Table of Contents
- What you need to know about the new zero-day, Springshell
- FBI: Triton Malware is Being Used Against Energy Companies
- CISA Adds 66 Flaws to Known Exploited Vulnerabilities Catalog
- Dept. Of Health and Human Services Office of Civil Rights Enforcement Actions
- Sophos Patches Firewall Vulnerability
- Windows Driver Blocker Added to Defender
- Chrome and Edge Updates Fix Flaw that is Being Actively Exploited
- Ukrtelecom ISP Experienced Cyber Attack
- Replay Vulnerability Can be Exploited to Unlock and Start Honda Automobiles
- Prison Sentence for Ransomware
- VMware Releases Fixes for Carbon Black App Control Vulnerabilities
- Okta Acknowledges Breach
- Senate Bill Would Require Agencies to Update Outdated IT Systems
- Lapsus$ Arrests in UK
- Viasat Attack Collateral Damage
- Health-ISAC Current and Emerging Healthcare Cyber Threat Report
- Malicious npm Packages Removed from Registry
- FBI’s 2021 Internet Crime Report
- DoJ Charges Four Russian in Connection with Energy Sector Hacking
- CSIS Report: A Shared Responsibility: Public-Private Cooperation for Cybersecurity
- Microsoft Investigating Lapsus$ Hacking Claims
- President Biden’s Statement on National Cybersecurity
- TSA Pipeline Security Efforts are Faltering
- FBI AvosLocker Ransomware Advisory
- Ransomware Attack Shut Down Production at Bridgestone Subsidiary
- FIDO Alliance’s Vision for Passwordless Authentication
- NSA Cybersecurity Director: OpenSSL Vulnerability Can be Weaponized
- Nearly One-Third of Log4j Instances Still Not Patched
- Apple Outages Resolved
- Germany warns against Russian anti-virus use
- Exposing initial access broker with ties to Conti
- CISA, FBI warn of threats to U.S. satellite networks after Viasat cyberattack
- Ukraine arrests ‘hacker’ it says was routing calls for Russian troops
- ZAP-Hosting had 60GB of data breached
- City hall broken into using code ‘1234’
- Mask unlock is finally live on iPhone as iOS 15.4 arrives
- How California is building the nation’s first privacy police
- Lawmakers probe early release of top Russian hacker
- Ukrainian hackers say HackerOne blocked payments
- Facebook forgets how to security
- Firms must quickly report hacks to DHS in new law
- The deepfakes have arrived
- Microsoft Releases Scanner to Detect TrickBot-Infected Devices
- CISA, FBI: Hackers Exploited Misconfigured MFA
- Florida Medical Services Contractor to Pay Penalty for Misrepresenting its Cybersecurity Posture
- ICO Fines Law Firm Over Unsecured Legal Data
- Israeli Government Websites Affected by DDoS
- Linux Dirty Pipe Vulnerability Affects QNAP NAS Devices
- Internet Explorer 11 is Being Retired in June
- Cyclops Blink Now Targeting ASUS Routers
- European Union Aviation Safety Agency Warns Navigation Satellite Outages
- CISA, FBI Warning of Potential SATCOM Threats
- Azure Automation “AutoWarp” Flaw Fixed in Four Days
- US Legislators Pass Bill Requiring Critical Infrastructure to Report Cyberattacks and Ransomware Payments
- Cobalt Strike Spreading Through Phony AV Updates
- Intel Agencies Investigating Viasat Cyberattack
- GPS Disruptions Affecting Air Traffic in Parts of Finland
- Data Centre Security Guidance for Owners and Users
- Federal Register: US Federal Communications Commission Seeks Comments on BGP Security Issues
- CISA’s Cyber Storm VIII Exercise
- WordPress Update Released
- Healthcare Organization Breaches in Colorado and Alabama
- Secret U.S. surveillance program collects Americans’ money-transfer data
- Ransomware roundup: REvil, NetWalker ransomware members extradited to U.S.
- Ubisoft reveals “cyber security incident,” won’t say much
- Google blocks China-based phishing campaign targeting U.S. government
- NSA probes sabotage of satellite internet during Russian invasion
- Inside ‘Project Texas,’ TikTok’s answer To U.S. lawmakers’ China fears
- Inside Conti leaks: The Panama Papers of ransomware
- UPS flaws allow for remote code execution and remote fire-based interruptions
- Geofence warrants found unconstitutional in Virginia
- Twitter launches Tor onion service making it easier to access in Russia
- Google to acquire Mandiant for $5.4 billion
- Linux has been bitten by its most high-severity vulnerability in years
- Mitel devices abused for record-breaking DDoS amplification attack
- Mitel Collaboration Systems Exploited to Launch Amplified DDoS Attacks
- Russia Creates TLS Certificate Authority
- Securities and Exchange Commission Proposes Breach Disclosure Rule
- Access:7 Vulnerabilities
- Microsoft Patch Tuesday
- Qakbot is Hijacking eMail Threads
- CISA Updates Conti Warning
- Ransomware-Related Extraditions
- WordPress Security Whitepaper
- Cyberattack Irreparably Damaged SATCOM Terminals in Europe
- Cybersecurity Companies Offer Free Help to US Healthcare and Utilities
- Nvidia Code-Signing Certificates Stolen
- Samsung Galaxy Source Code Leaked
- NSA Publishes Network Infrastructure Security Guidance
- Linux Dirty Pipe Bug
- CISA Adds 95 Flaws to Known Exploited Vulnerabilities Catalog
- HSCC’s Model Contract Language for Medtech Cybersecurity
- Firefox Emergency Updates
- PressReader Outage
- Vulnerability: Patches for critical issues in Cisco video communications services
- Vulnerability: Security vulnerability in self-managed GitLab instances
- Vulnerability: Security bug affects campus access control system
- The APTs are Restless
- Azure’s Absolute Clanger
- Conti Members Doxxed but Undeterred, For Now
- Alexa’s Self-Abuse
- ICANN Says it Will Not Revoke Russian Domains
- Ukrainian Government Asks Tech Companies, Crypto Exchanges for Support
- Data Center Under Guard After SWIFT Excludes Russian Banks
- Senate Passes Bill Requiring Critical Infrastructure Operators to Report Cyberattacks, Ransomware Payments
- GAO: CISA’s National Critical Infrastructure Prioritization Plan Needs to Improve
- Palo Alto Networks Unit 42 Looks at Medical Infusion Pump Vulnerabilities
- CISA Medical Device Advisories for Vulnerabilities in BD Products
- Logan Health Breach Compromised Patient and Employee Data
- Nvidia Data Stolen
- Article: APIs increasingly used for account takeover
- Review: “Hacking APIs” by Corey Ball
- Guide: Using Postman for OAuth 2.0 authorization code grants
- Guide: Comprehensive guide to API documentation
- This is what they tell me cyberwar looks like.
- Meanwhile, Iran and China…
- The staggering ransomware wealth transfer.
- Remember Log4Shell?
- Must-see research projects.
- Hacking things.
- CISA and FBI Warning on HermeticWiper and WhisperGate
- SpaceX Starlink Satellite Service is Now Active in Ukraine
- Viasat Says European Broadband Outages Caused by Cyberattack
- Toyota Suspends Operations at Multiple Plants Following Supply Chain Cyberattack
- HHS Office for Civil Rights Director Tells Healthcare Providers to Strengthen Cyber Posture
- Zabbix Flaws Added to CISA’s Known Exploited Vulnerabilities Catalog
- FCC Notice of Inquiry Seeks Comments on Border Gateway Protocol Security
- CISA Warns of SCADA Flaws in Schneider Products
- Microsoft Says FoxBlade Malware Infected Ukrainian Networks
What you need to know about the new zero-day, Springshell
You may have seen news about a new remote code execution flaw that affects Spring, one of the most popular Java frameworks. This vulnerability, dubbed by some as “Springshell,” is a previously unknown security vulnerability, now confirmed by several security researchers, which is why we’re advising everyone to take immediate action to patch spring to the latest 5.3.18 or 5.2.20 versions.
While the situation is still unfolding, it has been compared to the ubiquitous Log4shell vulnerability, and is rightfully causing much anxiety. Because Spring is such an omnipresent software framework, we want to ensure you stay informed of the latest, and can respond appropriately:
- There are two vulnerabilities — one in Spring-Cloud released as CVE-2022-22963, that is high risk, contrary to its official ‘Medium’ rating, and another one affecting spring-beans that does not yet have a CVE.
- The critical RCE vulnerability (dubbed SpringShell) in Spring-Beans needs JDK9 or newer to be running, for the application to be packaged as a war and run using tomcat, which may limit how widespread exploitation could be.
- While sources have shared a SpringShell PoC its widespread impact to real-world applications is yet to be determined. Given the prominent nature of this vulnerability we’re being bullish on getting in front of this.
Read more in
- Spring Core on JDK9+ is vulnerable to remote code execution
- Spring Framework RCE, Early Announcement
- New Spring Framework RCE Vulnerability Confirmed – What to do?
FBI: Triton Malware is Being Used Against Energy Companies
The FBI has issued a TLP: White Private Industry Notification warning that Triton malware, also known as Trisis, is still a threat to critical infrastructure industrial control systems (ICS) around the world. The bulletin describes the threat, including the 2017 Triton attacks targeting a petrochemical company in the Middle East.
Note
- TRITON malware has been around since 2017. If you are responsible for securing Industrial Control Systems, this should not be news to you. However, the recommended best practices are not trivial to implement in these environments but hopefully you are making progress.
- The IC3 recommendations include using a one-way-link for receiving data from targeted systems such as the Schneider Electric Triconex safety instrumented system in addition to making sure they are properly isolated, security features enabled, and firmware/OS/applications kept updated. Leverage change management and logging to make sure things remain properly configured and any malicious activities are detected.
Read more in
- TRITON Malware Remains Threat to Global Critical Infrastructure Industrial Control Systems (ICS) (PDF)
- Triton Malware Still Targeting Energy Firms
- Feds Allege Destructive Russian Hackers Targeted US Refineries
- Feds allege destructive Russian hackers targeted US oil refineries
CISA Adds 66 Flaws to Known Exploited Vulnerabilities Catalog
The US Cybersecurity and Infrastructure Security Agency (CISA) has added 66 security issues to its Known Exploited Vulnerabilities catalog. Federal agencies have until April 18 to patch the vulnerabilities. The flaws’ disclosure dates range from 2005 to 2022.
Note
- You’re watching this catalog right? Just because a vulnerability is old, doesn’t mean the exploit doesn’t still exist or isn’t in use. Make sure that you’re not ignoring or accepting the risks of these in your environment. Remind management that these are being exploited, not just hypothetical weaknesses.
- This list is now up to 602 entries. These are vulnerabilities that you should have patched by now, but we understand vulnerability management is hard. This is another useful resource that helps your organization prioritize.
- CISA deserve a lot of kudos for this initiative. I recommend everyone response for cybersecurity in their organization to become familiar with the Known Exploited Vulnerabilities catalog and to implement it within their own vulnerability management program.
Read more in
- CISA Adds 66 Known Exploited Vulnerabilities to Catalog
- CISA: Here are 66 more security flaws actively being used by hackers – so get patching
- CISA adds 66 vulnerabilities to list of bugs exploited in attacks
Dept. Of Health and Human Services Office of Civil Rights Enforcement Actions
The US Department of Health and Human Services (HHS) Office for Civil Rights (OCR) has announced enforcement actions against four healthcare providers over possible violations of the Health Insurance Portability and Accountability Act (HIPAA). HHS OCR has reached settlements with organizations in Pennsylvania, North Carolina, California and Alabama. Two settlements involve potential violations of HIPAA’s right of access standard.
Note
- HHS OCR averaged over 740 corrective actions over 2017 – 2021, with on average 411 breach-related penalties and corrective actions. The three incidents noted here are kind of different – two were refusal by small practices to send patients their medical records and the other was a dentist responding to a bad online review by posting details of a patient’s treatment. If you work in a small medical practice, these are good items to use to show why access policies need to be in place and employees trained.
- Information protection is a balance between providing allowed access to information and protecting it, made more difficult by ever evolving regulations and increased system interconnection. If you’re not sure, contact your legal or other informed expert, the fine will exceed the cost of counsel. Use caution responding to negative feedback, particularly when delivering “the facts.” Compose what you really want to say, delete it, count to 100, re-compose, count again, and have a peer check it, then maybe post it. It’s easy to get drawn into an argument you cannot win, so skipping the response may be prudent.
Read more in
Sophos Patches Firewall Vulnerability
Sophos has released an update to address a critical authentication bypass vulnerability in its Firewall products. The flaw exists in the User Portal and Webadmin of the Sophos Firewall, and could be exploited to allow remote code execution.
Note
- This is the type of flaw that has often been compromised in the past to gain access to networks. An attacker controlling the firewall is not only able to disable it, but also able to intercept and redirect traffic passing through the firewall. Patch this flaw as soon as possible even if there is currently no publicly known exploit.
- It is interesting to note that the default configuration for the affected Sophos firewalls is to apply the patch automatically, but note that many updates require the system to be rebooted before it takes effect.
- Make sure that your Sophos firewall user portal and Webadmin interfaces are not Internet or WAN accessible. Next, apply the hotfixes and make sure that you’re on supported versions of the Sophos firewall. Verify boundary protection devices are at the top of your priority list for lifecycle replacement.
Read more in
- Resolved RCE in Sophos Firewall (CVE-2022-1040)
- Critical Sophos Security Bug Allows RCE on Firewalls
- Sophos patches critical remote code execution vulnerability in Firewall
- Sophos fixes critical hijack flaw in firewall offering
Windows Driver Blocker Added to Defender
Microsoft is adding a Vulnerable Driver Blocklist to Windows Defender on Windows 10, Windows 11, and Windows Server 2016 or newer. The blocklist will comprise information from Microsoft and from OEM partners.
Note
- Implementing this block list requires testing in audit mode first and then enabling the block to ensure devices don’t blue screen or get bricked.
- If you’re not allowing only approved drivers, this provides an opportunity to at least block known bad ones. Microsoft also recommends running devices in Hypervisor-protected code integrity (HVCI) devices or S mode. Test in audit mode before fully implementing this change to prevent malfunction/BSOD.
Read more in
- Microsoft is adding a new driver-blocklist feature to Windows Defender on Windows 10 and 11
- New Windows security option: Enable more aggressive blocklist which includes vulnerable drivers
- Microsoft recommended driver block rules
Chrome and Edge Updates Fix Flaw that is Being Actively Exploited
Google and Microsoft have updated Chrome and Edge, respectively, to address a high-severity zero-day vulnerability. The type-confusion flaw in the V8 JavaScript engine could be exploited to cause crashes and possibly lead to code execution. Users should update to Chrome version 99.0.4844.84 or newer; Microsoft has pushed out the Edge update.
Note
- Make it a habit to check your browser for update at least once a week, and restart the browser at least once a day. Restarting the browser will often trigger an update.
- CVE-2022-1096 is being actively exploited in the wild. Your IT staff may have pinged you over the weekend about this update pushed. Let them know now is a good time to do it. Don’t forget to update your chromium-based browsers as well.
Read more in
- Emergency Google Chrome update fixes zero-day used in attacks
- Google Chrome, Microsoft Edge patched in race against exploitation
- Chrome and Edge hit with V8 type confusion vulnerability with in-the-wild exploit
- Google Issues Urgent Chrome Update to Patch Actively Exploited Zero-Day Vulnerability
Ukrtelecom ISP Experienced Cyber Attack
Ukrainian ISP Ukrtelecom’s IT infrastructure was the victim of a “massive cyberattack.” The incident affected the entire country; connectivity levels were estimated to be 13 percent of pre-war levels. On Monday, March 28, the country’s State Service of Special Communication and Information Protection said that the attack had been neutralized.
Note
- The recovery plan included restoring service to priority customers, e.g. Ukraine’s Armed Forces and related military organizations, before private users or business-clients. Make sure that you’ve considered service restoration to priority customers vs everyone at once. As a customer, understand what key provider service restoration plans entail so you can plan accordingly.
Read more in
Replay Vulnerability Can be Exploited to Unlock and Start Honda Automobiles
Researchers have found a vulnerability that can be exploited through a replay attack to unlock and remotely start certain Honda and Acura vehicles made between 2016 and 2020. The attack captures radio frequency signals sent to the car from a key fob and replays them at a later time. The researchers recommend that the car manufacturers use “rolling” or “hopping” codes.
