of access to hundreds of corporate networks for a mere few million bucks, researchers revealed in a new report. Meanwhile, a new attack campaign has been found exploiting security software to target Japanese organizations. Continue reading for more scoops from cyberspace in the last 24 hours.
More highlights from the past 24 hours
- North Carolina-based WakeMed Health and Hospitals reported a data breach impacting nearly 500,000 individuals, owing to its use of Facebook’s Pixel website tracking code in patient portals. Read more: Second Health Entity Reports Breach Tied to Meta Pixel Use
- U.S. Bank notified some customers that their personal information was accidentally shared by a third-party vendor. The incident affected 11,000 customers with closed credit card accounts. Read more: U.S. Bank data breach impacts 11K customers
- The White House is set to host a meeting of officials from 37 countries and 13 global companies to address the growing threat of ransomware and other cybercrimes, including the illicit use of cryptocurrencies. Read more: Cyber officials from 37 countries, 13 companies to meet on ransomware in Washington
- Label printing service provider Multi-Color Corporation (MCC) notified employees of a recent cyberattack that may have compromised their personal information, including personnel files and information on enrollment in its benefits programs. Read more: Label Giant Multi-Color Corporation Discloses Data Breach
- An Experian product used by organizations to verify customer identity could be exploited to expose partial Social Security numbers, a researcher found through testing several organizations that use the product. Read more: Experian tool exposed partial Social Security numbers, putting customers at risk
- A malvertising campaign abusing Google ads was found redirecting users looking for the GIMP photo editing utility to a phishing page delivering a malicious setup file. Read more: Google ad for GIMP.org served info-stealing malware via lookalike site