The latest Microsoft AZ-900 Azure Fundamentals certification actual real practice exam question and answer (Q&A) dumps are available free, which are helpful for you to pass the Microsoft AZ-900 Azure Fundamentals exam and earn Microsoft AZ-900 Azure Fundamentals certification.
Question 781
You need to collect and automatically analyze security events from Azure Active Directory (Azure AD).
What should you use?
*A. Azure Sentinel
B. Azure Synapse Analytics
C. Azure AD Connect
D. Azure Key Vault
Question 782
Your Azure environment contains multiple Azure virtual machines.
You need to ensure that a virtual machine named VM1 is accessible from the Internet over HTTP.
Solution: You modify a DDoS protection plan.
Does this meet the goal?
A. Yes
*B. No
Explanation
DDoS is a form of attack on a network resource. A DDoS protection plan is used to protect against DDoS attacks; it does not provide connectivity to a virtual machine.
To ensure that a virtual machine named VM1 is accessible from the Internet over HTTP, you need to modify a network security group or Azure Firewall.
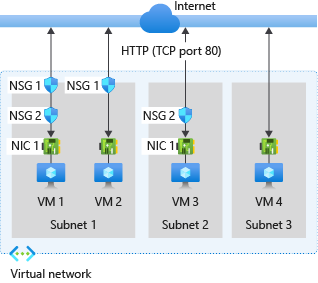
Question 783
Your Azure environment contains multiple Azure virtual machines.
You need to ensure that a virtual machine named VM1 is accessible from the Internet over HTTP.
Solution: You modify a network security group (NSG).
Does this meet the goal?
*A. Yes
B. No
Explanation
A network security group works like a firewall. You can attach a network security group to a virtual network and/or individual subnets within the virtual network. You can also attach a network security group to a network interface assigned to a virtual machine. You can use multiple network security groups within a virtual network to restrict traffic between resources such as virtual machines and subnets.
You can filter network traffic to and from Azure resources in an Azure virtual network with a network security group. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources.
In this question, we need to add a rule to the network security group to allow the connection to the virtual machine on port 80 (HTTP).
Question 784
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Statement 1: You can create custom Azure roles to control access to resources: Yes
Statement 2: A user account can be assigned to multiple Azure roles: Yes
Statement 3: A resource group can have the Owner role assigned to multiple users: No
Question 785
To complete the sentence, select the appropriate option in the answer area.
After you create a virtual machine, you need to modify the __________ to allow connections to TCP port 8080 on the virtual machine.
Answer Area:
*A. network security group (NSG)
B. virtual network gateway
C. virtual network
D. route table
Explanation
When you create a virtual machine, the default setting is to create a Network Security Group attached to the network interface assigned to a virtual machine.
A network security group works like a firewall. You can attach a network security group to a virtual network and/or individual subnets within the virtual network. You can also attach a network security group to a network interface assigned to a virtual machine. You can use multiple network security groups within a virtual network to restrict traffic between resources such as virtual machines and subnets.
You can filter network traffic to and from Azure resources in an Azure virtual network with a network security group. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources.
In this question, we need to add a rule to the network security group to allow the connection to the virtual machine on port 8080.
Question 786
You plan to deploy several Azure virtual machines.
You need to control the ports that devices on the Internet can use to access the virtual machines.
What should you use?
*A. a network security group (NSG)
B. an Azure Active Directory (Azure AD) role
C. an Azure Active Directory group
D. an Azure key vault
Explanation
A network security group works like a firewall. You can attach a network security group to a virtual network and/or individual subnets within the virtual network. You can also attach a network security group to a network interface assigned to a virtual machine. You can use multiple network security groups within a virtual network to restrict traffic between resources such as virtual machines and subnets.
You can filter network traffic to and from Azure resources in an Azure virtual network with a network security group. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources.
Question 787
Your company plans to automate the deployment of servers to Azure.
Your manager is concerned that you may expose administrative credentials during the deployment.
You need to recommend an Azure solution that encrypts the administrative credentials during the deployment.
What should you include in the recommendation?
*A. Azure Key Vault
B. Azure Information Protection
C. Azure Security Center
D. Azure Multi-Factor Authentication (MFA)
Explanation
Azure Key Vault is a secure store for storage various types of sensitive information. In this question, we would store the administrative credentials in the Key Vault. With this solution, there is no need to store the administrative credentials as plain text in the deployment scripts.
All information stored in the Key Vault is encrypted.
Azure Key Vault can be used to Securely store and tightly control access to tokens, passwords, certificates, API keys, and other secrets.
Secrets and keys are safeguarded by Azure, using industry-standard algorithms, key lengths, and hardware security modules (HSMs). The HSMs used are Federal Information Processing Standards (FIPS) 140–2 Level 2 validated.
Access to a key vault requires proper authentication and authorization before a caller (user or application) can get access. Authentication establishes the identity of the caller, while authorization determines the operations that they are allowed to perform.
Question 788
This question requires that you evaluate the bold text to determine if it is correct. Review the bold text. If it makes the statement correct, select “No change is needed”. If the statement is incorrect, select the answer choice that makes the statement correct.
Azure Key Vault is used to store secrets for Azure Active Directory (Azure AD) user accounts.
A. No change is needed
B. Azure Active Directory (Azure AD) administrative accounts
C. Personally Identifiable Information (PII)
*D. server applications
Explanation
Centralizing storage of application secrets in Azure Key Vault allows you to control their distribution. Key Vault greatly reduces the chances that secrets may be accidentally leaked. When using Key Vault, application developers no longer need to store security information in their application. Not having to store security information in applications eliminates the need to make this information part of the code. For example, an application may need to connect to a database. Instead of storing the connection string in the app’s code, you can store it securely in Key Vault.
Question 789
You have an Azure environment that contains 10 virtual networks and 100 virtual machines.
You need to limit the amount of inbound traffic to all the Azure virtual networks.
What should you create?
A. one application security group (ASG)
B. 10 virtual network gateways
C. 10 Azure ExpressRoute circuits
*D. one Azure firewall
Explanation
You can restrict traffic to multiple virtual networks with a single Azure firewall.
Azure Firewall is a managed, cloud-based network security service that protects your Azure Virtual Network resources. It’s a fully stateful firewall as a service with built-in high availability and unrestricted cloud scalability.
You can centrally create, enforce, and log application and network connectivity policies across subscriptions and virtual networks. Azure Firewall uses a static public IP address for your virtual network resources allowing outside firewalls to identify traffic originating from your virtual network.
Question 790
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Statement 1: You can associate a network security group (NSG) to a virtual network subnet: Yes
Statement 2: You can associate a network security group (NSG) to a virtual network: No
Statement 3: You can associate a network security group (NSG) to a network interface: Yes