Note
- Much like a compromised reusable password, it will continue to work until changed. This is a bit different than password capture as the signal has to be captured over the air, so proximity matters. If you have a garage door opener with a static code, you have the same replay scenario, albeit the capture opportunity is different. Most late model vehicles do support non-static codes; verify this when purchasing. Double check your vehicles and other devices with wireless operation to determine your potential risks consider replacement where static codes are used.
- These replay and relay attacks are not new to cars or the industry. A HackRF One costs a little more than $300. Similar replay attacks for RFID are possible with a Proxmark. I am glad these vulnerabilities are getting more visibility.
Read more in
- Hackers remotely start, unlock Honda Civics with $300 tech
- Honda bug lets a hacker unlock and start your car via replay attack
Prison Sentence for Ransomware
A judge in Virginia has sentenced an Estonian man to five-and-a-half years in prison for his role in a series of ransomware attacks. Maksim Berezan was also involved in other cyber-related criminal activity.
Note
- The sentence of 66 months included an order to repay $36 million in restitution to his victims. His specialty was cash-outs and drops. Cash-outs use stolen credit cards to withdraw money or make fraudulent purchases while drops are a mechanism where money or goods are transferred to circumvent fraud detection by making the transactions hard to trace. This continues the trend where investigators are getting expert at discovery of crypto operations associated with malfeasance, reducing the viability of cryptocurrency payments.
Read more in
- Man linked to multi-million dollar ransomware attacks gets 66 months in prison for online fraud
- Estonian Tied to 13 Ransomware Attacks Gets 66 Months in Prison
- Cybercriminal Connected to Multimillion Dollar Ransomware Attacks Sentenced for Online Fraud Schemes
VMware Releases Fixes for Carbon Black App Control Vulnerabilities
VMware has released updates to fix two critical flaws in its Carbon Black App Control tool. The OS command injection vulnerability and the file upload issue could be exploited to execute arbitrary commands. Exploiting the flaws requires the attacker to be logged in with administrative privileges or as a highly privileged user.
Note
- While exploiting the flaw requires access with privileges, this is your application allow/deny list, and there are no workarounds, so you don’t want to miss addressing this flaw. The fix is to apply the corresponding patch for your currently installed App Control tool.
Read more in
- VMware Issues Patches for Critical Flaws Affecting Carbon Black App Control
- VMware fixes command injection, file upload flaws in Carbon Black security tool
- VMware Carbon Black App Control update addresses multiple vulnerabilities (CVE-2022-22951, CVE-2022-22952)
Okta Acknowledges Breach
Identity management and authentication provider Okta has acknowledged that some customer data has been breached, likely by the Lapsus$ group. According to a statement from Okta, the attack affected approximately 2.5 percent of its customers, which translates to 375 organizations.
Note
- Okta has been lacking transparency. Their hand was forced by Lapsus$ to admit a significant breach. As an IDAAS vendor, this should disqualify Okta from consideration for some customers who expect their identities to be managed and controlled by a vendor capable of detecting and responding to an incident.
- Valuable to note how Okta detected this: Okta “…detected an unsuccessful attempt to compromise the account of a customer support engineer working for a third-party provider.” As part of investigating that, Okta brought in a third party forensics firm to investigate and they found that a week before this event, for 5 days an attacker had access to a support engineer’s laptop. Doing that thorough investigation discovered the bigger problem.
- Lapsus$ trades in stolen credentials and leverages information about team structures, users, help desks, incident response workflow and possible supply chain trust to target victims. Be on the look for unexpected account lockout, users with added privileges, or new users with full administration rights in your cloud accounts. As they also tap into internal communications, make sure that you have out-of-band protected communication channels for incident response.
Read more in
- Updated Okta Statement on LAPSUS$
- Okta now says: Lapsus$ may in fact have accessed customer info
- The Third-Party Okta Hack Leaves Customers Scrambling
- Okta Says 366 Customers Impacted via Third-Party Breach
- Authentication Giant Okta Breached Through Customer Support
Senate Bill Would Require Agencies to Update Outdated IT Systems
Legislation introduced in the US Senate would make federal agencies identify and replace outdated IT systems and to create modernization plans. The Legacy IT Reduction Act would also direct the Office of Management and Budget to create guidance for the agencies.
Note
- First, the cynical comment: I think there has been some form of “Modernizing Government Technology Act of 20XX” every year or two since X=0. More importantly, as evidenced by yearly GAO reports, the US Government has major problems patching, maintaining and securely administering the modern technology they are already using. Doing the wrong things on shiny, new hardware can only be marginally more secure than doing the wrong things on dusty, old hardware.
- Affected agencies will have to submit modernization plans within two years and every five years thereafter. Expect those plans to be part of your annual assessments. Irrespective of legislative requirement, or funding, you need lifecycle plans for not just hardware and operating systems, but also for applications. Keeping those updated and modernized will put you at odds with your business system owners who value stability and meeting milestones over security and business process modernization. That may be the time to discuss outsourcing or moving to a cloud service which is engineered for both stability and updates. Note that government systems, e.g., government financials, cost modeling, are different from private sector systems, so make sure your provider has demonstrated success in these domains. Where you still have legacy systems, ICS/OT being the easiest examples, make sure that you are both protecting them from your environment and vice versa.
Read more in
- Senate bill would push replacement of legacy IT systems
- Sens. Hassan, Cornyn Want Planning for Fed ‘Legacy’ IT Replacement
Lapsus$ Arrests in UK
Authorities in the UK have arrested seven people in connection with the Lapsus$ cyberattack group that has targeted Okta, Microsoft, and others. All the individuals, who are between the ages of 16 and 21, were detained and released under investigation.
Note
- Techniques used by Lapsus$ in some of their attacks, like SIM swapping and bribing insiders, are used by other actors as well. Do not discount this as a “group of teenagers.” Sophisticated attackers use the same techniques and are less likely to get caught. Lapsus$ got caught because they didn’t try to hide their exploits. Sophisticated expensive security stacks had little to contribute after Lapsus$ notified their victims and made data public.
- The alleged leader appears to have amassed about $14m in bitcoin from his exploits so far. It would be nice to channel that level of ingenuity and leadership for a successful, legal, business venture. The arrest may be, in part, due to the 16-year-old leader having a falling out with his cohorts resulting in him getting “doxxed.” One hopes he learned from that experience.
Read more in
- Alleged Microsoft, Okta hackers arrested in UK
- Researchers Trace LAPSUS$ Cyber Attacks to 16-Year-Old Hacker from England
- British cops arrest seven in Lapsus$ crime gang probe
Viasat Attack Collateral Damage
One month after a cyberattack against Viasat, there are still disruptions. The attack was not against the satellite itself, but affected fixed broadband customers; it bricked modems across Europe and knocked German wind turbines offline. The attack is being investigated by US and European intelligence agencies.
Note
- Satellite communication is really attractive in areas where other communication options are not available or reliable. This also makes contingency planning complex. When planning connectivity in that situation be sure to consider and document what the fail-over options are and what they involve including lead time and mission impact.
Read more in
Health-ISAC Current and Emerging Healthcare Cyber Threat Report
The Health Information Sharing and Analysis center (Health-ISAC) has published its first annual Current and Emerging Healthcare Cyber Threat Landscape report. The document includes results of a survey of healthcare sector executives; cyber threat intelligence analysis; and 2022 operational technology and supply chain projections.
Note
- Not really anything useful in the publicly available executive summary, but Health-ISAC members can download the full report. The report seems to be saying Healthcare should spend at the levels of Finance in cybersecurity, which is not likely. Plus, the IT architectures and more importantly IT governance is vastly different in healthcare – more like retail than banking.
- The executive summary is a good read, you have to be a member of the Health-ISAC to get the full report. The issues of service delivery, exposing more functions to customers, rapid change to remain viable during the pandemic and software supply chain attacks (SolarWinds, Kaseya, Log4J, etc.) are not industry specific. The mitigations and recommendations are applicable across the board.
Read more in
- Health-ISAC’s First Annual Current and Emerging Healthcare Cyber Threat Landscape Executive Summary
- H-ISAC calls for ‘intelligence-led’ security, as actors continue to target healthcare
Malicious npm Packages Removed from Registry
Researchers from JFrog Security found more than 200 malicious npm packages that were targeting Microsoft Azure developers. The packages were designed to steal personally identifiable information. The malicious packages have been removed from the npm registry, but not before they had been downloaded an estimated 50 times.
Note
- Beware of guest packages bearing “gifts.” The fake packages had similar names but with different scope from the legitimate ones and much higher version numbers to appear to be legitimate updates, e.g., @azure/core-tracing vs core-tracing. Be sure to scope the packages fully and make sure that you’re loading the versions you have qualified.
Read more in
- Large-scale npm attack targets Azure developers with malicious packages
- Malicious npm packages target Azure developers to steal personal data
- Microsoft Azure Developers Awash in PII-Stealing npm Packages
- Over 200 Malicious NPM Packages Caught Targeting Azure Developers
- Microsoft Azure developers targeted by 200-plus data-stealing npm packages
FBI’s 2021 Internet Crime Report
According to the FBI’s 2021 Internet Crime Report, nearly 650 critical infrastructure organizations were hit with ransomware in 2021. The actual figures are likely higher, as the FBI did not start tracking ransomware attacks specifically against critical infrastructure organizations until June 2021. Of the critical infrastructure sectors, healthcare topped the list in reported ransomware attacks. The report noted an overall seven percent increase in “complaints of suspected Internet crime.”
Note
- The report also gives an overview of what IC3 does as well as how they are responding to top incidents reported. This is a good time to make sure you’ve included IC3 reporting in your incident response plan, to include contacts in your local FBI office, in case you need these services in the future. The report also gives some context on recovery and how these crimes are interrelated.
- Much of the report is given over to explicating IC3’s role and accomplishments. While the findings, (for example, $6.9 billion victim losses in 2021, 2,300+ average complaints received daily, 552,000+ average complaints received per year (last 5 years), over $6.5 million is complaints reported since inception) are not surprising, they carry authority and weight, and demonstrate both the vulnerability and the threat. Note that $6.9 billion in losses would buy a lot of prevention.
Read more in
- Internet Crime Report 2021 (PDF)
- FBI: Ransomware hit 649 critical infrastructure orgs in 2021
- FBI: Cybercrime Victims Suffered Losses of Over $6.9B in 2021
- FBI IC3: Healthcare Sector Faced Most Ransomware Attacks Last Year
DoJ Charges Four Russian in Connection with Energy Sector Hacking
The US Department of Justice (DoJ) recently unsealed two indictments charging four Russian citizens “with attempting, supporting and conducting computer intrusions that together, in two separate conspiracies, targeted the global energy sector between 2012 and 2018.” The defendants allegedly targeted energy-related organizations in more than 130 countries.
Note
- These indictments are not so much about getting the culprits arrested and convicted. But they are very useful as they are providing some insight into the techniques used by these attackers. And remember that these techniques tend to trickle down to less sophisticated attackers.
- Extradition restrictions in Russia will likely prevent them from ever coming to trial. Nevertheless, their actions reinforce the need to make sure your systems are appropriately secure. Don’t ignore low-hanging fruit like not allowing RDP from the Internet, judicious application of patches and updates and implementing MFA for all Internet accessible services. Finished that list? Now have some of the hard conversations about lifecycle replacement. Not just of boundary protections, but also endpoint, monitoring and incident response systems. Don’t forget there are many services available to help, both free (ISAC, FBI, CISA) and paid (MSP, etc.) you can leverage.
Read more in
- Four Russian Government Employees Charged in Two Historical Hacking Campaigns Targeting Critical Infrastructure Worldwide
- Feds Allege Destructive Russian Hackers Targeted US Refineries
- U.S. charges 4 Russian government workers with hacking energy sector
- US charges four Russians over hacking campaign on energy sector
The Center for Strategic and International Studies (CSIS) has published a report based on “two private roundtables with senior government officials and senior information security executives from major enterprises in a range of U.S. industry sectors. The goals of the roundtables were to identify common challenges, discuss best practices, and outline avenues for cooperation.”
Note
- Another point noted is the need to prioritize security efforts. “Patch all the things (now)” isn’t really viable. Identify key assets, know where sensitive information is, and make sure those are well secured. Make sure that security of outsourced or cloud-based services remains appropriate, remember to do those reviews and audits you added to the contract provisions. Keep leveraging the resources available from the government services to help you knock this out of the park.
Read more in
- A Shared Responsibility | Public-Private Cooperation for Cybersecurity (PDF)
- A Shared Responsibility: Public-Private Cooperation for Cybersecurity
- Federal government earns high marks for cyber collaboration, but gaps remain
Microsoft Investigating Lapsus$ Hacking Claims
Microsoft is investigating claims made by the Lapsus$ hacking group that it has compromised Azure DevOps source code repositories. Lapsus$ has previously stolen data from Nvidia, Samsung, Ubisoft, and others. Rather than infecting its targets with malware, Lapsus$ infiltrates networks, steals sensitive data, and attempts to exact ransom payments from its victims.
Note
- The Lapsus$ group has breached a number of other high profile targets. The claims should be taken seriously. Today, they also announced a breach of a company associated with Octa and they claimed to be going after Octa customers. Exposed RDP servers are one way how Lapsus$ is assumed to breach its targets. The goal is typically extortion.
- While you cannot be certain of being or not being a target of the Lapsus$ group, you can make sure that your cyber hygiene is up to par. Make sure that you’re following best practices for your source code repositories, particularly any which are externally stored. Make sure you are only enabling the minimum access needed, that authorization/API or other security keys are NOT stored there. If you remove them, make sure they are rotated so that any downloaded or archived copies are not viable. MFA all externally accessible services, make sure there are no undocumented exceptions; keep those to the minimum possible.
Read more in
- Microsoft investigating claims of hacked source code repositories
- Microsoft investigating hacking group’s claims of successful breach
- Microsoft Investigating Claim of Breach by Extortion Gang
- Microsoft investigates after Lapsus$ gang brags of Bing, Cortana code heist
President Biden’s Statement on National Cybersecurity
President Joe Biden issued a statement “reiterating [earlier] warnings based on evolving intelligence that the Russian Government is exploring options for potential cyberattacks.” The president urged private sector organizations to harden their cyber defenses. The government is providing resources and tools through CISA’s Shields-Up campaign and lists steps for organizations to take in the fact sheet below.
Note
- The warning is vague, but it links to some of the guidance CISA has been publishing. At this point, it is likely too late to fix your security program. Instead, check the list of CISA suggestions for any gaps. The announcement has been covered in many non-tech news outlets and management is likely going to ask if you are “ready.” It may be good to have a brief slide deck ready explaining where you stand (and good opportunity to get buy-in for things like MFA or whatever is missing). But please avoid “busy work.” Make sure not to overload your team with work at a time when they probably should rest a bit to get ready for the big event, should it happen.
- The CISA has been publishing guidance on cyber hygiene you can leverage. They also offer services to help with scanning, analysis, or tool recommendations. Review their guidance, perform a gap analysis, then go get funding and resources for priority items such as MFA, modern endpoint and boundary protection services. Remember to make sure your SOC is equipped with the tools, including staff; they need to monitor and respond to incidents.
Read more in
- Statement by President Biden on our Nation’s Cybersecurity
- FACT SHEET: Act Now to Protect Against Potential Cyberattacks
- Russia Is Exploring Cyberattack Options, Tells US to Harden Networks
- White House warns Russia prepping possible cyberattacks against US
TSA Pipeline Security Efforts are Faltering
Owners and operators of US pipelines say that the Transportation Security Administration’s (TSA’s) cybersecurity rules are (cumbersome and confusing and could put pipeline safety and supply at risk. Many of TSA’s pipeline cybersecurity requirements are more appropriate for personal computers than for operational technology.
Note
- It’s easy to forget the TSA’s scope includes mass transit systems, ports, and pipelines. The lesson here is to make sure that regulations, policies etc. at any level, are relevant. While the requirements from TSA don’t necessarily apply to ICS, the goals of security awareness, strong authentication, segmentation, allowing only authorized devices and users access to these systems are appropriate. Supporting IT systems need to be up-to-snuff as well, leveraging endpoint protection, patching, and MFA where appropriate. With revisions the guidelines will make a better fit; in the interim, review them for what you can use, and document what is inappropriate to moderate regulators looking for you to follow the “letter of the law.”
- Drafting regulation is difficult. TSA came late to this aspect of their responsibility. Whether or not TSA had the necessary knowledge, skills, abilities, and experience to regulate this aspect of its responsibility has been in question. They should seek the assistance of CISA and NIST to raise the security of the pipeline industry to an appropriate level.
Read more in
FBI AvosLocker Ransomware Advisory
In a joint cybersecurity advisory, the FBI, the US Treasury Department, and the Financial Crimes Enforcement Network warn that the “AvosLocker … Ransomware as a Service (RaaS) affiliate-based group … has targeted victims across multiple critical infrastructure sectors in the United States including, but not limited to, the Financial Services, Critical Manufacturing, and Government Facilities sectors.” The advisory includes technical details, indicators of compromise, suggested mitigations, and other resources.
Note
- This group typically exploits Exchange Server vulnerabilities as entry points. If you cannot migrate off on-premises Exchange servers, adopt an aggressive patching and vulnerability management posture. The AvosLocker RaaS group handles details such as ransom negotiation, publishing leaked data on their site, guiding victims to the payment sites, and will accept either Monero or Bitcoin (for a 10-25% fee). This shields affiliates from direct communication with the victims. Use the IoCs from IC3 to scan for activities.
Read more in
- FBI warning: This ransomware uses DDoS to threaten victims. Here’s what to watch out for
- AvosLocker group is targeting US critical infrastructure, FBI says
- FBI: Avoslocker ransomware targets US critical infrastructure
- Indicators of Compromise Associated with AvosLocker Ransomware (PDF)
Ransomware Attack Shut Down Production at Bridgestone Subsidiary
Bridgestone has acknowledged that a subsidiary was the victim of a ransomware attack in February. The incident caused Bridgestone Americas to shut down its computer network and production for a week. Bridgestone is a supplier for Toyota; a different Toyota supplier experienced a ransomware attack shortly after the Bridgestone attack.
Note
- Now that we’re emerging from challenges getting chips for modern vehicle electronics, we can’t get the tires to drive them. Fortunately, as a consumer you can buy tires from alternate manufacturers; it’s a bit harder for a factory to ask for a quick shipment of thousands of tires. When looking at alternate suppliers for your contingency plan, be sure to include how long it’s going to take to get a replacement order and if that disruption is tolerable. Stockpiling may not be the optimal answer; consider downsides.
Read more in
- Ransomware Attack Led Bridgestone to Halt US Tire Production for a Week
- Bridgestone Hit as Ransomware Torches Toyota Supply Chain
FIDO Alliance’s Vision for Passwordless Authentication
The FIDO (Fast Identity Online) Alliance has published a whitepaper describing what it believes are solutions to issues that have prevented passwordless authentication from being widely adopted. FIDO Alliance executive director Andrew Shikiar stated that “Not using a password should be easier than using a password.”
Note
- Fraudulent reuse of passwords continues to be a frequent method of compromise. A preference for convenience is used as a justification for the continued use of passwords. One test of good design is that it makes it easier to do the right thing than the wrong thing. Cheap, powerful, portable clients make it possible to implement strong authentication without the use of passwords by the individual. Such implementation is urgent.
Read more in
- FIDO Alliance says it has finally killed the password
- A Big Bet to Kill the Password for Good
- FIDO Alliance White Paper: Choosing FIDO Authenticators for Enterprise Use Cases (PDF)
NSA Cybersecurity Director: OpenSSL Vulnerability Can be Weaponized
NSA Cybersecurity Director Rob Joyce is urging organizations to patch a high-severity vulnerability in OpenSSL. Joyce tweeted, “With the current state of internet threats, recommend patching CVE-2022-0778 immediately. This flaw enables a pre-authentication DOS attack on OpenSSL. I know it is “only” rated a 7.5 CVE, but definitely can be weaponized.”
Note
- Yes, the vulnerability can be weaponized for a DoS attack. But is this your #1 priority right now? Apply patches as they become available. Don’t get distracted by “squirrels” but stick to your vulnerability management protocol on this one. Updated packages are available for various Linux distributions that should be straightforward to apply.
- The patch was released on March 15th; apply it when it is available. If you’re still on OpenSSL 1.0.2 – it’s time to go to 1.1.1n or higher. The flaw is triggered by elliptic curve keys where the explicit curve parameters are invalid.
Read more in
- OpenSSL Security Advisory [15 March 2022] Infinite loop in BN_mod_sqrt() reachable when parsing certificates (CVE-2022-0778)
- CVE-2022-0778 Detail
- Rob Joyce @NSA_CSDirector
- OpenSSL vulnerability can ‘definitely be weaponized,’ NSA cyber director says
Nearly One-Third of Log4j Instances Still Not Patched
Researchers from Qualys found that 30 percent of Log4j instances remain unpatched, more than three months after the vulnerability was first disclosed. Within 72 hours of its initial disclosure, there were nearly one million attempts to exploit the flaw.
Note
- No surprise here. This isn’t an “easy” vulnerability to patch and it usually doesn’t patch “itself” via more or less automatic operating system updates. While log4j is no longer at the top of the list of vulnerabilities attackers scan for, it now has entered the dangerous zone of exploits that are more used in targeted attacks and less in widespread scans by bots.
- The low-hanging fruit is patched at this point; many are waiting for updates from vendors. For Internet-facing applications, make sure that your WAF is configured to handle attempted Log4J exploits. Make sure you’re actively monitoring for attempted exploits and your response plan is known. Track internally discovered Log4J instances to make sure they are addressed as software is either updated or retired. Watch for orphaned systems no longer getting automatic updates.
Read more in
- Qualys Study Reveals How Enterprises Responded to Log4Shell
- 30% of Log4j instances still remain vulnerable, with open source apps a major hurdle
Apple Outages Resolved
Apple has resolved issued that caused outages of multiple cloud-based services on Monday, March 21. The incident affected the App Store, Apple Music, iCloud Mail, Maps, and iMessage. The services were reportedly restored by 3:45pm ET.
Note
- There is no such thing as too big (or too small) to fail. Given the scope of the outage, Apple was back on its feet relatively quickly. How fast could you recover if you got hit hard? When thinking of fall-back practices, such as hand-written sales receipts, include processes for entering and reconciling them into systems once recovered, making sure resources are identified and know how to do that. Think about how you would communicate internally and externally. Then test those assumptions.
Read more in
- Apple Maps, App Store, other Apple services experience outage
- Apple has resolved the outage affecting iMessage, Apple Music, the App Store, and other services
- System Status
Germany warns against Russian anti-virus use
Germany’s cybersecurity office is warning organizations across the country against using software made by Kaspersky, a Russian-headquartered antivirus giant. Germany’s BSI said (in German) that Kaspersky’s antivirus, which to function relies on deep access to its host operating system, could be forced to spy or launch cyberattacks at the request of the Russian government in the wake of the Ukrainian war. Kaspersky said the decision was a “made on political grounds.” @hatr, a reporter in Germany, explains more in a tweet thread. The U.S. banned Kaspersky in 2019 citing fears that the firm could be used to spy by Russia.
Read more in
Exposing initial access broker with ties to Conti
Conti hobbles on, seemingly undeterred by a slew of leaks into its own operations, as new victims come to light. Google’s Threat Analysis Group dropped new details on an initial access broker (IAB) with ties to the Conti ransomware group. The IAB, dubbed “Exotic Lily,” breaks into networks and hands off access to the highest bidder. Cyberscoop breaks down some of the details well. It comes as more leaked details about Conti come to light. The Washington Post ($) has 11 interesting takeaways.
Read more in
- Leaked Ransomware Docs Show Conti Helping Putin From the Shadows
- Google discovers threat actor working as an ‘initial access broker’ for Conti ransomware hackers
CISA, FBI warn of threats to U.S. satellite networks after Viasat cyberattack
CISA and the FBI are warning of possible threats to satellite communications (or SATCOM), after the Viasat cyberattack saw thousands of users across Europe and Ukraine without internet access. The outage happened at the time of the Russian invasion of Ukraine, and was a “really huge loss in communications in the very beginning of the war,” per Ukrainian cyber official Victor Zhora (via @Bing_Chris). (The Ukrainian military is a big user of satellite communications.) The Viasat hack also knocked out access to turbines across Germany, reports said. CISA warns that U.S. users could also face similar cyberattacks. SATCOMs are used across the U.S. media, government and military, and energy sectors.
Read more in
- Strengthening Cybersecurity of SATCOM Network Providers and Customers
- CISA and FBI warn of possible threats to satellite communications networks
Ukraine arrests ‘hacker’ it says was routing calls for Russian troops
Interesting developments in the electronic warfare side of the Ukraine war this week: Ukraine’s security service detained a “hacker” who was helping Russian troops by routing calls on their behalf by leveraging Ukrainian phone networks that are blocking Russian and Belarusian numbers after forces crossed into its territory. @mcdaidc has an interesting tweet thread on the SIM box used in this story. Meanwhile, the maintainer of node-ipc, an open source project downloaded over a million times a week, sabotaged the code to wipe computers that are in Russia and Belarus. The so-called “protestware” was marked as CVE-2022-23812. @josephfcox explains more in another story for Motherboard.
Read more in
- Pro-Ukraine ‘Protestware’ Pushes Antiwar Ads, Geo-Targeted Malware
- CVE-2022-23812 | RIAEvangelist/node-ipc is malware / protest-ware
- Sabotage: Code added to popular NPM package wiped files in Russia and Belarus
ZAP-Hosting had 60GB of data breached
Germany-based ZAP-Hosting has confirmed a security breach and has shut down part of its infrastructure. Payment data and passwords were encrypted, the company said in a tweet thread. Have I Been Pwned got wind of the data; it amounts to about 60GB of data, including names, phone numbers, chat logs, email addresses, etc. — just the regular personal information you probably wouldn’t want out there.
City hall broken into using code ‘1234’
A woman allegedly broke into Newport City Hall on Monday, using the code “1234” to gain access before damaging the building and contents, reports the Oregonian newspaper. “A large potted plant had been thrown to the floor.” Absolute carnage. The city manager claimed the access code was programmed temporarily for a contractor. (Yeah, but for how long are we talking about here?)
Mask unlock is finally live on iPhone as iOS 15.4 arrives
Finally. With iOS 15.4, now you can unlock your phone while wearing your mask using Face ID on newer iPhones. Face ID lets you unlock your iPhone with your face — which when covered with a mask isn’t so easy. It only took Apple two years… @JoannaStern also has a run-down of how the feature works. (It’s far from perfect!)
How California is building the nation’s first privacy police
Here’s a profile of Ashkan Soltani, a former researcher and chief technologist at the FTC, who now “faces the daunting task of overseeing the first government body in the United States with the sole job of regulating how Google, Facebook, Amazon and other companies collect and use data from millions of people.” Soltani is the first head of the California Privacy Protection Agency, which will enforce the state’s privacy law, one of the strictest in the country.
Lawmakers probe early release of top Russian hacker
Here’s the curious case of Russian cybercriminal Aleksei Burkov, who after being extradited to the U.S. and jailed for nine years was curiously released just a year into his sentence. The big question is why, and lawmakers want to know. Burkov was once one of Russia’s most elusive hackers, and was for a time a pawn in a diplomatic spat that saw him floated for a potential prisoner exchange. Much of his court docket is sealed. Where did his sentence go?
Ukrainian hackers say HackerOne blocked payments
Ukrainian hackers and security researchers said HackerOne was withholding bug bounty rewards, citing U.S. sanctions against Russia and Belarus, but which don’t affect Ukrainians. Hackers said they were unable to withdraw in some cases thousands of dollars in earnings. HackerOne CEO’s tweets (which he later deleted and recast) and support staff added to the confusion, but HackerOne said it would resolve the situation “within the week.” (Disclosure: I wrote this story.) Turns out companies don’t know sanctions work. Thankfully we have some solid analysis from @k8em0 on the bug bounty front.
Facebook forgets how to security
Last year Facebook said it would mandate that some high risk accounts use two-factor authentication and that they would be locked out of their accounts if they didn’t. It was an ultimatum at the time. But Facebook flubbed the process completely, sending users emails from non-Facebook.com domains, which many thought was spam (and ignored — you know, that thing people are supposed to do!). Behold, this week rolls around and a lot of people are understandably pissed at being locked out of their accounts.
Firms must quickly report hacks to DHS in new law
A new $1.5 trillion funding package signed into law this week by President Biden includes a provision that mandates critical infrastructure operators to notify Homeland Security of data breaches within 72 hours of discovery, or any ransomware payments within 24 hours, reports Bloomberg. The aim is to help officials get better insights into global hacking events. But the FBI isn’t happy that DHS gets the first cut of the data, even though CISA boss @CISAJen said the DHS would “immediately” share the goods.
The deepfakes have arrived
A Ukrainian TV outlet claimed its live broadcast and website were hacked with a chyron falsely claiming the country had surrendered, according to Motherboard. At the same time, a deepfake of Ukrainian president Zelenskyy appeared this week of him apparently surrendering (he didn’t, he’s long said he would not surrender to Russia). No one has claimed responsibility for the alleged hack or the fake video, but it’s looking like deepfakes are now part of the information war. This week also saw U.K. defense secretary Ben Wallace and home affairs secretary Priti Patel apparently targeted by “imposter” video calls who managed to get through to Wallace via “another government department.” Per the BBC, the video call was “fairly sophisticated” that was not made to Wallace’s own mobile phone. Deepfakes are going to pose a considerable security risk when they inevitably start to work.
Microsoft Releases Scanner to Detect TrickBot-Infected Devices
In a blog post, the Microsoft Defender for IoT research team shares its analysis of how MikroTik devices are used in TrickBot’s command and control framework. Microsoft has published a tool that can be used to detect MikroTik Internet-of-Things (IoT) devices that are infected with TrickBot.
Note
- Great work by Microsoft. But a bit sad that this didn’t come from MikroTik. Like many similar devices, MikroTik routers had their share of vulnerabilities (or just simple misconfigurations) in the past. But vendors need to step up and provide users with tools to avoid and detect configuration errors and compromise. This could start with a simple standardized API to request firmware versions for easier vulnerability scanning (and an API to find the most recent version easily). Currently, scripts to accomplish this often have to scrape data from ever changing webpages. (Prove me wrong and let me know of vendors doing this well.)
- It still blows my mind when looking at all the cool cyber research Microsoft is publishing, to include free tools for prevention and detection. If you have any MikroTik devices you need to read this. Essentially the TrickBot malware is using the routers as a proxy on a non-standard port to access their C2 servers. Then adds a persistence layer which obfuscates malicious IPs to avoid many detection systems. Make sure that you have changed default passwords on your MikroTik devices, use good passphrases – ideally checked against data breaches and keep the firmware updated. Only allow management from authorized systems making sure you restrict access to port 8291 and 22. Grab the forensic tool and cross-check your devices for any areas of concern.
Read more in
- Uncovering Trickbot’s use of IoT devices in command-and-control infrastructure
- Microsoft: Here’s how this notorious botnet used hacked routers for stealthy communication
- Trickbot is using MikroTik routers to ply its trade. Now we know why
- Microsoft creates tool to scan MikroTik routers for TrickBot infections
- Has Trickbot gang hijacked your router? This scanner may have an answer
CISA, FBI: Hackers Exploited Misconfigured MFA
In a joint cybersecurity advisory, the FBI and the Cybersecurity and Infrastructure Security Agency (CISA) “warn … that Russian state-sponsored cyber actors have gained network access through exploitation of default MFA protocols and a known vulnerability.”
Note
- This issue is getting to some of the core challenges of MFA: How to deal with lost/expired tokens efficiently.
- Headlines are making this sound like MFA has been hacked and is no longer reliable, which is NOT the case; it’s something much more boring: MFA mis-configuration. The cyber attackers were able to gain control of a forgotten account via simple password brute forcing. This account had been ‘expired’ from the MFA server, but was still able to re-enroll. Once the attackers re-enrolled and gained access to the internal environment, they disabled the domain controllers MFA configuration by pointing to itself (localhost) which caused MFA authentication to fail. Unfortunately, it was configured for ‘fail-open’ mode which means if MFA is not working, users can gain access with just their password. Is MFA still a viable and recommend method for protecting accounts, absolutely. Are there steps we can do on the server end to lock it down even more? It appears so. The CISA write-up has the best technical details of the attack.
- Does your MFA fail open or closed? MFA which fails open is being discovered and exploited. Sometimes old accounts are identified which haven’t been converted to MFA, so a password attack works, or somehow are trivially reactivated. Make sure that your MFA is comprehensive, fully disable inactive accounts – removing them is best, make sure all components are patched to mitigate risks on all the components involved in MFA. If you have emergency/”break glass” accounts monitor them closely; it is very tempting to for system administers to use these instead of the MFA “everyone else” has to use. Make sure their credentials are strong and changed after each authorized use. Don’t allow for non-MFA accounts for special/VIP users.
- Another good report from FBI and CISA. This one maps to ATT&CK and provides some TTPs that you should be able to easily detect regardless of what vulnerability or misconfiguration is exploited. As we say in SEC504, prevention is a goal, detection and response are the reality.
Read more in
- Alert (AA22-074A) Russian State-Sponsored Cyber Actors Gain Network Access by Exploiting Default Multifactor Authentication Protocols and “PrintNightmare” Vulnerability
- CISA and FBI warning: Hackers used these tricks to dodge multi-factor authentication and steal email from NGO
- Russia State-Sponsored Hackers Used Misconfigured MFA to Breach NGO
Florida Medical Services Contractor to Pay Penalty for Misrepresenting its Cybersecurity Posture
Florida-based Comprehensive Health Services (CHS) will pay $930,000 to settle allegations that it violated the False Claims Act. CHS falsely represented its electronic medical record cybersecurity compliance to the US State Department and Air Force. The DoJ press release notes that “This is the Department of Justice’s first resolution of a False Claims Act case involving cyber fraud since the launch of the department’s Civil Cyber-Fraud Initiative.”
Note
- If you are a contractor or supplier to the US federal government, or a federal grant recipient, this is an important item to show to Chief Legal Counsel and management. The False Claims Act is a long-used mechanism to fine offenders for misuse of government funds. This case is the first of the 2021 Civil Cyber Fraud Initiative being applied to instances where companies did not disclose incidents or known high risk issues while accepting government funding – there will be more. The message is “much less expensive to follow regulations for disclosure than try to hide incidents, lowest cost is to avoid incidents in the first place.”
- While this case is specific to medical/health industry activities, it foreshadows the expectations of federal government contractors. Make sure that your licensing and knowledge of regulatory requirements is up to current requirements, to include NIST, CMMC and incident reporting requirements. Use this incident to reinforce support meeting and ongoing monitoring of these requirements.
Read more in
- DOJ Settles First Case Under Civil Cyber-Fraud Initiative
- Medical Services Contractor Pays $930,000 to Settle False Claims Act Allegations Relating to Medical Services Contracts at State Department and Air Force Facilities in Iraq and Afghanistan
ICO Fines Law Firm Over Unsecured Legal Data
The UK’s Information Commissioner’s Office (ICO) has fined a London criminal defense law firm for failing to protect information about legal cases; the data were stolen in a 2020 ransomware attack. Tuckers Solicitors has been fined £98,000 for violating the General Data Protection Regulation. While a fix for the vulnerability was made available in January 2020, Tuckers did not apply the patch until June 2020.
Note
- While the exploit wasn’t discovered until August of 2020, it’s believed the attack happened during the five months the vulnerability was unpatched. Make sure that you are prioritizing application of updates with high CVSS scores, 9.8 in this case. This is even more critical as many services now have customer facing interfaces allowing for potential exploitation or abuse. Remind management reluctant to incur downtime or complete regression testing that with the GDPR and other privacy legislation such as the CCPA, there are real fines at stake which can quickly offset any costs associated with staying secure.
Read more in
Israeli Government Websites Affected by DDoS
Israel’s National Cyber Directorate has acknowledged that a massive distributed denial-of-service (DDoS) attack hit communications service providers and caused numerous government websites to be unavailable. The sites are now operating as usual.
Note
- Adversaries shooting bullets ‘over the fences’ has been replaced with cyber-attacks, and DDoS seems to be a favorite lately, not only as a mission disruptor, but also to disguise other activities such as a ransomware attack. DDoS protection, particularly in the public sector, needs to be added to the SOP list. Talk to your ISP, CDN and cloud service providers to not only ensure available DDoS protections are enabled, but also to determine what they are to see if they are sufficient or if you need to seek added protections.
Read more in
- Huge DDoS attack temporarily kicks Israeli government sites offline
- DDoS Attack Downs Several Israeli Government Websites
Linux Dirty Pipe Vulnerability Affects QNAP NAS Devices
The Dirty Pipe Linux vulnerability affects QNAP network attached storage (NAS) devices running QTS 5.0.x and QuTS hero h5.0.x. The flaw does not affect QNAP NAS devices running QTS 4.x. There are currently no mitigations for the issue.
Note
- This vulnerability affects all devices based on Linux, not just QNAP. QNAP was just nice enough to release a patch and point out that they are vulnerable.
- Linux privilege escalation vulnerabilities, like Dirty Pipe, tend to affect many products and solutions and stick around for a very long time.
- You already know what I’m going to say – so say it along with me “I solemnly swear I won’t expose NAS devices to the Internet.” Do keep your NAS devices patched, monitor for unauthorized accounts or applications, change default credentials, use another option for sharing content externally. Cloud based file sharing is not all that expensive, particularly when compared to recovery of your compromised content.
Read more in
- Most QNAP NAS Devices Affected by ‘Dirty Pipe’ Linux Flaw
- Local Privilege Escalation Vulnerability in Linux (Dirty Pipe)
Internet Explorer 11 is Being Retired in June
Microsoft is reminding users that it will be retiring Internet Explorer 11 (IE 11) in June. Microsoft will replace the browser with Edge. Legacy IE-based websites and applications will be supported with Edge’s IE mode feature.
Note
- While this may sound easy to drop for consumers, large organizations continue to be dependent on IE because of legacy applications. We have known about this retirement for a long time, I hope organizations were able to migrate applications and can move to current web browsers.
- If you’ve not been pushing out and testing Chromium Edge you really need to get moving. Chromium Edge does include an IE mode for IE dependent applications you can toggle the “Allow sites to be reloaded in Internet Explorer” At this point you may not need that as many applications are now fully functional in Chrome/Chromium based browsers. If you need it, Microsoft is planning to support IE mode through 2029. Microsoft has published a transition guide. query.prod.cms.rt.microsoft.com: Microsoft Edge + Internet Explorer mode | Getting Started guide
Read more in
- Microsoft reminds of Internet Explorer’s looming demise in June
- Internet Explorer 11 desktop app retires June 15, 2022
- Internet Explorer 11 desktop app retirement FAQ
Cyclops Blink Now Targeting ASUS Routers
Researchers from Trend Micro say that the Cyclops Blink malware is targeting ASUS routers. Several weeks ago, it was noted that the malware was targeting WatchGuard Firebox devices. Cyclops Blink has been linked to the Sandworm advanced persistent threat (APT) group.
Note
- See my comment about the MikroTik tool released by Microsoft. We need an easier way to identify out of date or misconfigured routers.
- Initial reports of Cyclops Blink included speculation that the Sandworm group would be porting it to other platforms. There is not a firmware update from ASUS to resolve the vulnerability, as such affected routers will need to be factory reset. Mitigations, which apply to most routers, include replacing any end of life devices, disabling remote management, changing default admin passwords, and keeping your firmware updated. If you have any doubts, go through the factory reset and recreate your configuration including the mitigating steps above. Don’t forget to really get rid of the old unsupported devices you’ve got on the shelf “just in case.” It’s no good if your service restoration is followed by a compromise.
Read more in
- ASUS warns of Cyclops Blink malware attacks targeting routers
- Sandworm-linked botnet has another piece of hardware in its sights
- Cyclops Blink Sets Sights on Asus Routers
The European Union Aviation Safety Agency (EASA) has warned of Global Navigation Satellite Systems (GNSS) outages related to Russia’s invasion of Ukraine. Last week, Finland’s Traficom warned of GPS outages near its eastern border with Russia; those issues appear to be affecting other countries in the area, including Poland, Lithuania, and Latvia.
Note
- This may in some cases affect devices using GPS to synchronize time.
- These are jamming or spoofing attacks. The EASA bulletin has both issues aviation authorities, service providers and operators may face as well as possible mitigations/recommendations. They include both validation and testing of contingency plans. How viable is it really to grab a map and look out the window when you don’t have aids such as a GPS? While the best defense is to stay away from affected areas, not all flights have that option making preparation and planning crucial.
Read more in
CISA, FBI Warning of Potential SATCOM Threats
The Cybersecurity and Infrastructure Security Agency (CISA) and the FBI have issued a joint alert with information about strengthening the cybersecurity of SATCOM networks. The alert says that “Given the current geopolitical situation, CISA’s Shields Up initiative requests that all organizations significantly lower their threshold for reporting and sharing indications of malicious cyber activity.” It also lists mitigations for organizations to employ.
Note
- Recommended mitigations include reviewing trust relationships, use of MFA, principle of least privilege, increased monitoring, shortened update/patch intervals and use of strong encryption wherever possible. These are good mitigations for non-SATCOM networks too – consider how they apply to your enterprise.
Read more in
- Alert (AA22-076A) Strengthening Cybersecurity of SATCOM Network Providers and Customers
- CISA, FBI warn US critical orgs of threats to SATCOM networks
Azure Automation “AutoWarp” Flaw Fixed in Four Days
Microsoft fixed a critical flaw in Azure Automation late last year. Dubbed “AutoWarp,” the vulnerability could have been exploited to allow users to access and take control of other users’ accounts. Researchers from Orca Security reported the flaw to Microsoft on December 6, 2021. Microsoft fixed the vulnerability four days later.
Note
- This is a success story where responsible disclosure and prompt response by the software owner quickly closed a serious cross-tenant cloud threat. Points out two things: (1) vulnerabilities will continue to be found in cloud platforms, meaning (2) platform-specific security best practices (like Microsoft’s for Azure or the excellent Center for Internet Security Azure Benchmark (www.cisecurity.org/benchmark/azure) need to be following and audited against.
- While it remains true that cloud security providers, especially the larger players, are able to make their platforms more secure than many organisations can make their own on-premise solutions, it should always be remembered that security is never a binary thing and continuous risk assessment, multi-layer controls, combined with detection and response capabilities still remain top priorities when you move to the cloud.
- This was resolved in four days; the vulnerability disclosure agreement didn’t allow publication until March 7th. Make sure that you are following Microsoft’s best practices for Azure Automation (docs.microsoft.com/en-us/azure/automation/automation-security-guidelines) – use accounts with the minimum required privileges, use managed identities rather than Run As accounts and rotate keys periodically. If you must use Run As accounts, renew their certificates periodically, verify permissions are as locked down as possible. Secure credentials, certificates, connections and encrypted variables; use either Microsoft or customer managed keys to keep this information encrypted.
Read more in
- AutoWarp: Critical Cross-Account Vulnerability in Microsoft Azure Automation Service
- Microsoft fixes ‘AutoWarp’ vulnerability in Azure Automation inside of four days
- Microsoft praised for quickly resolving Azure Automation cloud security vulnerability
- Microsoft Azure ‘AutoWarp’ Bug Could Have Let Attackers Access Customers’ Accounts
US Legislators Pass Bill Requiring Critical Infrastructure to Report Cyberattacks and Ransomware Payments
Owners and operators of US critical infrastructure will be required to report cyberattacks to the Cybersecurity and Infrastructure Security Agency (CISA) within 72 hours of their detection, and must report ransomware payments within 24 hours. The provisions have been included in Congress’s omnibus spending bill, which now heads to the president’s desk.
Note
- There are a few meaningful items in this bill: CISA is tasked to increase its pen testing resources; it requires federal agencies to do more/be better at threat hunting (but first an 18-month study); modernizing FedRAMP cloud security requirements; and studies on use of honey pots and a government SOC as a Service offering. Most of the rest is increasing reporting by government agencies, including incident and vulnerability reporting. There’s a lot that is aimed at making sure CISA is authorized to do stuff that it has already been doing and making sure they report to Congress more, and a lot of reports that are just updates on progress on last year’s President Biden cyber memo in areas like Zero Trust, dashboard, metrics, software inventory etc.
- Don’t assume this condones ransomware payment; you still need to abide by OFAC rules. The legislation creates a council to coordinate reporting requirements, as well as formalization through the federal rule-making process which includes consultation with industry. Don’t expect CISA to go slow here, even though they have two years for that process to complete. The legislation also includes a requirement for CISA to warn organizations of vulnerabilities. Make sure that you’re signed up for that; CISA has a reputation for providing relevant and actionable information.
Read more in
- US Congress Passes Cyber Incident Reporting Mandate
- Hit by ransomware or paid a ransom? Now some companies will have to tell the government
- Congress approves cyber incident reporting for critical infrastructure
- Thompson, Katko, Clarke, Garbarino Laud Cyber Incident Reporting Passage
Cobalt Strike Spreading Through Phony AV Updates
According to a warning from Ukraine’s Computer Emergency Response Team, fake Windows anti-virus updates are being used to spread Cobalt Strike and other malware. The campaign involves phishing emails urging recipients to download “critical security updates.”
Note
- Beware of email bearing security updates. You should be pushing required updates to enterprise users, disabling local actions if possible. Make sure that users are aware of the update process and how legitimate communication will look. Also ensure that you’ve enabled URL rewrite/security for email services, as well as layer 7 controls to block access to known bad sites.
- Apart from a Cobalt Strike beacon, the attack chain also pulls two payloads written in Golang: GraphSteel and GrimPlant. The Cobalt Strike payloads should be easily detected but attackers are moving to other languages, like Go, Rust, NIM, to avoid preventive controls.
Read more in
Intel Agencies Investigating Viasat Cyberattack
US, French, German, and Ukrainian intelligence agencies are reportedly investigating the late February cyberattack against satellite Internet provider Viasat. The attack caused connectivity to plummet, and modems used to connect to Viasat’s KA-SAT satellite are no longer functioning.
Note
- The attack against Viasat has so far, in my opinion, been the most interesting facet of “cyber” in this war. It looks like so far, Viasat is still attempting to put together all the pieces, but based on current reporting, Russian forces had some access to a ground station in Ukraine (either physical access, or via remote connectivity). The initial assessment, which suggests that the affected terminals will need to be reset by hand or even entirely replaced makes for a lengthy and expensive recovery process with thousands of sites like wind generator plants to be visited by technicians.
- As an example of how interconnected and interdependent our world has become, this attack apparently impacted on the ability of a German wind turbine manufacturer to remotely monitor and manage thousands of wind turbines across Europe.
www.datacenterdynamics.com: Satellite outage impacts more than 5,000 wind turbines across Europe - A flaw in the KA-SAT management system allowed access to customer modems, which were subsequently disabled by the attack. Impacted devices need replacement, which is hindered by both supply chain and conflict related challenges. Assess the importance and reliance on Internet connectivity for your business and have a backup commensurate with critical service needs. Note that if your backup is of lower capacity than your primary connection, you will need to have a plan for how you’re going to restrict access to critical systems only. Don’t forget to factor in how long you can operate with a reduced connection. It may turn out that you need a secondary connection of equal bandwidth to your primary. I harken back to when we had DS1 fail-over links for our primary DS3 connection, which were dropped because they simply were not viable as a fail-over and drove the need for parity of capacity.
Read more in
- Exclusive: U.S. spy agency probes sabotage of satellite internet during Russian invasion, sources say
- New narrative forms on Russia-Ukraine cyberwar as Viasat outage investigated
GPS Disruptions Affecting Air Traffic in Parts of Finland
Traficom, Finland’s Transport and Communications Agency, has noted disruptions in global positioning system (GPS) signals near its eastern border. A plane flying from Tallinn, Estonia, to Savonlinna, Finland was forced to return to Tallinn after the onboard GPS navigation failed. “Traficom does not know what is causing the interference … . GPS interference can be momentary and local, which makes it difficult to verify afterwards.”
Note
- Russian forces have disrupted GPS in that area in the past during military exercises. In Finland, some more remote airports can only be used if reliable GPS coverage is available as no other electronic landing aids exist. For most commercial air traffic GPS is not required, but it is helpful, and disruptions may lead to lower capacity on specific routes. Some routes around Russia are seeing an increase in traffic and are somewhat congested after routes across Russia have been closed to many airlines.
- GPS spoofing attacks are relatively simple and inexpensive to carry out: e.g., a 1KW jammer can block a GPS receiver as far as 80KM away and only cost a few hundred US dollars. This is intended as a warning to airlines, putting them on notice to not rely on their GPS for navigations and landing as they are supposed to have other systems which assist during a GPS outage. Even so, the pilots may not want or be prepared to fall back to other systems and elect to turn back rather than risking a failed landing.
Read more in
- Disruptions in GPS services hinder air traffic in central and eastern Finland
- Finnish govt agency warns of unusual aircraft GPS interference
- Unusual amount of reports about GPS interference near the eastern border of Finland
Data Centre Security Guidance for Owners and Users
The UK’s National Cyber Security Centre and Centre for the Protection of National Infrastructure have jointly published guidance for data centre security. There are separate documents for owners and for users.
Note
- This is yet another excellent guide published by the UK’s NCSC. I strongly recommend that security professionals refer to the NCSC website for some excellent guidance on various security matters.
- When I was working on data center design, the focus was on physical and environmental stability, security, and resilience. I recall one provider that located their two data centers seven miles apart due to tornado threats. Today there is an equal, if not greater, need to factor in logical attack paths, both for the facility control systems and the systems housed within them. Make sure you understand what threats the data center is mitigating and what you need to focus on. Use the guides to drive the conversation. Don’t forget to include people and supply chain threats in the conversation.
Read more in
- Joint security guidance offered to data centre operators and users
- Data centre security: Guidance for owners
- Data centre security: Guidance for users
- Data centres are still a tempting target for hackers. Here’s how to improve your security
Federal Register: US Federal Communications Commission Seeks Comments on BGP Security Issues
Several weeks ago, we ran a story about the FCC seeking comments regarding Border Gateway Protocol (BGP) security. Below is a link to the text of the notice in the Federal Register. The FCC notes that “BGP’s initial design, which remains widely deployed today, does not include security features to ensure trust in the information that it is used to exchange. BGP was designed at a time when the number of independently managed networks on the internet was low and the trust among them was high.” Comments will be accepted through April 11, 2022. Reply comments will be accepted through May 10, 2022.
Note
- While the conversation has been ongoing about improving BGP security, now is the time to reach out and comment. Use the FCC’s Electronic Comment Filing System (www.fcc.gov/ecfs) to electronically file comments. There are also provisions for people with disabilities wishing to comment – email [email protected] for options.
Read more in
CISA’s Cyber Storm VIII Exercise
The US Cybersecurity and Infrastructure Security Agency (CISA) recently concluded Cyber Storm VIII, a national cyber exercise. The three-day event included more than 2,000 participants from both public and private sector organizations. The National Cyber Exercise is conducted every two years.
Note
- Take a moment to review CISA’s “Shields Up” guidance (www.cisa.gov/shields-up) to reduce the likelihood of an intrusion, speed detection, be better prepared to respond and maximize resilience to a destructive incident.
- Practice, practice, practice! It is required for every sport you have ever played; it is required in information security. The more you train, the better prepared you will be for the real attack.
Read more in
- CISA Hosts Eighth Cyber Storm Exercise With More Than 200 Organizations
- US cybersecurity agency concludes massive exercise
WordPress Update Released
WordPress has released version 5.9.2 of its content management system to address one high-severity and two medium-severity vulnerabilities. Users are urged to update to the newest version of WordPress. The high-severity stored XSS flaw could be exploited by users with access at the contributor-level and above to inject JavaScript into posts. The other two flaws are prototype pollution issues.
Note
- You should have a notice that your WordPress sites were already updated to 5.9.2, if they are not, find out why and make sure to not only apply the update but also make sure future updates will be automatically applied. With the ongoing threats to WordPress, the risks of regression testing outweigh the risk of having to roll back due to a bad update. Note that Wordfence has already provided WAF rules for their paid users for this attack, the free version will be updated April 10th.
Read more in
Healthcare Organization Breaches in Colorado and Alabama
Data security breaches at healthcare organizations in Colorado and Alabama have compromised sensitive information belonging to more than half a million individuals. South Denver Cardiology Associates disclosed that a breach in early January 2022 resulted in the exfiltration of data belonging to nearly 290,000 patients. Norwood Clinic in Birmingham, Alabama disclosed that nearly 230,000 individuals were impacted by a breach that occurred last fall.
Note
- Two recurring themes to contemplate here. First, long delays between the attack and notification allow sufficient time to forensicate issues, and put a limit for the sanity of your users and to not get crosswise with regulators. Second, email was a key component in the compromise. Don’t wait to implement both technical controls, MFA, strong passwords, anomaly detection and email security tools; as well as making sure that you are providing current relevant training to users. Studies have found that security training fades in as few as six months without a refresher.
Read more in
- Over 500,000 Patients Hit by Data Breaches at Healthcare Firms in Alabama, Colorado
- Cyberattack on Norwood Clinic compromises data tied to 228K patients
- Notice to Our Patients of a Privacy Incident (PDF)
- Notice of Data Security Incident (PDF)
Secret U.S. surveillance program collects Americans’ money-transfer data
Sen. Ron Wyden has revealed that a law-enforcement arm of Homeland Security participated in “a secret bulk surveillance program that collected millions of records about certain money transfers of some Americans without a warrant.” The program collected information on domestic and international transfers that exceed $500 to or from several U.S. states. It’s not clear how the data is being used (or even if it’s legal!) but apparently dates back to at least 2010. A non-profit was set up to host the money-transfer data, which meant authorities could mine the data without needing a court-approved warrant.
Ransomware roundup: REvil, NetWalker ransomware members extradited to U.S.
CSO, Justice Department: The DOJ has extradited an alleged member of the REvil ransomware group, Ukrainian national Yaroslav Vasinskyi, 22, after he was arrested in Poland. He’s accused of being “responsible” for the attack on Kaseya, per the DOJ, which left hundreds of its downstream customers also affected by ransomware. He faces up to 115 years in prison if convicted. Meanwhile, a former Canadian government employee was extradited to the U.S. to face charges for his alleged involvement with the NetWalker ransomware group, which resulted in the seizure of $28 million in bitcoin.
Ubisoft reveals “cyber security incident,” won’t say much
Gaming giant Ubisoft says it has “experienced a cyber security incident that caused temporary disruption to some of our games, systems, and services” and issued a company-wide password reset, but that there is “no evidence” that any player information was accessed or exposed. (Ubisoft has more than 117 million players worldwide.) But when I asked the company what I thought were basic and reasonable questions like, what was the cyber security incident, or if it had logs or the means to detect improper data access or exfiltration, Ubisoft declined to comment. Classic case of “please disperse” dot gif.
Read more in
Google blocks China-based phishing campaign targeting U.S. government
Google Threat Analysis Group lead Shane Huntley said the company sent out a recent batch of warnings about a China government-backed phishing campaign targeting Gmail users affiliated with the U.S. government. The campaign was blamed on APT31, a group that previously targeted Biden presidential campaign staff in 2020 just before the election. Huntley said TAG doesn’t have evidence to suggest this campaign was related to the war in Ukraine.
NSA probes sabotage of satellite internet during Russian invasion
Remember last week, we had a story about how satellite Viasat was hacked across Europe, causing widespread outages and communication issues with wind turbines that rely on satellite connectivity. Now there’s more: the U.S. National Security Agency is reportedly investigating the attack, which began at the time Russian forces crossed into Ukraine on February 24. Per Reuters, the hack disabled modems that connect with Viasat’s European satellite network. Viasat is also a defense contractor for the U.S. and its allies, hence why the NSA is involved.
Inside ‘Project Texas,’ TikTok’s answer To U.S. lawmakers’ China fears
TikTok is close to a deal for Oracle to store its U.S. users’ information without its China-based parent company ByteDance having access to it, as part of an effort to address U.S. government regulatory concerns about data security and integrity. The agreement would come more than a year after the U.S. told ByteDance to divest TikTok over fears that U.S. user data could be handed to Beijing. It’s not known yet if this will appease U.S. regulators. BuzzFeed News has a deeply reported piece on “Project Texas,” which aims to decouple TikTok from China and bring U.S. user data back to its territory. More from @ebakerwhite’s tweets.
Read more in
Inside Conti leaks: The Panama Papers of ransomware
@NPRDina has a feature (and podcast) out looking at the Conti ransomware leaks, said to be one of the most successful online extortion groups. A couple of weeks ago, Conti declared support for the Russian government’s invasion of Ukraine, apparently hitting a nerve with someone on the inside, because they leaked the group’s internal Jabber server — with almost two years of their private correspondence. But Conti is already bouncing back, with two new breaches under its belt since the leak.
UPS flaws allow for remote code execution and remote fire-based interruptions
After two years of pandemic, a war, and “that whole thing” which we try not to think about, burnout is hitting everyone pretty hard — even inanimate technology. Turns out a trio of vulnerabilities involving a bad implementation of TLS in uninterrupted power devices sold by a Schneider Electric subsidiary could result in remote code execution and literal smoldering of the entire unit. Whoops. Armis explains more about the flaws in a blog post.
Read more in
Geofence warrants found unconstitutional in Virginia
Authorities in Virginia “violated the Constitution” when they demanded location data from Google to find people who were close to the scene of a 2019 bank robbery, according to a federal judge. That could make the widely used policing tactic, which effectively reverse engineers who were at the scene of a crime based on their Google-collected location data, more difficult for police to use geofence warrants across the state. @elizabeth_joh has more in the tweets.
Twitter launches Tor onion service making it easier to access in Russia
Twitter has become one of the most significant services to create a Tor onion service to allow users around the world — including countries like Russia where censorship is rife, especially following its invasion of Ukraine — to access the site. Twitter’s Tor address can be found on its supported browsers page. @AlecMuffett, who helped Facebook set up its Tor service back in 2014, wrote in a tweet thread and a blog post why a dedicated onion address is better than just browsing over Tor. It comes as big web security companies leave Russia, including Czech-based antivirus company Avast and website certification firm DigiCert. Several other backbone companies have also pulled their business from the country, leaving vast swathes of the Russian population without access to the internet outside of its borders. Some are even taking to “spamming” Russian people to spread information about Russia’s military assault on Ukraine.
Read more in
- Big Web Security Firms Ditch Russia, Leaving Internet Users Open To More Kremlin Snooping
- Ukraine: Spam website set up to reach millions of Russians
- Why offer an Onion Address rather than just encourage browsing-over-Tor?
Google to acquire Mandiant for $5.4 billion
And, this week saw one of Google’s biggest acquisitions — almost out of nowhere. Google Cloud will acquire security giant Mandiant for about $5.4 billion, which sits between Google’s massive $12 billion acquisition of Motorola (patents, patents, patents!) and Nest Labs at $3.2 billion. Mandiant, the incident response side of things, if you recall, was bundled with FireEye, the product business, until FireEye was spun out and sold off for $1.2 billion. It’s going to be a huge deal for Google, allowing it to beef up its cloud security offering, which generates close to $20 billion a year and about 7% of the worldwide cloud market share.
Read more in
- Google boosts cloud security with $5.4 billion Mandiant deal
- Google makes second-largest acquisition ever: $5.4 billion for Mandiant
Linux has been bitten by its most high-severity vulnerability in years
Ars Technica: “Dirty Pipe” is a new vulnerability that has the potential to allow untrusted users to execute code on a vulnerable Linux device or machine, allowing for backdoors or creating unauthorized user accounts. The bug is half-named after Dirty Cow, a Linux flaw that came to light in 2016, which allowed for the privilege escalation and rooting of any Android phone, regardless of its version. Dirty Pipe, meanwhile, is similar in nature but refers to the Linux “pipeline” mechanism for sending data from one process to another. According to @nopslide, Dirty Pipe is easier to exploit than Dirty Cow. Patches have been released. @dangoodin001 explains this well, as usual.
Read more in
Mitel devices abused for record-breaking DDoS amplification attack
A vulnerability called TP240PhoneHome (tracked as CVE-2022-26143) found in Motel devices, of which tens of thousands are deployed in government and private organizations around the world, can be abused to carry out DDoS attacks with a massive amplification ratio by about 4.2 billion to 1. That means a single spoofed packet can result in massive amounts of traffic to overwhelm systems, knocking them offline. As @campuscodi notes, a single reflected request can crash pretty much any website. Shadowserver, which helped find the bug, said about 2,600 devices need to be patched. The bug has already been abused by advanced attackers for carrying out DDoS attacks, per Cloudflare.
Mitel Collaboration Systems Exploited to Launch Amplified DDoS Attacks
Attackers have been exploiting incorrectly provisioned Mitel MiCollab and MiVoice Business Express collaboration systems to launch massive amplified distributed denial-of-service (DDoS) attacks against financial institutions, logistics companies, broadband ISPs, and other organizations. The issue reportedly allows for an amplification factor as high as 4.3 billion to one.
Note
- Luckily, the number of vulnerable systems is rather limited. But the amplification factor still makes this a debilitating attack. Make sure you are not part of the problem and update your devices! Efforts are under way to notify organizations exposing vulnerable devices.
- Packet amplification ratio of 4,294,967,296:1 is mind blowing. Anyone that has defended against a DDoS attack is very familiar with what amplification is and this ratio is unheard of.
- This technique, dubbed TP240PhoneHome (CVE-2022-26143), leverages UDP port 10074, a system test service, which should not be Internet accessible. If you have the Mitel products, verify that you’re restricting access to that service. The most recent software update from Mitel makes sure this port is locked down. Even so, verify that you’re protecting and monitoring use of that service. All this attack takes is a single malicious command to release a flood of 4.3 billion packets over about 14 hours, or about 2.5TB of traffic at about 393mb/sec from a single amplifier.
Read more in
- New method that amplifies DDoSes by 4 billion-fold. What could go wrong?
- Mitel VoIP systems used in staggering DDoS attacks
- Hackers Abuse Mitel Devices to Amplify DDoS Attacks by 4 Billion Times
Russia Creates TLS Certificate Authority
Russia has created its own TLS certificate authority to issue certificates for Russian sites whose TLS certificates have expired or been revoked. Yandex and Atom are currently the only browsers that recognize the new certificate authority as trustworthy.
Note
- Certificate authorities have also been revoking some certificates for Russian organizations. As a result, you may get warnings when visiting affected sites. Do not add the new Russian CA as a trusted CA in your browser/operating system. This new CA operates outside the rules governing CAs in current trusted CA lists. Currently, free certificates from Let’s Encrypt should still work for Russian sites.
- The current sanctions prevent certificate renewals with certificate issuers outside Russia and vetting a new issuer for inclusion in browsers is a lengthy process unlikely to commence until those sanctions are lifted. If you must interact with a site that uses these certificates e.g. Sherbank, VTB, or the Russian Central Bank, you will need to both verify you will not run afoul of sanctions and either add the CA’s public cert to your browser or use the Russian browsers which already support it. Time will tell where this goes.
Read more in
Securities and Exchange Commission Proposes Breach Disclosure Rule
The US Securities and Exchange Commission (SEC) has proposed a rule that would require publicly-traded companies to report cyberattacks. The rule would amend the SEC-s Form 8-K reporting requirements to include disclosure of cyberattacks “within four business days after the registrant determines that it has experienced a material cybersecurity incident.”
Note
- This rule proposes reporting in four days, versus recent legislation proposing 72 hours. What is needed is both a consistent timeframe and reporting format so companies aren’t confused about which rules apply. For investors, disclosure has to use the same measurement across companies, perhaps leveraging a maturity model, to provide a meaningful designation of risk for decision making.
- “Material cybersecurity incident” is mentioned 64 times in the 129 page rule but I could not find the actual definition.
- This wording is well-intentioned and the minimum that an investor user of the Form 8-K might expect. However, given the time between such incidents and their detection, as reported in the Verizon Data Breach Incident Report, it acts late and will not do much to limit or explicate the investor’s risk. Perhaps the SEC might ask management for an expression of its exposure to and tolerance for cyber risk.
Read more in
- SEC proposes mandatory breach reporting for publicly traded companies
- SEC proposes four-day rule for public companies to report cyberattacks
- Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure Proposed Rule (PDF)
Access:7 Vulnerabilities
A group of vulnerabilities collectively identified as Access:7 put hundreds of thousands of medical devices and ATMs at risk of denial-of-service attacks and data alteration and exfiltration. The flaws exist in the PTC Axeda Internet of Things (IoT) remote access tool. Three of the seven vulnerabilities are crated critical and could be exploited to remotely execute code.
Note
- Note that PTC phased out Axeda, replacing it with their ThingWorx platform. If you’re still using the Axeda solution you need to migrate after either applying the released patches or mitigations. The patches address these vulnerabilities. Note the mitigations include limiting where you’re running ERemoteServer.exe process, configuring agents and services to only listen on localhost, allowing communication only from trusted hosts.
Read more in
- Critical Bugs Expose Hundreds of Thousands of Medical Devices and ATMs
- Access:7 vulnerabilities impact medical and IoT devices
Microsoft Patch Tuesday
On Tuesday, March 8, Microsoft released updates to address more than 70 security issues in multiple products. Three of the vulnerabilities are rated critical. The updates include a fix for an issue that was preventing some data from being erased after resetting Windows 10 and Windows 11.
Note
- CVE-2022-23277 is another RCE for Exchange servers. It’s time, actually past time, to stop running Exchange on-premise. Remember to consider the burden of keeping up not only with flaws and remediation, but also with continuously applying the latest techniques to repel boarders when evaluating cloud migration.
Read more in
- Microsoft patches critical remote-code-exec hole in Exchange Server and others
- Microsoft’s latest Windows patches fix the bug causing user data not to be erased
- Microsoft Patch Tuesday, March 2022 Edition
- Microsoft Addresses 3 Zero-Days & 3 Critical Bugs for March Patch Tuesday
- Security Update Guide
Qakbot is Hijacking eMail Threads
According to a report from Sophos, the Qakbot botnet is now hijacking email conversations to spread malware. The malware operators inject messages into existing email threads in an attempt to trick users into downloading the malware. Qakbot has been known since 2008, when it was a Trojan designed to steal bank account access credentials.
Note
- Qakbot operates on the endpoint, stealing credentials for accessing email, as well as accessing websites to upload their malware payloads to help spread itself or added functions on behalf of other malicious actors. Enable MFA on your email accounts, make sure authentication tokens expire, triggering a re-authentication. Do not allow reusable passwords when accessing services from non-corporate systems or the Internet.
- Qakbot focuses on initial access and brokers that access to other threat actors with varying objectives spanning from ransomware to intellectual property theft. Keeping up with the latest tactics, techniques, and procedures is important so your organization can test, measure, and improve the detection and response.
Read more in
- Watch out for this phishing attack that hijacks your email chats to spread malware
- Qakbot Botnet Sprouts Fangs, Injects Malware into Email Threads
- Qakbot injects itself into the middle of your conversations
CISA Updates Conti Warning
The US Cybersecurity and Infrastructure Security Agency (CISA) has updated its Conti Ransomware alert to include indicators of compromise. The alert provides a list of “domains have [that] registration and naming characteristics similar to domains used by groups that have distributed Conti ransomware.”
Note
- Nothing net-new on the tactics, techniques, and procedures leveraged by Conti but very happy to see CISA providing those behaviors on top of indicators of compromise (IoC). Organizations should be evolving from consuming only IoCs to leveraging the indicators of behaviors (TTPs).
- Conti gains initial access via spearphishing (with malicious attachments), stolen/weak RDP credentials, fake software – leveraging SEO, social engineering over the phone, CVEs and other malware distribution networks. You know how to mitigate most of these; make sure your users are aware of their stake in the game. Then grab your CIO and initiate actions to finish your comprehensive MFA rollout. Have your SOC check the alert for any new IOCs.
Read more in
- CISA updates Conti ransomware alert with nearly 100 domain names
- U.S. Warns of Conti Ransomware Attacks as Gang Deals With Leak Fallout
- Alert (AA21-265A) Conti Ransomware
Ransomware-Related Extraditions
Two individuals have been extradited to the US to face ransomware-related charges. Yaroslav Vasinskyi of Ukraine was extradited to face charges related to the attack that targeted Kaseya; Vasinskyi was arraigned in Texas on Wednesday, March 9. Sebastien Vachon-Desjardins was extradited from Canada to face charged related to NetWalker ransomware attacks. His case is being handled in Florida.
Note
- These actors are behind the Revil Kaseya supply chain and NetWalker attacks. NetWalker was a RaaS service, recruiting affiliates to use their malware to attack sites, while the Kaseya leveraged a zero-day flaw in their remote management software, stole their signing key to sign malware, and used many interesting techniques including DLL sideloading to place a spoofed DLL in the Windows WinSxS directory, which gets loaded instead of the legitimate one. At this point endpoint protection systems and patches remediate these flaws and detection of these attempted exploits.
- While the Conti Leaks may suggest ransomware and illegal/unethical activity pays, it does not! Very happy (understatement) to see law enforcement working to get some of the people behind REvil and NetWalker through due process.
Read more in
- Feds extradite ransomware suspects from 2 prolific gangs in a single week
- Sodinokibi/REvil Ransomware Defendant Extradited to United States and Arraigned in Texas
- Alleged REvil suspect extradited and arraigned on ransomware spree charges
- Alleged hacker behind Kaseya ransomware attack extradited, arraigned in Texas
- REvil ransomware member extradited to U.S. to stand trial for Kaseya attack
- Former Canadian Government Employee Extradited to the United States to Face Charges for Dozens of Ransomware Attacks Resulting in the Payment of Tens of Millions of Dollars in Ransoms
- Ex-Canadian Government Employee Charged in NetWalker Ransomware Attacks
WordPress Security Whitepaper
According to a whitepaper from Patchstack, nearly 30 percent of critical flaws in WordPress plugins have never been patched. Patchstack also notes a 150 percent increase in reported vulnerabilities between 2020 and 2021.
Note
- Take a look at your WordPress site health dashboard to double check your security posture. Pay attention to both themes and plugins which are not being updated. If you have items which are not being updated, have the hard conversation about moving to replacements which are, particularly ones that are end-of-life. Make sure that you have a properly configured WAF which is getting regular updates. Note that getting regular updates of plugins, themes, or your WAF may require using the paid versions.
- This report explicates and documents the problem with WordPress plugins. Most come with no representation of quality, should be used only by design and intent, never by default, and must be rigorously policed and patched. While patching is expensive, in this case it is part of the cost of the quality and security for these plugins.
Read more in
Cyberattack Irreparably Damaged SATCOM Terminals in Europe
More information is emerging about the cyberattack that took down tens of thousands of SATCOM terminals across Europe in late February. It now appears that the attack damaged the terminals beyond repair.
Read more in
Cybersecurity Companies Offer Free Help to US Healthcare and Utilities
Three companies – Cloudflare, CrowdStrike, and Ping Identity – have offered free cybersecurity help to US hospitals and water and electric utilities. Services offered include multi-factor authentication and denial-of-service attack protection.
Note
- Like Google offering Workspace free to schools, it’s great to see these three vendors reaching out to healthcare, water, and electricity providers. These truly are critical infrastructure and often don’t have the resources to adequately mitigate risk.
- Lowering the cost of entry is a key enabler for services which have been both under attack and stretched to survive during the pandemic, let alone identified as likely targets in the anticipated retaliatory strikes from Russia. These offerings include endpoint, DDoS protection and authentication services which will allow these organizations to raise the bar and reduce the per-client impact of protecting them. The offer is for four months of services to hospitals and power and water utilities. If the need presents itself, the offer will be extended to other sectors.
Read more in
Nvidia Code-Signing Certificates Stolen
Code-signing certificates stolen from Nvidia are being used to sign malware. The Lapsus$ extortionists claim to have stolen 1TB of data from Nvidia, and began leaking it to the Internet after Nvidia refused to meet their demands. Both of the stolen certificates are expired, but Windows will allow drivers signed with the certificates to be loaded.
Note
- Breach assessments never get better with time. Initial reports indicated a “minor” breach at NVidia. More recent reports suggest a complete compromise. Malware signed using the stolen certificates has already been uploaded to Virustotal.
- One of the certificates expired in 2014, the other in 2018. Windows will accept drivers signed by certificates, without a timestamp, issued prior to July 29, 2015 which chains to a supported cross-signed CA. This is to support backward compatibility and allow old software to be reinstalled. You can mitigate the risk by adding these certificates to the untrusted certificate stores, but that will also block installation of legitimate Nvidia driver versions signed by these certificates.
Read more in
- Leaked stolen Nvidia cert can sign Windows malware
- NVIDIA’s Stolen Code-Signing Certs Used to Sign Malware
- Malware now using NVIDIA’s stolen code signing certificates
Samsung Galaxy Source Code Leaked
Samsung has acknowledged that a breach of its systems led to the theft and subsequent leak of source code for its Galaxy devices. The thieves have leaked nearly 200GB of Samsung data.
Note
- The Lapsus$ gang, the same ones from the Nvidia breach, are also behind this attack. They don’t follow the traditional ransomware pattern of a payment with a release of data when unpaid. Instead, they release the data online to have their targets bid for their decryption key and data erasure. While Samsung devices run the open source Android OS, they also have the Samsung Knox security suite, which is approved for protection of low-level classified data in the US and UK, and having the source could allow the protections to be reverse engineered. Additional security component source code leaked may make compromising Samsung devices easier. Watch for security updates from Samsung designed to mitigate these risks.
Read more in
- Lapsus$ extortionists dump data online as Samsung admits breach
- Samsung confirms Galaxy device source code leaked after breach
NSA Publishes Network Infrastructure Security Guidance
The US National Security Agency (NSA) has published a cybersecurity technical report on Network Infrastructure Security Guidance. The report addresses network architecture and design; security maintenance; authentication, authorization, and accounting; admin accounts and passwords; remote logging and monitoring; remote administration and network services; routing; interface ports; and notification banners.
Note
- While many are focusing on Zero Trust, this guide is focused first on securing your existing network, while remaining applicable to your Zero Trust initiatives in the future.
Read more in
- NSA report: This is how you should be securing your network
- Network Infrastructure Security Guidance (PDF)
Linux Dirty Pipe Bug
A newly-detected Linux vulnerability affects Linux kernel versions 5.8 and later. Dubbed Dirty Pipe, the flaw can be exploited to allow non-privileged users to overwrite data in read-only files.
Note
- Despite the name, your plumber is not going to be able to address CVE-2022-0847. A publicly disclosed exploit alters the /usr/bin/su command, dropping a shell in /tmp and then executing it. The bug is fixed in Linux kernel versions 5.16.11, 5.15.24 and 5.10.102. The last twelve months have included multiple Linux privilege escalation flaws including iSCSI, kernel bugs, extended Berkeley Packet Filter and polkit pkexec, clearly leaving the free time we had after Flash was retired. Keep an eye on your Linux distros, keeping them not only patched, but also lifecycle out old versions prior to de-support/EOL dates.
- This is a relatively simple to exploit privilege escalation vulnerability and an exploit is available. Sadly, not all distributions have patches available yet.
Read more in
- New Linux bug gives root on all major distros, exploit released
- Linux has been bitten by its most high-severity vulnerability in years
CISA Adds 95 Flaws to Known Exploited Vulnerabilities Catalog
The US Cybersecurity and Infrastructure Security Agency (CISA) has added 95 flaws to its Known Exploited Vulnerabilities Catalog. Binding Operational Directive (BOD) 22-01 requires Federal Civilian Executive Agencies to mitigate vulnerabilities by deadlines listed in the catalog.
Note
- Sort the catalog by date added to catalog. Most have March 2022 due dates, with the majority of the new issues being Microsoft (Office, Windows and IE) products, Cisco software (IOS, IOS EX, RV series routers), Adobe Flash and Oracle Java. Most of these are simple to either fix or retire the product, such as Flash Player and old Java versions. Even if you’re in the private sector, this database is a good resource to cross check your enterprise vulnerability management program for omissions.
Read more in
- With Ukraine driving urgency, CISA adds 95 bugs to its catalog of known exploited vulnerabilities
- Get patching now: CISA adds another 95 flaws to its known exploited vulnerabilities list
- CISA Adds 95 Known Exploited Vulnerabilities to Catalog
- Known Exploited Vulnerabilities Catalog
HSCC’s Model Contract Language for Medtech Cybersecurity
The Healthcare and Public Health Sector Coordinating Council Cybersecurity Working Group has published a guide to model contract language for medtech cybersecurity. “The purpose of [the] Model Contract Language is to offer a reference for shared cooperation and coordination between Healthcare Delivery Organizations (HDOs) and Medical Device Manufacturers (MDMs) regarding the security, compliance, management, operation, services, and security of MDM managed medical devices, solutions, and connections.”
Note
- Finding relevant contract language is always a challenge for me. Leverage the heck out of this model; remember when they say MDM the mean Medical Device Manufacturers, not mobile device management (breathe). The document provides guidance on areas to cover, structure of the contract, sample language and context so you can also answer the “where did that come from” question.
- This is a good example of the expression of the security expectations that the vendor and the user should have of each other. The use of such expressions in other relationships can go a long way toward improving our security posture.
Read more in
- Model Contract-Language for Medtech Cybersecurity (MC2)
- New HSCC insights target cybersecurity contract language for medical tech
Firefox Emergency Updates
Mozilla has updated Firefox to address a pair of critical vulnerabilities. Both use-after-free flaws are being actively exploited. The updated products are Firefox 97.0.2, Firefox ESR 91.6.1, Firefox for Android 97.3.0, and Focus 97.3.0.
Note
- These flaws affect the Thunderbird email client as well as Firefox. Patch both.
- These updates address CVE-2022-24685 and CVE-2022-24686, rated critical. Note that Focus and Thunderbird are included in this update, not just the browsers. These are also on the CISA vulnerabilities catalog with a due date of 3/21/22. Given these are Zero-Day flaws and active exploited, I would say deploy the updated versions now.
Read more in
- Critical Firefox Zero-Day Bugs Allow RCE, Sandbox Escape
- Mozilla fixes two critical Firefox flaws that are being actively exploited
- Mozilla Firefox 97.0.2 fixes two actively exploited zero-day bugs
- Mozilla Foundation Security Advisory 2022-09
PressReader Outage
PressReader systems suffered a cyberattack on Thursday, March 3, affecting availability of more than 7,000 publications. The attack occurred days after PressReader removed Russian publications from its catalog and announced that it would make all its content available without change in Ukraine. The content processing system has been restored and is now operating normally.
Note
- PressReader was suggested as a popular alternative to the traditional news reprints on a vacation. While not the same as the paper in your hand, (I’m old-school) it does make access to news easy. PressReader has restored services and working to get content released. They are prioritizing titles from Europe, Africa and the Middle East, followed by the Americas and, finally, Asia. Follow their progress on their status update page: care.pressreader.com: Updates for users
Read more in
- PressReader service partially returns after cyberattack causes outages at 7,000+ publications
- PressReader Suffers Cyber-Attack
Vulnerability: Patches for critical issues in Cisco video communications services
This week, Cisco has disclosed two critical flaws affecting their Expressway Series and TelePresence video communications service. The issues are tracked as CVE-2022-20754 and CVE-2022-20755, both scoring high on CVSS at 9.0.
The first vulnerability allowed an authenticated user with read/write access to perform path traversal attacks using the cluster database API. An attacker could use this vulnerability to overwrite arbitrary files on the operating system potentially leading to device takeover. The vulnerability was caused by a failure to fully validate the input that users supplied to the API — a form of injection attack.
The second vulnerability was a command injection vulnerability on the web-based management interface that allowed authenticated users to perform arbitrary command execution. Again, the root cause is insufficient input validation.
Cisco confirmed that they have no evidence that either vulnerability was exploited on live systems, but have nevertheless advised customers to upgrade their systems to the latest version to minimize the likelihood of any exploit.
Vulnerability: Security vulnerability in self-managed GitLab instances
Self-managed versions of the popular CI/CD platform GitLab are vulnerable to attack through a GraphQL API, according to research published this week in TheHackerNews. The vulnerability is tracked as CVE-2021-4191, with a CVSS score of 5.3.
The vulnerability was discovered and reported by a security researcher at Rapid7, and initially disclosed on 18 February 2021. It has been patched in a recent update from GitLab, and all users on self-managed instances are advised to update their installations as soon as possible.
The vulnerability allowed an unauthenticated user (API2:2019 — Broken authentication) to access a GraphQL endpoint and collect private information of other registered users, such as names and email addresses. These details could be invaluable to attackers performing initial reconnaissance of installations, leading to brute-forcing or guessing of passwords.
Estimates suggest that a large number of GitLab installations could be affected by this vulnerability.
Vulnerability: Security bug affects campus access control system
The third and final vulnerability this week affects an access control system for a campus: a curious user discovered that the backend API of the mobile application did not authenticate users (another case of API2:2019 — Broken authentication). Effectively, this vulnerability gave an attacker a “master key” to all doors controlled by the system.
University student Erik Johnson had become frustrated at the poor performance of the GET Mobile application that controlled access to campus buildings, and used elementary network monitoring to understand the behavior of the application. He discovered that he had to submit location coordinates to validate proximity with the targeted door, but this could easily be spoofed through an API.
Johnson then made a startling observation: the API endpoints did not actually validate a student’s credentials. This meant that anyone who knew easily available identifiers (like student IDs, usernames, or email addresses) could access the target’s account, which together with the ability to unlock doors at known locations resulted in a digital “master key”.
Johnson attempted to report the vulnerability to the solution developer CBORD, but hit a wall there so resorted to disclosure through TechCrunch. Reports suggest the same company has been affected by a similar vulnerability in 2009.
This vulnerability has since been acknowledged and fixed by CBORD, who has also revoked all session keys of affected systems. It is unknown whether the bug was exploited for any malicious access, or whether users have been informed of the issue.
The APTs are Restless
In another report from the beginning of this month, Proofpoint describes a state-sponsored group they call TA445 targeting “European government personnel involved in managing the logistics of refugees fleeing Ukraine”. TA445 could well be the same as the (reportedly) Belarusian Ghostwriter team, known for its disinformation campaigns. The phishing campaign used a macro-enabled “list of persons.xls”, likely referring to a “kill list” of Ukrainian citizens that the Russian FSB is purportedly developing.
Azure’s Absolute Clanger
A researcher at Orca Security, Yanir Tsarimi, found that Microsoft’s Azure Automation service would give out authentication tokens that belonged to other accounts. The access granted by the stolen tokens depended upon the permissions granted by the legitimate Azure customer, but could potentially be very broad. Tsarimi points out how using cloud services can be a double-edged sword: “Cloud service vulnerabilities are scary. Think about all the companies potentially impacted by one single bug. On the flip side, it was fixed within a few days with minimal work”. This vulnerability was awarded a USD$40k bounty.
A second big bounty payout this week involved Meta. Security researcher Youssef Sammouda found a set of bugs in the way Facebook hosts online games. These bugs allowed a malicious game to steal a user’s Facebook access token and take over a user’s account and any other account linked to it (eg Instagram). This earned Sammouda a USD$98k bounty.
This isn’t Sammouda’s first go at some of these bugs — he’d previously earned USD$126k for bugs in the same Facebook technology and one of the new bugs was a bypass for a previous fix. Why get paid just once?
Conti Members Doxxed but Undeterred, For Now
Following in the footsteps of ContiLeaks, which has been leaking Conti chat logs and source code, other twitter accounts have been doxxing Conti members with details including photos, email addresses and phone numbers.
Brian Krebs’ series based on Conti’s leaked chat messages, covering Evasion, The Office, Weaponry and Cryptocrime, is stellar. It covers tooling, ransom negotiations, hacking and open source tools, and cryptocurrency pump and dump schemes. One thing that is not entirely illuminated is Conti’s relationship with Russian law enforcement and the FSB in particular. It looks like Conti received tips about law enforcement investigations into them and perhaps even some protection — a Conti member was assured that law enforcement investigations would go nowhere. But Krebs doesn’t report any indication of direct tasking from the police or FSB.
Despite Conti members being outed, however, it appears that the group has bounced back and resumed operations again. If a core group in Russia is immune from law enforcement action it’ll be a constant battle to keep a lid on the group.
Alexa’s Self-Abuse
Amazon Echo devices can issue commands to themselves via the Alexa voice assistant. An attacker could connect to it via Bluetooth and command the Echo to buy things, call phone numbers or change calendar appointments, for example.
ICANN Says it Will Not Revoke Russian Domains
The Internet Corporation for Assigned Names and Numbers (ICANN) has rejected a request from Ukraine to revoke top-level Russian domains and associated SSL certificates. In a publicly released reply, ICANN President and CEO Göran Marby wrote, “In our role as the technical coordinator of unique identifiers for the Internet, we take actions to ensure that the workings of the Internet are not politicized, and we have no sanction-levying authority. Essentially, ICANN has been built to ensure that the Internet works, not for its coordination role to be used to stop it from working.”
Note
- “Disconnecting” Russia is the wrong move IMHO. The Internet is one way Russians are still receiving outside news and it is making a difference. More targeted removal of particular domains may be more appropriate, but ICANN wouldn’t be the right way to accomplish this.
- Ukraine’s request to ICANN sought technical actions ICANN could execute; however, executing those actions would arguably violate ICANN’s own bylaws. If ICANN were to pick sides in this conflict, it would be pressured to pick sides in countless future conflicts where the public opinion could be more divided. The future political ramifications would likely decrease the world’s confidence in the security and stability of the Internet as a whole. ICANN wisely held true to its stated mission, which is “to ensure the stable and secure operation of the Internet’s unique identifier systems.”
- In short, ask the right organization to take actions and know their constraints. While I can appreciate the desire for the Ukraine to delist the .ru top level domain, revoke certificates and shutdown root servers as a sanction for Russia’s actions against them, ICANN can’t technically do all those things. Its role is the assignment of unique Internet identifiers aligned with global policies. Those same policies don’t allow for ICANN to take the actions requested; in fact, no single entity has the power to take those actions. It’s worth noting the root DNS servers are independently operated and geographically distributed for the same reasons. Yes, SSL certificates can be revoked by the issuers, but only for reasons outlined in their certificate handling agreements.
Read more in
- Response (PDF)
- ICANN rejects Ukraine’s request to block Russia from the internet
- ICANN responds to Ukraine demand to delete all Russian domains
Ukrainian Government Asks Tech Companies, Crypto Exchanges for Support
The Ukrainian government has asked Oracle and SAP to halt their business relationships with Russian entities. The government has also requested cryptocurrency exchanges to “block addresses of Russian users.” Earlier this week, Oracle tweeted that they have “suspended all operations in the Russian Federation.”
Note
- It may not be technically possible in all cases, but for sanctions to work, cryptocurrencies have to be included. It will however be difficult (and may take some time) to properly identify sanctioned entities exchanging payments via crypto currencies.
- Crypto Exchanges and cryptocurrency fall outside normal regulatory reach. As such, participation by the exchanges is going to be an individual choice. This is further complicated by having to have an accurate mapping of wallet to user and location as crypto facilitates obfuscation and indirection. It is not clear how effective these blocks will be.
Read more in
- Ukraine calls for corporate support as Oracle suspends Russian operations
- Ukraine asks cryptocurrency firms to block Russian users
Data Center Under Guard After SWIFT Excludes Russian Banks
A SWIFT data center in Switzerland is being physically guarded by law enforcement after the international financial messaging system excluded several large Russian banks from its network to comply with instructions from the European Council. SWIFT also has data centers in the Netherlands and the US.
Note
- SWIFT’s Swiss data center is a well-protected defensible space with five of seven floors under ground as well as being surrounded by high walls, barbed wire ,and security cameras in preparation for such a situation. Verify the physical security at your data center is not only commensurate with your anticipated threat scenarios, but also that those protections are tested regularly.
Read more in
Senate Passes Bill Requiring Critical Infrastructure Operators to Report Cyberattacks, Ransomware Payments
The US Senate has passed the Strengthening American Cybersecurity Act, which requires critical infrastructure operators to report cyberattacks to the Cybersecurity and Infrastructure Agency (CISA) within 72 hours. The legislation also requires the critical infrastructure operators to report ransomware payments within 24 hours. The Department of Justice (DoJ) says the bill has ”serious flaws,” noting that it does not include reporting incidents to the FBI.
Note
- The tools being deployed against the Ukraine critical infrastructure will work in the US as well. The architecture of US critical infrastructure, including the thousands of independent operators, makes attacks much more complicated, particularly if you’re looking to remain undetected or coordinate across operators. CISA is tasked with having visibility to critical infrastructure; having these notifications will help that insight. One hopes that as CISA resolves the issues in the GAO study above, the issues noted by DoJ can also be remedied.
- Legislation cannot do magic. The Verizon Data Breach Incident Report continues to show, that with the possible exception of ransomware attacks, the time from breach to discovery continues to be measured in weeks, not hours. While one might well argue that that is far too long, law alone will not change it.
Read more in
- Senate passes cybersecurity act forcing orgs to report cyberattacks, ransom payments
- DOJ officials criticize Senate-passed cyber bill
- How the Senate’s Cyber Bill Could Affect Health Sector
GAO: CISA’s National Critical Infrastructure Prioritization Plan Needs to Improve
According to a Government Accountability Office (GAO ) audit report, the Cybersecurity and Infrastructure Security Agency’s (CISA’s) National Critical Infrastructure Prioritization Plan is not living up to its potential. According to the report, “Nine of 12 CISA officials and all 10 of the infrastructure stakeholders GAO interviewed questioned the relevance and usefulness of the program.”
Note
- The central issue driving most of the negative comments is that the bulk of the US infrastructure looked at (energy, water, manufacturing, IT) is owned and operating by some combination of private industry and state/local government. The CISA started out in 2018 and largely took a top down approach as if the federal government drove how those systems worked and were governed. So, better involvement in early stages with “stakeholders” is a good recommendation. I’d add taking advantage of the ISACs that have been effective, especially the Multi-State ISAC. The Federal Government cannot move at the speed of threats and technology changes with a top down approach – we learned that in the old “Orange Book” computer security days and it still holds true.
- The distributed nature of critical infrastructure operators makes comprehensive communication and cooperation challenging. One hopes leveraging local ISACs which are more closely connected to those operators can facilitate the relationship and get stakeholders in the conversation. If you are an operator, a.k.a. stakeholder, make sure that you’re connected not only to your local ISAC, but also your local CISA office for resources and support.
Read more in
- CRITICAL INFRASTRUCTURE PROTECTION: CISA Should Improve Priority Setting, Stakeholder Involvement, and Threat Information Sharing (PDF)
- Watchdog: CISA must make critical infrastructure threats, resources a higher priority
Palo Alto Networks Unit 42 Looks at Medical Infusion Pump Vulnerabilities
Researchers at Palo Alto Networks’ Unit 42 examined data gathered from “more than 200,000 infusion pumps on the networks of hospitals and other healthcare organizations.” More than half of the devices were vulnerable to two flaws that have been known since 2019.
Note
- Unit 42 not only calls out the flaws, but also points out that mitigations are well-known and not applied. Their report includes a list of capabilities healthcare organizations need to embody to protect and secure Internet of Medical Things (IoMT) devices. At a high level, know what you have, know where it is, reduce risks (segmentation, monitoring and updates) and prevent threats. Look beyond the devices themselves and make sure your entire network ecosystem is secured.
Read more in
- Over 100,000 medical infusion pumps vulnerable to years old critical bug
- Infusion Pumps Impacted by Years-Old Critical Vulnerabilities: Report
- Know Your Infusion Pump Vulnerabilities and Secure Your Healthcare Organization
CISA Medical Device Advisories for Vulnerabilities in BD Products
The US Cybersecurity and Infrastructure Security Agency (CISA) has issued two medical device advisories regarding hard-coded vulnerabilities in certain BD Pyxis and Viper LT products. The flaws could be exploited to access or in some cases modify sensitive information. BD Pyxis is an automated medication dispensing system; BD Viper LT is an automated molecular texting system.
Note
- There are two vulnerabilities, CVE-2022-22765 – hard coded credentials which has a low attack complexity, is not remotely exploitable and has no known public exploits and CVE-2022-22766, which allows access to the underlying file system if the BD managed credentials were discovered. While fixes haven’t been released yet, mitigate the risks by limiting physical access to the devices, as well as ensuring the devices are properly segmented and traffic is monitored for inappropriate interaction. Make sure that the right staff are being alerted to updates from BD.
Read more in
- BD discloses hard-coded flaws impacting some Pyxis, Viper medical devices
- ICS Medical Advisory (ICSMA-22-062-01) BD Pyxis
- BD Pyxis™ Products – Hardcoded Credentials
- ICS Medical Advisory (ICSMA-22-062-02) BD Viper LT
- BD Viper LT™ system – Hardcoded Credentials
Logan Health Breach Compromised Patient and Employee Data
Logan Health Medical Center in Montana has notified more than 200,000 patients, employees, and business associates that their personal information was compromised following a file server breach. Logan Health became aware of suspicious activity in November 2021.
Note
- Notifications from this breach and other similar incidents have been delayed by using manual processes to verify information was accessed or otherwise released in contrast to declaring the entire dataset was compromised. Act now to capture exactly which systems have sensitive data to facilitate identification of affected information as as well as fine tune your recovery process. With the continued focus by attackers on healthcare systems, consider proactively obtaining identity monitoring services instead of waiting for notification that your information was previously compromised.
Read more in
Nvidia Data Stolen
Nvidia has acknowledged that its network was breached and data were stolen. The chipmaker said that the hackers stole proprietary data and employee credentials. The data have reportedly been leaked on the internet. The data thieves are demanding that Nvidia allow their graphics cards to mine cryptocurrencies faster; if the demand is not met, the thieves say they will release Nvidia source code.
Note
- We may not have heard the last from Nvidia regarding the breach. There are some leaks surfacing that may include certificate material (even if outdated) and source code. The demand to unlock the graphics card for mining is interesting. Nvidia implemented some restrictions and intentionally slowed some mining related operations as cards where purchased quickly by miners and none were left for Nvidia’s traditional customers: online gamers.
- The Lapsus$ gang claims they have 1TB Nvidia proprietary data and password hashes and leaked a 20GB document archive to support their claim. The attackers are asking to change Nvidia’s Lite Hash Rate (LHR) technology which enables the card to limit its use for crypto mining, making it harder to use compromised systems for this purpose. As the LHR source is claimed to be part of the exfiltrated data, and attackers hope someone will engineer a bypass to the rate restrictions, be vigilant and verify Nvidia firmware updates are genuine.
Read more in
- NVIDIA confirms data was stolen in recent cyberattack
- Nvidia says its ‘proprietary information’ is being leaked by hackers
- Cybercriminals who breached Nvidia issue one of the most unusual demands ever
Article: APIs increasingly used for account takeover
New research covered by Security Boulevard reveals how APIs are increasingly favored by developers: they are becoming the development tool of choice, with data indicating that of the 21.1 billion application requests analyzed, nearly 70% of them were API-based.
Unfortunately, APIs are also the favorite attack vector for adversaries: correspondingly, the data indicated that 80% of blocked attacks were targeting APIs. In particular, the research revealed a 62% increase in account takeovers (ATO) using login APIs. Most notably, the attacks increasingly focused on account logins and registrations. Common examples were attacks against gift card sites, such as card and points theft, and semi-automated large-scale attacks against loan sites.
The report also revealed a 178% increase in API-based content scraping. Although apparently benign, large-scale content scraping can lead to revenue loss for the organizations that own that data. Typical examples of data scraping included inventory pricing, stock levels, market data, and social media data.
An interesting observation made in the article is that well-documented and discoverable APIs (either by virtue of OpenAPI definitions or GraphQL endpoints) can actually facilitate attacks. No longer do attackers have to enumerate API endpoints, but instead can easily leverage the definitions. However, this does not definitely mean that APIs should not be documented, but perhaps some consideration is needed on the intended (and unintended) audience and how exactly to reach them.
The article provides the following sound recommendations for improving API security:
- API discovery and inventory tracking: Ensure that your organization maintains an accurate inventory of APIs to avoid exposing unnecessary attack surface, and make sure all APIs have assigned owners.
- API risk assessment and remediation: Assess APIs for common weaknesses and drive remediating or mitigating vulnerabilities.
- Native, inline protection for attacks and vulnerability exploits: Use a defense-in-depth approach by leveraging API firewalls and gateways for inline protection.
Review: “Hacking APIs” by Corey Ball
My last few evenings have been spent reading “Hacking APIs” by Corey Ball, available now as early access form from NoStarch Press. I have no doubt this book is destined to become the industry handbook for API security aficionados in years to come, and would recommend this to readers of this newsletter regardless of experience.
The book tackles a broad topic primarily from the perspective of a pentester but makes few assumptions on prior knowledge. I certainly learned a great deal about API discovery, bug bounty programs, and disclosure. The chapters on how to evade standard controls and countermeasures were particularly interesting — for defenders, this should prove quite eye-opening indeed!
On a personal level, I found myself inspired to get a lot more hands-on with APIs, hopefully there is a disclosure with my name on it soon.
Following on from the popular best practice for API authentication and authorization featured last week, we have a quick guide on how to use Postman to implement the OAuth 2.0 authorization code grant flow.
The guide describes how to use Postman acting as a client to obtain an authorization code, and how then to use the code to gain access and refresh tokens. The popular Keycloak server acts as the authorization server in this example.
This is a great guide to help developers understand this important OAuth 2.0 flow in a very hands-on manner, and I look forward to the next article describing the PKCE extension to this flow.
Guide: Comprehensive guide to API documentation
Good API documentation is essential in enabling downstream API consumption by end users. Well-documented APIs also enable effective security implementations: for example, illustrative code samples and associated documentation can guide end-users to correctly implement authentication workflows.
I’ve found myself frequently referring to the excellent and comprehensive guide by Tom Johnson on a variety of API documentation topics. This is worth bookmarking for anyone engaged in writing or documenting APIs.
This is what they tell me cyberwar looks like.
Sure, the wording stinks, but it’s hard to find another description for the kinds of worm-like data-wiping attacks we’ve seen linked to kinetic war currently underway in Ukraine. Let’s try to catch up:
- ESET has done a fantastic job documenting the data-wiper attacks hitting Ukraine. The latest report discusses a second wiper with worm-spreading capabilities and even a ransomware smokescreen.
- Microsoft says it has seen evidence that civilian digital targets are being hit in the Ukraine attacks and says these “raise serious concerns under the Geneva Convention.”
- SentinelLabs follows up with its own report on the wiper and decoy ransomware component.
- Symantec says the disk-wiping attacks preceded the Russian invasion.
- The U.S. government’s cybersecurity agency CISA has released IOCs to help defenders hunt for signs of these destructive payloads.
Meanwhile, Iran and China…
Speaking of apex-level nation-state malware activity, Symantec has found a super-stealthy backdoor linked to a Chinese APT actor first seen in 2012. The Symantec report on Daxin confirms the Chinese have invested in a command-and-control mechanism similar to Regin.
MIT Technology Review’s Patrick Howell O’Neill looked at the paper and concluded it was China’s work to build a one-of-a-kind cyber espionage behemoth to last.
The skinny: “While Beijing’s hackers were once known for simple smash-and-grab operations, the country is now among the best in the world thanks to a strategy of tightened control, big spending, and an infrastructure for feeding hacking tools to the government that is unlike anything else in the world.”
The staggering ransomware wealth transfer.
From vx-underground on Twitter (take with multiple grains of salt):
The Conti ransomware leaks have unveiled Conti’s primary Bitcoin address. From April 21st, 2017 – February 28th, 2022 Conti has received 65,498.197 BTC. That is 2,707,466,220.29 USD.
In April last year, Emsisoft estimated that ransomware accounted for $74,632,036,933 moving from western countries to Russian criminal gangs.
Here’s another spicy Twitter thread on the Conti leaks suggesting links between Russian law enforcement and ransomware criminals.
Remember Log4Shell?
The SANS Internet Storm Center is reporting that attackers have lost interest in exploiting the Apache Log4j vulnerability. Here’s data from the ISC sensors:
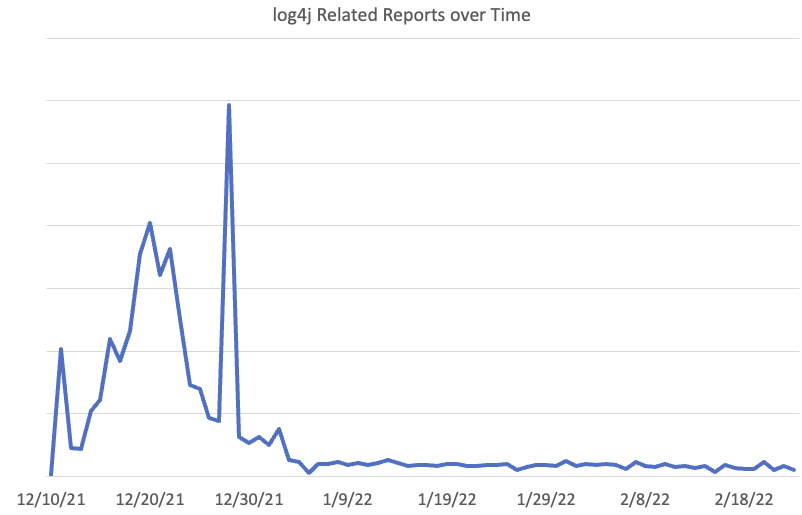
Must-see research projects.
- BrokenPrint documents a pre-auth stack-based overflow vulnerability found and exploited in Netgear routers and modems.
- Stairwell’s Steve Miller on building a labeled malware corpus for YARA testing.
- Chinese security vendor Pangu Lab has published a 56-page technical report (PDF) showing its work researching Equation Group malware.
Hacking things.
- Researchers at Tel Aviv University expose the cryptographic design and implementation of Android’s Hardware-Backed Keystore in Samsung’s Galaxy S8, S9, S10, S20, and S21 flagship devices. The paper provides a detailed description of the cryptographic design and code structure, and severe design flaws.
- Wired’s Lily Hay Newman with a softball piece on Intel’s iSTARE, a team that looks for critical flaws before CPU chips to to production. (Non-paywall archive).
- Kolide’s Jason Meller asks: Is Grammarly a keylogger?
CISA and FBI Warning on HermeticWiper and WhisperGate
In a joint cybersecurity advisory, the FBI and the US Cybersecurity and Infrastructure Security Agency (CISA) provide technical details about the WhisperGate and HermeticWiper malware strains that have been used against organizations in Ukraine. The advisory cautions that “Further disruptive cyberattacks against organizations in Ukraine are likely to occur and may unintentionally spill over to organizations in other countries.” The advisory also includes a list of mitigations.
Note
- Spend 5 minutes hunting for the specific IOCs mentioned (file hashes and the like). The rest of the day: Try to understand the infection chain and verify how you would detect similar techniques in your environment. Look for gaps in visibility (host or network-based logging).
- Unlike other malware, focused on quietly stealing IP or PII, this kind of incident is a DR/BCP issue that requires strategic thinking about continuity (how do we keep payroll, AR/AP, logistics, sales going) and recovery (access offline backups and start restoring business processes). Backups and backup applications are themselves targets for destruction/encryption, unlike in other critical incidents, natural or of the cyber variety.
- Attacks targeting Ukraine have featured disk wipers of one form or another as far back as 2013. The issue here is that attacks are spilling over into other areas, not just including Ukrainian supporters, but also in response to attacks on behalf of Ukraine, such as Anonymous promises, so we all need to brush up on our mitigations to make sure nobody just checked the box. Add examining systems for atypical malware delivery paths, resiliency for common points of failure, such as your SAN or network switches, robust physical and logical access controls, active monitoring and response to your list of services to verify are up to the task at hand.
- We learned about similar disruptive attacks and how to mitigate them after the North Korean attack on Sony. Here we have another opportunity to learn and be prepared for future attacks. Kudos for an actionable advisory from CISA and FBI.
Read more in
- Destructive Malware Targeting Organizations in Ukraine
- CISA, FBI to US firms: prepare for Ukraine wipers
- CISA, FBI warn US orgs of WhisperGate and HermeticWiper malware
- CISA and FBI warn of potential data wiping attacks spillover
SpaceX Starlink Satellite Service is Now Active in Ukraine
In response to requests from Ukrainian leaders, SpaceX has activated its Starlink satellite service in Ukraine. The organization has also sent Starlink user terminals to Ukraine.
Note
- Starlink does provide high bandwidth connectivity, but in its current design still requires ground stations in the same region as the user. But Starlink’s ability to provide easy to use ad-hoc connectivity has proven to be invaluable during various disasters in the past. Some pointed out that the terminals may be located by their EM emissions. I am not sure how practical that is, but the terminal can also be placed some distance from the user.
- Starlink has about 2,200 satellites in low-earth-orbit and is designed as a high-bandwidth, low-latency alternative to broadband. The terminals arrived about 48 hours after Elon promised them for free to Ukrainian users who getting about 137mbps download speeds. When available, Starlink’s premium option will offer speeds between 150 and 500mbps download, with 20-40mbps upload speeds.
- Good stuff to help Ukraine is popping up as in this example.
- I have been testing the Starlink service and it is a game changer for areas that do not have reliable Internet service providers. The equipment only requires one power outlet meaning you can have Internet connectivity from a backup battery or generator even if the entire area is out of power.
Read more in
- Ukraine asks Musk for Starlink terminals as Russian invasion disrupts broadband
- Elon Musk activates Starlink to help keep Ukraine’s internet up and running
- Elon Musk says SpaceX’s Starlink satellites now active over Ukraine
Viasat Says European Broadband Outages Caused by Cyberattack
Satellite communications company Viasat says that a cyberattack has been causing broadband outages across eastern Europe. The attack appears to have begun on February 24. The investigation into the situation is ongoing.
Note
- In Germany, about 6,000 wind turbines lost connectivity. These wind turbines used Ka-SAT satellite connections and the event may be related to the Viasat outage. At this point, the root cause is unclear. Some reports also suspect a rogue firmware update to the turbines network equipment. But while satellite connectivity is less susceptible to ground based issues (see SpaceX story), it can be very difficult to recover if geographically dispersed systems like Wind turbines (or the satellite itself) are affected.
- This is a good time to investigate alternate or fail-over ISP options. If possible, have the secondary ready to go, including testing, prior to needing it. Determine what capabilities will operate over the fail-over connection to ensure that even with a change in bandwidth the business remains viable, for example the Starlink terminals in the Ukraine are getting 137mbps download speeds.
- Viasat is also a satellite provider, like Starlink. SpaceX should keep an eye on this attack and learn from the competitors.
Read more in
- Viasat says ‘cyber event’ is causing broadband outages across Europe
- Satellite giant Viasat probes suspected broadband cyberattack amid Russia fears
Toyota Suspends Operations at Multiple Plants Following Supply Chain Cyberattack
Toyota has halted operations at one-third of its factories after a supplier was reportedly hit with a cyberattack. Kojima Industries makes multiple vehicle components for Toyota. In all, Toyota has suspended operations at 14 plants. The company did not speculate about how long the downtime will last.
Note
- All our supply-chains have been very challenged as of late and hacking a key supplier doesn’t help it recover. In some cases you may have no alternative but to “stop and wait” for a supplier to recover. Examine backup sources, particularly for key suppliers, to include startup activities and make recorded decisions about the viability of utilizing them, and the associated processes.
- If corporate executives weren’t re-evaluating their Just-In-Time, zero inventory, single-point-of-failure supply chains for resilience, of the physical and digital (is there a difference anymore?), then perhaps it’s that time of the century.
- When reviewing incident response plans many organisations tend to focus their response based on their own company assets being compromised. However, in today’s interconnected world, it’s good practice to review your Incident Response and Business Continuity Plans to include the impacts incidents within your supply chain.
- This is not the first supply chain attack you have heard of. These are tougher to red team (play devil’s advocate) but with proper planning, you can tabletop and perform technical exercises to test, measure, and improve your resilience to supply chain attacks.
Read more in
- Toyota shuts down all Japanese production after supplier is hacked
- Toyota supplier reports cyberattack that halts production across Japan
- Toyota to Close Japan Plants After Suspected Cyberattack
- Toyota halts production after reported cyberattack on supplier
- Toyota suspends domestic factory operations after suspected cyber attack
HHS Office for Civil Rights Director Tells Healthcare Providers to Strengthen Cyber Posture
In a blog post, US Department of Health and Human Services Director for Office for Civil Rights (OCR) Lisa Pino urges all HIPAA-covered entities to improve their cyber posture in 2022. Pino notes that rather than focusing only on electronic health records (EHRs), “risk management strategies need to be comprehensive in scope. You should fully understand where all electronic protected health information (ePHI) exists across your organization – from software, to connected devices, legacy systems, and elsewhere across your network.” The post includes suggested best practices and additional guidance and resources.
Note
- Really no new information here, but the Director’s blog post does emphasize basic security hygiene and training/education. However, in emphasizing risks assessment, the post includes a link to the old HHS Security Risk Assessment application which expects the user of the tools to enter voluminous IT asset and vendor information and make an assessment of the likelihood of attack success and the impact of successful attacks. This old approach of multiplying two imaginary numbers to create a third imaginary number creates many pages of documentation but nothing useful in actually identifying or reducing critical risks.
- The last two years have put healthcare providers on notice for attacks. The trick is providing actionable guidance which is easy to consume. The HHS includes recommendations we should all be following irrespective of the data sensitivity, from knowing where your data is, making sure it’s securely backed up in an immutable form, judicious application of patches and updates, to relevant, updated, user training. They also include links to resources for more information which can help you deep dive when planning to address any of these recommendations.
Read more in
- Improving the Cybersecurity Posture of Healthcare in 2022
- OCR director urges providers to strengthen cyber posture, risk management
Zabbix Flaws Added to CISA’s Known Exploited Vulnerabilities Catalog
The US Cybersecurity and Infrastructure Security Agency (CISA) has added two Zabbix vulnerabilities to its Known Exploited Vulnerabilities catalog. Zabbix released fixes for the authentication bypass and improper access control vulnerabilities in December 2021. CISA has given federal civilian agencies until March 8 to install the patches.
Note
- If you’re using Zabbix with SAML SSO authentication enabled, you are potentially vulnerable. With the pressure to “MFA all the things” using SAML with an IDP which supports MFA, SSO, etc. across your organization is the easy button, but this also necessitates being on the lookout for security flaws in SAML implementations. This also means that mitigations such as disabling SAML authentication are not viable. In this case CVE-2022-23131, unsafe client-side session storage, has a CVSS score of 9.1, Zabbix has released patches, update to either 5.4.9rc2, 6.0beta1 or 6.0 (plan) as earlier patches didn’t fully address the issue.
- IT and cybersecurity tools can be exploited, especially when they’re approved and deemed safe. Monitoring with read rights is one thing, write is another… From the Zabbix page www.zabbix.com/features “Execute a script directly from a dashboard and remediate an issue or display additional information.”
Read more in
- Zabbix vulnerabilities added to CISA catalog
- CISA Adds Two Known Exploited Vulnerabilities to Catalog
- Unsafe client-side session storage leading to authentication bypass / instance takeover via Zabbix Frontend with configured SAML (CVE-2022-23131)
FCC Notice of Inquiry Seeks Comments on Border Gateway Protocol Security
In a Notice of Inquiry, the US Federal Communications Commission (FCC) says it is “seek[ing] comment on vulnerabilities threatening the security and integrity of the Border Gateway Protocol (BGP).” The notice says that “BGP’s initial design, which remains widely deployed today, does not include security features to ensure trust in the information that it is used to exchange.”
Note
- This should increase the support for updates to BGP, turning BGP best practices into requirements. If you’re wrestling with BGP security issues, take a moment to contribute. In the meantime, make sure you’re following best common practices with BGP to reduce risks of route hijacking or other disruptions.
- This talk by Wim Remes in 2015 is a good primer on BGP for security professionals.
www.blackhat.com: Internet Plumbing for Security Professionals: The State of BGP Security (PDF) - Richard Clarke was complaining about BGP in the Clinton Administration.
Read more in
CISA Warns of SCADA Flaws in Schneider Products
The US Cybersecurity and Infrastructure Security Agency (CISA) has published an advisory warning of multiple vulnerabilities affecting Schneider Electric’s Easergy medium voltage protection relays. The flaws could be exploited to cause denial-of-service conditions, reboot devices, disclose device credentials, or allow attackers to gain control of vulnerable devices. Schneider addressed the flaws in updates released on January 11, 2022.
Note
- Right now ICS systems are a prime target as attackers are focusing on disrupting services not only in the Ukraine, but also areas perceived to be supporting or of benefit to Ukraine. The flaws addressed include two classic buffer overflows (CVE-2022022725 and CVE-2022-22723) as well as hard coded credentials (CVE-2022-22722). Fix by applying the updates or at least disabling or restricting the GOOSE service. Additionally make sure that your ICS systems are isolated, not exposed to the Internet only communicating with authorized services and users. Scan all media before introduction to the isolated network, don’t allow remote access to directly terminate to the isolated network. Check the CISA alert for additional mitigations.
Read more in
- ICS Advisory (ICSA-22-055-03) Schneider Electric Easergy P5 and P3
- CISA Warns of High-Severity Flaws in Schneider and GE Digital’s SCADA Software
Microsoft Says FoxBlade Malware Infected Ukrainian Networks
In a blog post, Microsoft President and Vice-Chair Brad Smith writes that researchers with Microsoft Threat Intelligence Center recently detected cyberattacks using a new strain of malware, dubbed FoxBlade, against Ukrainian networks. Microsoft notified the Ukrainian government about the malware and offered technical advice. In the blog, Smith notes “These recent and ongoing cyberattacks have been precisely targeted, and we have not seen the use of the indiscriminate malware technology that spread across Ukraine’s economy and beyond its borders in the 2017 NotPetya attack.”
Note
- Microsoft has also decided to follow the EU’s decision to block Russian state sponsored disinformation outlets from their social networks, app store and search engine. Facebook, Instagram, YouTube and Tik Tok have taken similar steps. This is a complex area but as the disinformation attacks during the recent US presidential election show, those and other similar commercial services need to have the processes and capabilities to do this kind of filtering. Many legislative and regulatory efforts are underway to force them to do so, but as we have seen threats move faster and always will.
- Note RT is a brand of TV-Nososti, founded by the Russian state-owned news agency RIA Novosti. It is listed by Putin as one of the core organizations of strategic importance to Russia. FoxBlade allows systems to be used for a DDoS attack, unbeknownst to their owner. Microsoft Defender has been updated with signatures to detect and block FoxBlade. Make sure your endpoint protection solution includes these protections. Microsoft is also removing RT’s apps from their app store, blocking ads from RT and Sputnik sources and de-ranking their sites in Bing such that unless you’re explicitly looking for them they won’t appear in your search results.
Read more in